Business IT Architecture, Research Paper Example
“IT architecture has proved to be successful in providing a framework that is analysis and decision-making for a progression of new initiatives or changes, at the same time ensuring design integrity and stability.” Cherbakov et al. (2005)
In the crime Fighting System (CFS), one must ask what the key requirements of the system would be. As an architect, it is my responsibility to analyze the project and end up with innovative solutions to the clients’ requirements to meet their every need. This is essential as most people accept information technology to make tasks easier. In the case of the project of the crime fighting system, the police department needs a functioning system that will assist in the handling of crime in a way that will reduce the burden on the police force and make it easier for policing activities. This is an essential component.
Here, the major questions to be answered by the stakeholders are what exactly do you hope the system will achieve. This is the number one concern as it helps in the creation of a blueprint that I as the architect will use in designing and even implementation of the system.
Second, how will the new system incorporate the old system? What aspects of the existing technology will the new system adapt? This will be essential in determining what the shareholders’ value about the old system and ensure a smooth transition from old to new. Finally, what roles will each person in the system play? This is from the implementation to the general workings of the system. This is necessary to come up with safe guards that will ensure the system is incorruptible while at the same time effective and fast.
These three main questions will help in the design of the system as it will provide a clear picture of what the structure is anticipated to do, how it will run and its impact to the police department and other stakeholders as a whole. The key shareholders are the Government, local police authority made op of law enforcement officers to the judicial official and the local community at large. Seeing that the system will have an impact in the community, it is essential to make certain that it is flawless. This is essential as it touches on the sensitive issues of people’s privacy and people’s security. As much as people want to be guaranteed their security, they may not be willing to sacrifice some freedoms, though, it is said freedom comes at a cost.
One should also understand that, in any police department, there are not only police officers. There are also employees that are not necessarily trained in the disciplined forces. Such persons are from the administration of basic police administrative work, to forensic teams, to the legal department that handles legal issues. These personnel are a vital component in the whole law enforcement system, as they make sure the system runs as effectively and smoothly as can be. In any justice system, there is quite a substantial amount of complaints, arrests, suspects, plaintiffs and all manner of persons.
As the architect, it will fall to me to make sure the IT system is properly designed and meets the thresholds set by the clients. The client seeks to make policing work easier for law enforcement authorities and to the public at large. Given that there are many precincts spread out in the general vicinity, the main challenge is linking them together and ensuring secure links put in place for policing activities. The police department has already digitized the records that are in those precincts. Hence, half the work is already done even though it is the easiest part. Therefore, the main challenge will be to plan a scheme that will not only link the precincts, but also other arms of law enforcement. This will guarantee the design of a system that incorporates all aspects of law enforcement for the enactment of steady and swift justice when a crime is committed.
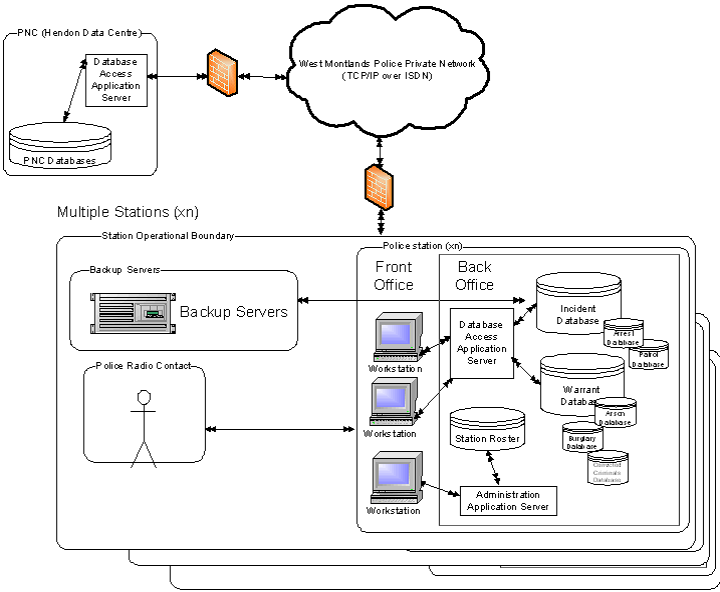
Figure 1. The layout of systems across the police organization
For the system to work properly, there must be the availability of reliable data and records. This will enable me as the architect to set up parameters that will help in the fighting of crime. Data mining is therefore, a key component of the new IT system. This will ensure that the data from the system is properly used in the proper legal manner in the fighting of crime. A key element of the implementation of the system is the timeline. The gravity of its effectiveness is not lost to me as the architect and the potential on the impacts of the system on the lives of the society. It is therefore, essential to make sure that the implementation process is fast, and done in the most professional way to maintain the effectiveness of the system.
Making sure that critical components of the system work flawlessly and the system as a whole is effective. Checks will be in a point, to assure that there is a balance in effectiveness and the fast implementation of justice.The implementation process is done systematically in order to merge the good aspects, improving on them. This will provide a form of continuity that will make the transition easier for the different people who will handle the new system. This will also allow, for the hiring and training of new staff, to run the system. This will make sure that the system will fully be utilized in crime fighting. The implementation processes is therefore, one of the most crucial stage that ensures the proper running of the system. This ensures that flows in the system are identified and amended so that it will not bring about harm in the future.
Rigorous checks on the system will ensure smooth running. Access is restricted to the vital database that contains private, personal information on many aspects on society and the citizens. The levels of security are essential in the administration of the system. Diagnostic checks are essential for the system over a long duration. This will make sure that trouble shooting will be easy when the system is up and running. This maintains the integrity of the system and makes sure that the system will not go offline during general maintenance of the system and infrastructure. This ensures the continuity of work while maintenance makes sure that essential services provided by the system remain functional. This will not sabotage any ongoing investigating or ongoing judicial processes that are needed in the system. This will be a substantial huddle to get over as there needs to be contingency plans put in place in cases where there are vandalism or data losses. The system should therefore, be secure, full proof and have backups that make sure services continue should something foul happen.
Functional necessities deal with what the structure is required to do. It deals with the what aspect of the system. They are observed tasks or processes that are carried out by the structure under growth. For instance, a functional obligation of a supply taking system is “Must update and remember reorder levels of stationery and be able to place an order when ever reorder level is reached”, for a web search engine, “must accurately parse Boolean queries; ” for an automated teller machine, “must process withdrawals and dispenses cash to the customer.”
Non-Functional requirements, on the other hand, are the qualities and principles that the structure under expansion must have or conform with, but which are not responsibilities that will be programmed by the scheme. While functional requirements, checks what the system can perform without considering the physical constraints, the non-functional describes the required attribute of the system, that is, performance, reliability, usability, safety, and security.
A number of essential concerns add to the predicament of conveying non-functional necessities; certain constraints relate to the designed solution that is unfamiliar at the necessities phase they are also highly subjective and can only be determined through complex empirical evaluations. Non-functional requirements tend to relate to one or more functional necessities. Non-functional necessities tend to clash and disagree with; they are no universal rules and guidelines for determining when non-functional requirements met.
Weak Point analysis forms, a part of the design process of a drilling riser system. The objective of weak point analysis in a system is to design and identify break points under extreme conditions. Evaluation Criteria for the weak point analysis is derived for each potential weak point of a system. The weak Point criteria determine failure of the system. It identifies the weak points in the system and calculates the cost effect of it, and enhances the parameters.
The system should be fully tested in this stage until one is sure that it can accommodate the workload that it is required to do. If it is a database that should have over 1 million records, the system should be bombarded, with the slightly higher amount of data, to see how the system will function. If it fails, prevention mechanism should be put in place that will take care of such. It should also be put records that are not required in the system it put integers where text is required.
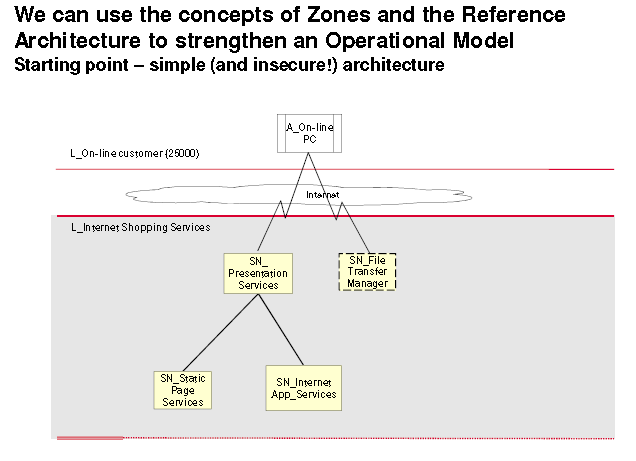
The major purpose of this scheme is to detect intrusion and alert relevant Stakeholders of potential break-in in a monitored site. In the case of a banking system, a security mechanism ensures that no unauthorized person will enter into the banking hall or the bank’s safe. In the case of T & T bank, the company installed a biometric system, which will be able to read the eye retina of the staff before they enter into the bank or the safe area. Every staff information is taken by the and saved into the system to be used for comparison purpose.
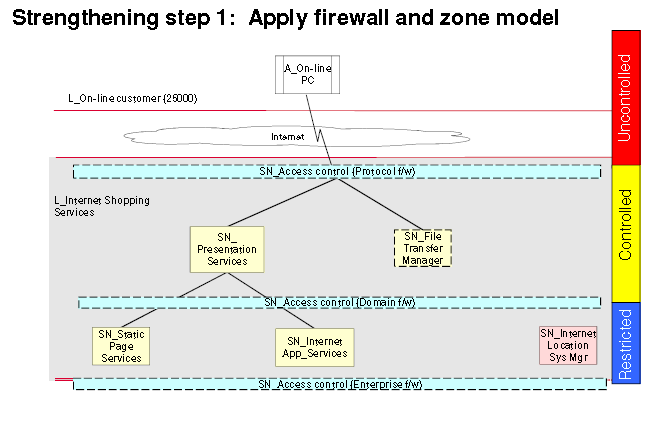
Preconditions
The preconditions of this system will be that every person will first pass through the security desk. Then go into the door where he/she sets his/her focus of one eye into an identification device that will be placed at the door.
Successful and failure outcome
In case of a successful outcome, the signal is send from the identification device to the system, the system verifies the identity of the person at the door if it is an employee, then take some 20 seconds to authenticate the information at hand then send feedback signal to the device at the door allow it to open the door.
Trigger event
In cases, where the person requesting access is unknown by the system, the system will send a signal to its stake holders through the security system notifying of unauthorized personnel at the entrance of the bank. The system will be set in a manner that, it will raise an alarm also to the security personnel to be able to check the surroundings. Another trigger that can be put in place is that, the identification device should be able to have a sound alarm that will notify enable security that there is an illegal request at the door.
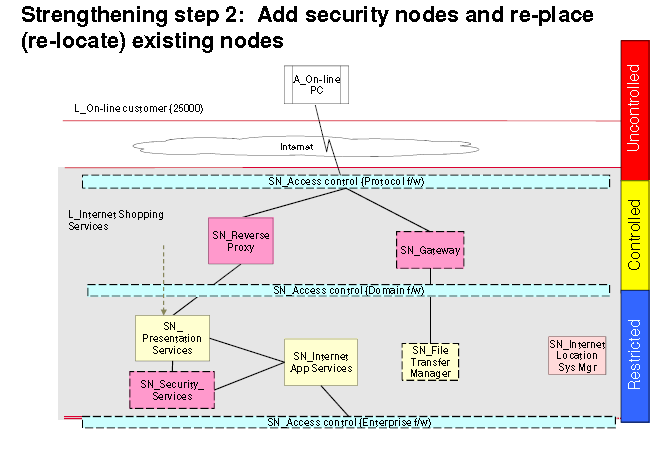
Main scenario
The main scenario of this system is that there will be desktop at the security desk and the stakeholders’ office. They will both be connected into the system, and messages will be send, notify them where never there is an entry into the banking hall or the safe. They will indicate all request whether legal or illegal.
Non-functional requirement
The non-functional requirement of this system will be security. Unlawful entry to the system and its information is not allowed, ensure the integrity of the system from accidental or malicious damage. The system’s data administrator may only change access permissions for system another measure will be backing up the system after every 24 hours and storing in a safe place, not in the same house as the scheme. All exterior infrastructure between the system’s information server and customers must be encrypted.
Architecture Overview Diagram is drawing that is used, as a means of communication, to represent the schematic diagrams showing the governing aspect and building block of an IT system. Its main objectives are to bring out the conceptual understanding of the IT system to its owners, it is an effective tool of communication and can also helps in exploring and evaluating alternative architectural options. Architecture Overview diagram aids in facilitation of orientation of new people joining the project as it enables them easily understand how it works, most importantly it helps to be able to recognize and validate the implications of the architectural approach early enough to be able to check the credibility of the system.
The Architecture Overview Diagram includes both functional and operational concepts. It looks at what the system is supposed to do and how its applications are organize and its internal operations. Using an Architecture Overview Diagram, maintains the IT system. Regular applications fix be carried out, and addition of the new interface that can aid the end-users to adopt comfortably with the system. By, upgrading the major software, the company can be able to keep up with the new, upcoming company with new IT systems by adopting the upcoming software. One can also select components and technologies with reasonable timespans and avoid highly obscure or specialised components wherever possible. Always consider what skills will be required to support the system.
Use performance engineering techniques to design, for scalability, this will enable one to either scale upwards or downwards. Select components, which are not tied to hardware and operating systems platforms.
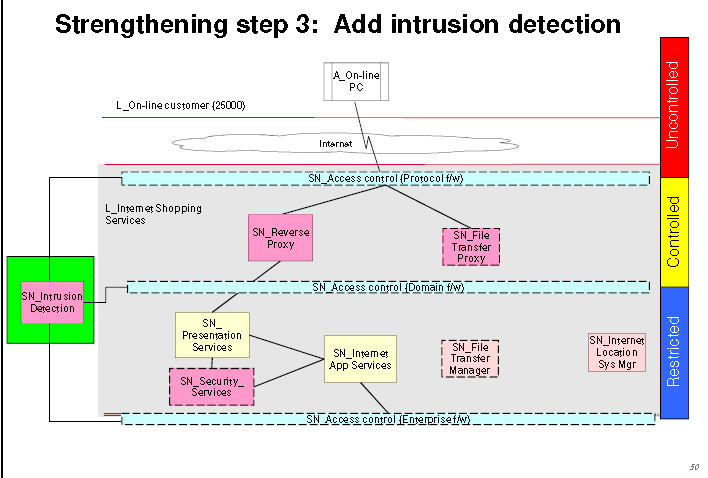
Architecture Overview Diagram of TopBank’s IT Architecture
Performance in IT architecture is a term use to check the functionality of the system and that its need and goals are clearly defined. Each key scenario should have at least one associated performance objective for each situation or performance study of interest. In some cases, however, it may be desirable to break an end-to end performance objective into sub-objectives that are assigned as performance budgets to each part of the processing.
Performance objectives may be expressed in several different ways, as well as reply time, throughput, or constriction on resource usage. An objective such as “the end-to-end time to process a typical user request should be less than 2 seconds” is much more useful.
It is also important to state the situation and performance studies under which the required performance is to be achieved for each combination of scenario and objective. For example, the performance studies may examine the scalability for the fourth quarter for the next 3 years. The conditions would then specify the workload mix and intensity expected for those quarters.
Maintainability in IT system is attained in numerous aspects. This is important to keep the cost of running the system down and thus scaling up the profits made of using the system. It maintains the hardware for longer and effective use and makes it easier to change platforms whenever it is required, this will ensures that the system will up with the technology. It is possible to upgrade to a leading software level, for example, operating systems or the Database Management System.
References
Cherbakov et al. (2005). Impact of service orientation at the business level. IBM Systems Journal, 44(4):653–668.
IBM Corporation. (2010). IT Architecture Workshop: Introduction to the ‘Police Crime Fighting System’ Case Study.
IBM Corporation. (2010). Qualities & Constraints in IT Architecture.
Thurston, Toby. (2008).What do IT architects do all day? University Relations: IBM Corporation

Time is precious
don’t waste it!

Plagiarism-free
guarantee

Privacy
guarantee

Secure
checkout

Money back
guarantee






