A Key Concept in Information Systems, Term Paper Example
Introduction
Information is believed to be a key asset of any business today. No matter how exactly the business operates, disclosure of information to people that are not authorized to make changes to it or utilize it will be costly. The disclosure of information is a serious blow to any company, which may result in loyal customers’ loss, downgrade of the business’s reputation and image in the market, and considerable loss of business opportunities.
In this context, information security, which basically means “protection of information and its critical characteristics (…) through appropriate deployment of products, people, procedures, and policies”, becomes a critical concern (Vlajic, 2010). In any organization, information security goals comprise protection of data, ability to maintain safe operations of applications within internal IT systems in this organization, and protection of the company’s ability to adequately function on the external level. Based on the need of relevant balance between protection and access, the Committee on National Security Systems (CNSS) adopted a model of information security which serves an evaluation standard for information systems security. The model was represented by the McCumber Cube and fixed in the CNSS document NSTISSI (National Standard for Information Systems Security Professionals) No. 4011.
The McCumber Cube (also known as the McCumber Model) is defined as detailed information-centric model applied to computer security (to its evaluation and establishment) (Whitman & Mattord, 2010, p.15). The concept behind this similar to Rubik’s cube is that “to develop a secure system, one must consider no only key security goals (CIA) but also how these goals relate to various states in which information resides and full range of available security measures” (Vlajic, 2010) (See Figure 1).
Figure 1. McCumber Cube
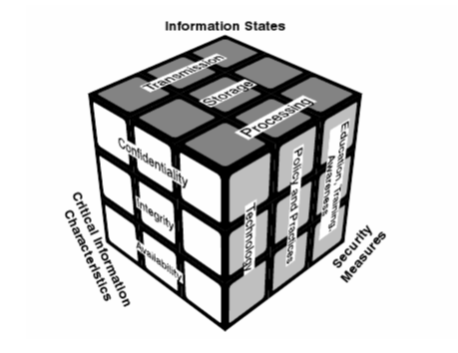
(McCumber, 2005 in Vlajic, 2010)
Importantly, the McCumber Cube centers around three dimensions of information. These are Information States, Critical Information Characteristics, and Security Measures. As it can be seen from the Figure 1, each dimension has three aspects. If coupled, these dimensions bring a three-dimensional cube, with each dimension on the cube’s axis (McCumber, 2004). Each of 27 cells in the McCumber Cube represents one area which has to be addressed in order to make an information system secure. For example, intersection between the following dimensions integrity, technology, and storage shows the need to utilize technology in order to protect data integrity while in storage (Figure 2). On the basis of this model, the following solution may be reached: to implement a host intrusion system which will alert the administrator once a critical file gets modified (Vlajic, 2010).
Figure 2. McCumber Cube Dimensions
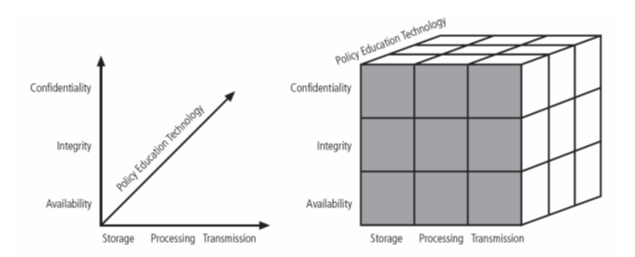
(Vlajic, 2010)
This paper explores a selected concept of information systems infrastructure – the McCumber Cube. First, it focuses on the origin and history of the model. Second, it discusses the place and use of the McCumber Cune in information security today. Third, it describes the advantages and disadvantages of the McCumber Cube. Then, the future of the model is discussed with reference to existing trends of its application. The paper concludes with the summary of findings from a variety of pertinent sources.
McCumber Cube: Origin and History
The goals that computer security aspires to achieve along with information states and safeguards are known to make a framework of the McCumber Cube, which serves a tool for guiding the overall process of setting up and assessing different information security programs. In brief, the idea behind the McCumber Cube is that organizations should take into consideration the way a range of factors relate as well as impact one another (Lock & Philander, p.38).
This comprehensive model of computer security that has grown to be a widely recognized standard for information security systems was introduced by a risk and security professional John McCumber back in 1991. As it can be learnt from the Proceedings of the 14th National Computer Security Conference (October, 1991), the McCumber Cube was designated as “a comprehensive model for the security of information systems and functions as an assessment, systems development, and evaluation tool.” (McCumber, 1991). Its key unique characteristic was that it acknowledged information rather than technology as the ground of security efforts. Hence, its application is perceived as universal and generally unrestricted by organizational differences (McCumber, 1991).
As for John McCumber, he is a retired officer of US Air Force, who served in US Defense Information Systems Agency and at the Pentagon during the Persian Gulf War as a Joint Staff. These days McCumber is involved in Semantec Corporation and has a position of a Professorial Lecturer in Information Security as a part of the faculty at The George Washington University in Washington, DC. McCumber is also known to be a monthly columnist as well as a technical editor at Security Technology and Design journal; he wrote and published a book Assessing and Managing Security Risk in IT Systems: a Structured Methodology (McCumber, 2004). McCumber’s current research interests encompass leading state-of-the-art government initiatives on cyber-security; he also provides consultations and guidance to both state and local CISOs and CIOs in different aspects of cyber security, data privacy, data availability, and data management (Keynotespeakers.com, 2013).
McCumber Cube: Current Use and Attitude
Introduced back in 1991, the McCumber Cube has been widely used by IT security practitioners across the globe. It has been extensively utilized over this extended period of time despite the fact that dramatic changes have taken place within the field of technology. This is attributed, first of all, to the model’s focus on information, not on technology, in combination with “a model structure of cognitive simplicity that allows human beings the ability to organize and reason about information at the proper level of abstraction.” (Endicott-Popovsky et al, 2012).
Today the model developed by John McCumber back in 1991 is widely appreciated and used to build new frameworks and models that will meet the demands of developments in the sphere of information systems and information security. For instance, it is one of major concepts in Information/Enterprise Assurance Management, in modelling e-business security (Nachtigal & Mitchell, n.d., ), in Risk Assessment, etc (Yamaguchi, 2010). For instance, in Yamaguchi (2010), the McCumber model is used within the combination of structured and unstructured techniques to make up a threat elicitation methodology within the model driven architecture framework: McCumber’s Cube + Miller’s (Rockwell Corp) process + Price’s (2008) model + MICROSOFT’s STRIDE + particular RA methodology (e.g. Octave) (Yamaguchi, 2010). Figure 3 shows OCC Cubes to extend the McCumber (on the basis of McCumber 2004, in Yamaguchi, 2010).
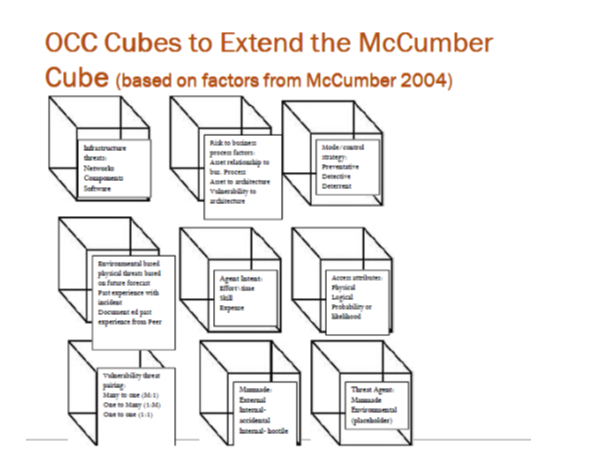
Also, it constitutes the basis of the Information Assurance Model (Maconachy, Schou, Ragsdale, and Welch, 2001) (Figure 4).
Figure 4. Information Assurance Model
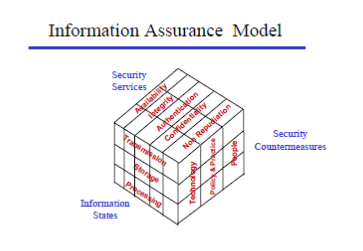
Hafiz & Johnson (2006) have based their security patterns on the McCumber Cube. Within three central patterns, separate viewpoints are addressed, with reference to different factors. See Table 1. Table 1. Security patterns classification based on the McCumber Cube (Hafiz & Johnson, 2006, p.18).
| Authenticator. (Technology, Transmission, Confidentiality).
Authorization. (Technology, Transmission, Confidentiality). Checkpointed System. (Technology, Processing, Availability). Compartmentalization. (Technology, Processing, Confidentiality). Defense In Depth. (Technology, Storage | Processing | Transmission, Confidentiality | Integrity | Availability). Full Access With Errors. (Technology, Processing, Confidentiality). Minefield. (Technology, Storage | Processing | Transmission, Confidentiality). Policy Enforcement Point. (Technology, Transmission, Confidentiality). Replicated System. (Technology, Storage, Integrity | Availability). Secure Pre-forking. (Technology, Processing, Confidentiality). Single Access Point. (Technology, Transmission, Confidentiality). Single Threaded Facade. (Technology, Processing, Confidentiality). Subject Descriptor. (Technology, Processing, Confidentiality). Trust Partitioning. (Technology, Processing, Confidentiality). |
McCumber Cube: Advantages and Disadvantages
Whereas the McCumber’s model has been often criticized for lack of accurate recipes of protection and for being too primitive, it is recognized to be theoretically useful. The McCumber Cub itself is a good basic tool for IT beginners and may be effectively used for educational purposes. Its major advantage, as many practitioners admit, is that it demonstrates that information is not constrained only by technical measures.
Tomhave (2006) observes that theoretically the McCumber Cube is a model that meets the characteristics of being abstract, technology-independent, as well as conceptual. It captures “the relationship between the disciplines of communications and computer security, without the constraints of organizational or technical changes.” (Tomhave, 2006, p.16) Hence, it may be utilized for other fields beyond information security (for instance, physical security) having to undergo few or no modifications of the basic tenets. In addition, the advantage of the McCumber model is its avoidance of going into details with reference to implementation, for example with large practice statements. Thus, it is recognized to be useful for understanding computer security, which is a highly complex topic, in a way that is both concise and abstract. To add, focus on information enables application to many other dimensions apart from computer security with ease. Also, a high-level framework, the McCumber Cube has proved valuable for making an assessment of an organization to aid in focusing resources (Tomhave, 2006, p.16).
On the other hand, As Tomhave notes, the fact that the McCumber does not supply detailed implementation moments is its disadvantage (Tomhave, 2006, p.26). It means that in order to benefit from the model, one should first of all understand it and only then translate this acquired understanding into a task or objective that is achievable. In this context, selling the concept of the MCumber Cube may either be successful or fail. It depends on the senior management’s capacity to grasp the whole picture that is being presented.
Future of McCumber Cube
Just as the idea behind the model is to push back the progress of security which is perceived as an art along with supporting it with some structured methodology which could function independent of evolution in the sphere of technology, the McCumber Cube framework has been widely used since the time it was introduced back in 1991. Its application is most likely to persist in provision of high quality security training and security education. The findings of research by Endicott-Popovsky et al (2012) makes it possible to predict that the model will be used in future due its ability to arrange and reason about information on an adequate abstraction level. Hence, its widespread pedagogical use may be predicted. To illustrate, Endicott-Popovsky et al provide a recently developed model for a secure coding workshop – an extenson of the McCube model – for those who teach information security – Asset Protection Model (Figure 5) (Endicott-Popovsky et al, 2012, p. 28).
Figure 5. Asset Protection Model Developed as Extension of McCumber Cube
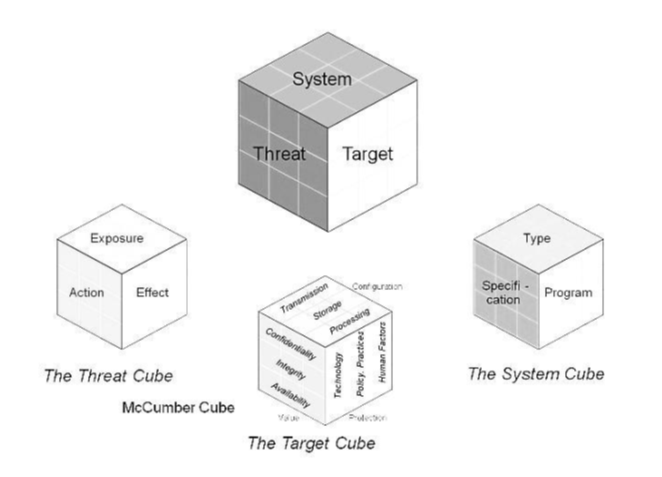
The model developed by McCumber is likely to be use din future judging by a number of its extension appearing these days. For example, to achieve a better quality of system risk evaluation and provide a generally more discrete identification of required countermeasures to defend some network against particular attack types an extension has been developed by Sean Price. To complement the classical cube, Price has added attacks to McCumber’s equation:
“ATTACK + Information State + Countermeasures -> Security Goal”.
Price’s final version of the suggested extension is as follows (Malta Info Security, “Extension to the McCumber Cube”):
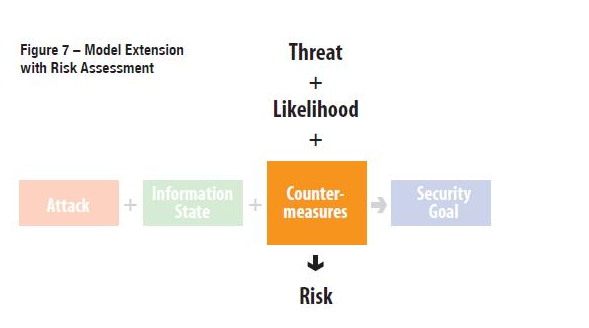
Overall, the McCumber cube is likely to be used in future due to its independence of technology, focus on information, comprehensive coverage, reduced commitment to resources, and ease of application and accessibility (“Review: McCumber Cube Methodology). It has already been referred to as a classical methodological structure in information security. As a part of newer modifications, the McCumber Cube continues to guide the area of information security. As along as modern business involves computer data operations, networking, information management, etc the information security will remain a critical issue. The McCumber Cube offers a basic comprehensive model of information security, hence will serve the foundation for new models that will be developed in future.
Conclusion
In summary, the McCumber’s Cube developed back in 1991 by a risk and security professional John McCumber constitutes the basis of CNSS Security Model. It is a comprehensive information security model that is widely used as the basis of numerous models within the model driven architecture framework of information security. Its pedagogical use is also widely documented. The McCumber Cube is a basic comprehensive model of information security, so it will serve the foundation for new models that will emerge in future.
References
Endicott-Popovsky, B. et al (2012). Provisioning secure coding curricular resources: Toward robust software. Proceedings of the 16th Colloquium for Information Systems Security Education. Lake Buena Vista, Florida, June 11-13, 2012, p. 27-37.
“Extension to McCumber Cube” (N.d.). Malta Info Security. Retrieved from http://maltainfosec.org/archives/125-Extension-to-the-McCumber-Cube.html.
Hafiz, M. & Johnson, R. (2006). Security patterns and their classification schemes. Retrieved from http://www.munawarhafiz.com/research/patterns/secpatclassify.pdf.
Keynotespeakers.Com (2013) “John McCumber”. Retrieved from http://keynotespeakers.com/speaker_detail.php?speakerid=5290.
Lock & Philander (2009). FCS systems analysis and design L4. Pearson South Africa.
Maconachy, V., Schou, C., Ragsdale, D., & Welch, D. (2001). A model for information assurance: An integrated approach. Proceedings of the 2001 IEEE Workshop on Information Assurance and Security United States Military Academy, West Point, NY, 5-6 June. Retrieved from http://it210web.groups.et.byu.net/lectures/MSRW%20Paper.pdf.
McCumber, J. (2004). Assessing and managing security risk in IT systems: A structured methodology. Auerbach Publications.
Nachtigal, S. & Mitchell, C. Modelling e-business security using business processes. Retrieved from http://www.chrismitchell.net/mebsub.pdf.
“Review: McCumber Cube Methodology” (N.d.). Protect Your Bits: Information Security Journal for Security, Risk, Compliance Professionals. Retrieved from http://protectyourbits.wordpress.com/2009/10/05/review-mccumber-cube-methodology/.
Tomhave, B. (2006). The total Enterprise Assurance Management (TEAM) Model: A unified approach to information assurance management. Unpublished master thesis. The George Washington University, Washington, DC.
Vlajic, N. (2010). Introduction to information security. Retrieved from http://www.eecs.yorku.ca/course_archive/2010-11/F/4482/CSE4482_01_Introduction.pdf.
Whitman, M. & Mattord, H. (2010). Principles of information security. Cengage Learning.
Yamaguchi, K. Situational awareness of the Risk Assessment (RA) Process. Retrieved from http://www.asq509.org/ht/a/GetDocumentAction

Time is precious
don’t waste it!

Plagiarism-free
guarantee

Privacy
guarantee

Secure
checkout

Money back
guarantee






