 All papers examples
All papers examples
Disciplines

- MLA
- APA
- Master's
- Undergraduate
- High School
- PhD
- Harvard
- Biology
- Art
- Drama
- Movies
- Theatre
- Painting
- Music
- Architecture
- Dance
- Design
- History
- American History
- Asian History
- Literature
- Antique Literature
- American Literature
- Asian Literature
- Classic English Literature
- World Literature
- Creative Writing
- English
- Linguistics
- Law
- Criminal Justice
- Legal Issues
- Ethics
- Philosophy
- Religion
- Theology
- Anthropology
- Archaeology
- Economics
- Tourism
- Political Science
- World Affairs
- Psychology
- Sociology
- African-American Studies
- East European Studies
- Latin-American Studies
- Native-American Studies
- West European Studies
- Family and Consumer Science
- Social Issues
- Women and Gender Studies
- Social Work
- Natural Sciences
- Anatomy
- Zoology
- Ecology
- Chemistry
- Pharmacology
- Earth science
- Geography
- Geology
- Astronomy
- Physics
- Agriculture
- Agricultural Studies
- Computer Science
- Internet
- IT Management
- Web Design
- Mathematics
- Business
- Accounting
- Finance
- Investments
- Logistics
- Trade
- Management
- Marketing
- Engineering and Technology
- Engineering
- Technology
- Aeronautics
- Aviation
- Medicine and Health
- Alternative Medicine
- Healthcare
- Nursing
- Nutrition
- Communications and Media
- Advertising
- Communication Strategies
- Journalism
- Public Relations
- Education
- Educational Theories
- Pedagogy
- Teacher's Career
- Statistics
- Chicago/Turabian
- Nature
- Company Analysis
- Sport
- Paintings
- E-commerce
- Holocaust
- Education Theories
- Fashion
- Shakespeare
- Canadian Studies
- Science
- Food Safety
- Relation of Global Warming and Extreme Weather Condition
Paper Types

- Movie Review
- Essay
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- GCSE Coursework
- Grant Proposal
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- Essay
- GCSE Coursework
- Grant Proposal
- Interview
- Lab Report
- Literature Review
- Marketing Plan
- Math Problem
- Movie Analysis
- Movie Review
- Multiple Choice Quiz
- Online Quiz
- Outline
- Personal Statement
- Poem
- Power Point Presentation
- Power Point Presentation With Speaker Notes
- Questionnaire
- Quiz
- Reaction Paper
- Research Paper
- Research Proposal
- Resume
- Speech
- Statistics problem
- SWOT analysis
- Term Paper
- Thesis Paper
- Accounting
- Advertising
- Aeronautics
- African-American Studies
- Agricultural Studies
- Agriculture
- Alternative Medicine
- American History
- American Literature
- Anatomy
- Anthropology
- Antique Literature
- APA
- Archaeology
- Architecture
- Art
- Asian History
- Asian Literature
- Astronomy
- Aviation
- Biology
- Business
- Canadian Studies
- Chemistry
- Chicago/Turabian
- Classic English Literature
- Communication Strategies
- Communications and Media
- Company Analysis
- Computer Science
- Creative Writing
- Criminal Justice
- Dance
- Design
- Drama
- E-commerce
- Earth science
- East European Studies
- Ecology
- Economics
- Education
- Education Theories
- Educational Theories
- Engineering
- Engineering and Technology
- English
- Ethics
- Family and Consumer Science
- Fashion
- Finance
- Food Safety
- Geography
- Geology
- Harvard
- Healthcare
- High School
- History
- Holocaust
- Internet
- Investments
- IT Management
- Journalism
- Latin-American Studies
- Law
- Legal Issues
- Linguistics
- Literature
- Logistics
- Management
- Marketing
- Master's
- Mathematics
- Medicine and Health
- MLA
- Movies
- Music
- Native-American Studies
- Natural Sciences
- Nature
- Nursing
- Nutrition
- Painting
- Paintings
- Pedagogy
- Pharmacology
- PhD
- Philosophy
- Physics
- Political Science
- Psychology
- Public Relations
- Relation of Global Warming and Extreme Weather Condition
- Religion
- Science
- Shakespeare
- Social Issues
- Social Work
- Sociology
- Sport
- Statistics
- Teacher's Career
- Technology
- Theatre
- Theology
- Tourism
- Trade
- Undergraduate
- Web Design
- West European Studies
- Women and Gender Studies
- World Affairs
- World Literature
- Zoology
Wireless Security, How Secure Are We? Essay Example
Hire a Writer for Custom Essay
Use 10% Off Discount: "custom10" in 1 Click 👇
You are free to use it as an inspiration or a source for your own work.

This paper examines the importance of wireless security. It answers the critical question of : How secure are we with the wireless security applications we use? The paper is structured into four main parts: (1) The historical perspectives of wireless security and how this technology evolved (2) The types of wireless technology in force today and the functionality of same (3) The Pro’s and Con’s of Wireless security options and finally (4) The future technological direction of wireless security.
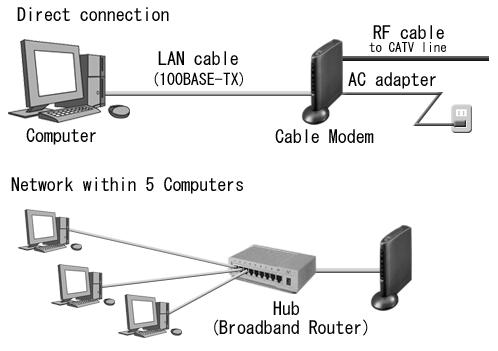
Figure 1: Old hard wired network
The Historical Perspective
The wireless network was designed to make enterprise networks have greater efficiency levels. These would be free of the previous hard wired Ethernet cabling systems (Fig 1 refers). This dispensing with the need for cabling, wall switches and installation of network jacks. There always used to be the problems of too few network jacks when you needed them. In particular in the meeting and teleconference meeting rooms. In this sense the wireless network became liberating, however as the signals passed through the air they became vulnerable to intrusion and as such presented a security risk to the computer systems in the wireless network. In the last few years security architecture has gone through a number of important changes including ..” incorporate WLANs under already existing VPN umbrellas and to view them merely as an alternative access method — thus preserving existing VPN infrastructure. Another view has been to address the security of the airwaves which has been demonstrated to be extremely vulnerable. The evolution of security standardisation based upon the work of the IEEE has evolved from WEP to WPA” (Hunt)
Fig 2 illustrates a typical wireless network configuration with network cards, routers being used to despatch wireless waves between computer devices like PC’s, Laptops, Notebooks, Cell Phones, etc.
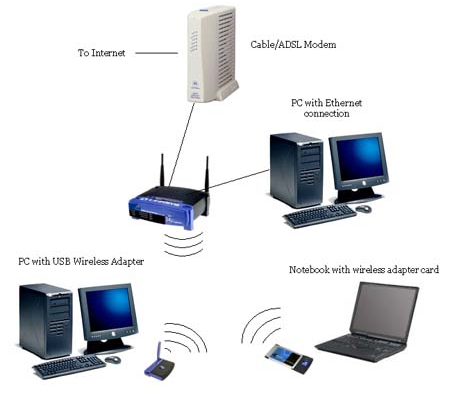
Types of wireless security in use today
Before addressing the types of security measures in place over wireless networks, it is necessary to have some understanding of the treats imposed. These vary from eavesdropping to that of physical intrusion and penetration of your system. Both can be potentially damaging but as a minimum a gross invasion of your privacy. Threats may be as simples as:
Rogue Wireless Area Networks : This is where someone may introduce an additional router to your network and thereby gain access to the wider network. This is essentially a hardware intrusion. Software applications like Network Magic will detect and report such intrusions to the network administrator.
Spoofing Internal Communications: This is a direct attack and intervention from outside computers wishing to gain access to your system. They simulate internal domains and essentially look harmless on the network maps.
Direct Theft of network resources: This is where your system is hacked and the intruder steals bandwidth to surf the internet. They can then indulge in a variety of illegal activities that indicates the source as your network. i.e. downloading pornography, music, video clips etc. Degradation of your network performance is an indication of this type of attack.
“LAN segmentation is used by many organizations to break the network down into smaller, more manageable compartments. Using different LAN segments or virtual LAN (VLAN) segments has a number of advantages. It can enable an organization to expand their network, reduce network congestion, compartmentalize problems for more efficient troubleshooting, and improve security by protecting different VLAN’s from each other.” (Bradley)
Whilst segmentation is a useful step you will also require wireless encryption which is essentially a means of preventing eavesdroppers on to your personal wireless network. The early method used WEP (Wireless equivalent privacy) but this was later discovered to be flawed as anyone who gained the key access could join the network. It was also easily cracked by professional hackers. We quickly moved over to WPA (wireless protect access). This used temporary key integrity protocol and provided a much tougher code system to decipher. Even this was not good enough for large enterprise networks that required a much higher degree of sophistication and security. This moved us into the real of wireless authentication ” Aside from just encrypting wireless data, WPA can interface with 802.1X or RADIUS authentication servers to provide a more secure method of controlling access to the WLAN. Where WEP, or WPA in PSK mode, allows virtually anonymous access to anyone who has the correct key or password, 802.1X or RADIUS authentication requires users to have valid username and password credentials or a valid certificate to log into the wireless network.” (Bradley).
Figure 3 Illustration of intruders to wireless network
Cisco systems provide an approach that is designed for the defence of enterprise wireless networks ” Cisco Adaptive Wireless Intrusion Prevention System (IPS) employs network analysis and signature-based techniques to protect against rogue access points and clients, network reconnaissance, eavesdropping, authentication and encryption cracking, man-in-the-middle attacks, wireless DoS attacks, and zero-day unknown attacks. It also provides automated wireless vulnerability and performance monitoring that persistently scans the wireless network to ward off attacks.” (Cisco)
The major computer manufacturers, software suppliers and communications providers will work with you to provide robust solutions for network security. One of the main considerations being the architecture itself and no computer wireless network is ever really safe from intrusion. Ease of access itself represents the greatest security challenge. The very navigation protocols that make it possible for users of a wireless network to find their destination nodes leave vulnerabilities for those who would use the network in an unethical, harmful or illegal manner” (Malcolm).
| Pro’s of Wireless Security | Con’s of Wireless Security |
| Encryptions are sophisticated | Any system can be penetrated by determined hackers |
| Can build self-defending networks | People may distribute security entry codes to others |
| It is scalable – increase security levels that fit your business model | Spoofing may occur if the wireless network is not properly monitored |
| It is layered i.e. multiple lines of defence | PC’s are now protected by “all in one” software applications i.e. anti virus, anti spyware, network security, system security, firewalls |
| It is modular i.e. LAN Segmentation | The larger the network the vulnerability increases |
| Provides network administration function and allows vigilance | Makes easier entry point for virus applications |
Future of Wireless Security
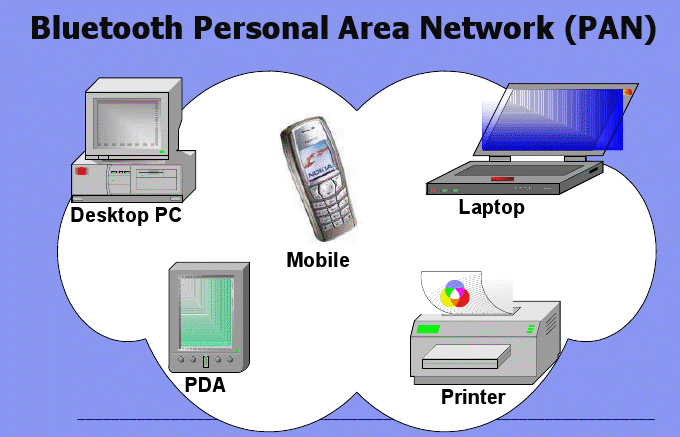
The more immediate security in wireless will focus upon hand held devices and the more sophisticated wireless cellular phones. It is highly likely that we will move towards some chip technology that will be built into the hand held mobile devices similar to that built into credit card applications. This will involve personal identification to the owner of the handheld device with higher degrees of encryption built in for network allowance. This is already being termed Personal Area Networking or PAN for short. The objective being to link all of your personal electronic devices like PC, PDA, Printer, Laptop, Fax etc to your mobile phone. This providing full mobile access to all of your personal data files by your own personal wireless network. There is no doubt that security issues will still need to be addressed in the new wave of technological developments in this area.
Works Cited
Bradley, Tony. Secure Your Wireless Network. 6 12 2007. 14 4 2010 <http://netsecurity.about.com/od/secureyourwifinetwork/a/securewifi.htm>.
Cisco. Cisco Adaptive Wireless IPS Software. 2010. 14 4 2010 <http://www-europe.cisco.com/en/US/products/ps9817/index.html>.
Hunt, M. Mathews and R. Evolution of Wireless LAN Security Architecture to IEEE 802.11i (WPA2). 2010. 11 4 2010 <http://www.actapress.com/Abstract.aspx?paperId=30374>.
Malcolm, Jerry. Help Net Security. 2010. 14 4 2010 <http://www.net-security.org/article.php?id=755>.
Figure 1: Old hard wired network. 1
Figure 2 Typical Wireless network. 2
Figure 3 Illustration of intruders to wireless network. 4
Figure 4: Illustration of Personal Area Network. 6

Stuck with your Essay?
Get in touch with one of our experts for instant help!
Tags:

Time is precious
don’t waste it!
writing help!


Plagiarism-free
guarantee

Privacy
guarantee

Secure
checkout

Money back
guarantee

