 All papers examples
All papers examples
Disciplines

- MLA
- APA
- Master's
- Undergraduate
- High School
- PhD
- Harvard
- Biology
- Art
- Drama
- Movies
- Theatre
- Painting
- Music
- Architecture
- Dance
- Design
- History
- American History
- Asian History
- Literature
- Antique Literature
- American Literature
- Asian Literature
- Classic English Literature
- World Literature
- Creative Writing
- English
- Linguistics
- Law
- Criminal Justice
- Legal Issues
- Ethics
- Philosophy
- Religion
- Theology
- Anthropology
- Archaeology
- Economics
- Tourism
- Political Science
- World Affairs
- Psychology
- Sociology
- African-American Studies
- East European Studies
- Latin-American Studies
- Native-American Studies
- West European Studies
- Family and Consumer Science
- Social Issues
- Women and Gender Studies
- Social Work
- Natural Sciences
- Anatomy
- Zoology
- Ecology
- Chemistry
- Pharmacology
- Earth science
- Geography
- Geology
- Astronomy
- Physics
- Agriculture
- Agricultural Studies
- Computer Science
- Internet
- IT Management
- Web Design
- Mathematics
- Business
- Accounting
- Finance
- Investments
- Logistics
- Trade
- Management
- Marketing
- Engineering and Technology
- Engineering
- Technology
- Aeronautics
- Aviation
- Medicine and Health
- Alternative Medicine
- Healthcare
- Nursing
- Nutrition
- Communications and Media
- Advertising
- Communication Strategies
- Journalism
- Public Relations
- Education
- Educational Theories
- Pedagogy
- Teacher's Career
- Statistics
- Chicago/Turabian
- Nature
- Company Analysis
- Sport
- Paintings
- E-commerce
- Holocaust
- Education Theories
- Fashion
- Shakespeare
- Canadian Studies
- Science
- Food Safety
- Relation of Global Warming and Extreme Weather Condition
Paper Types

- Movie Review
- Essay
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- GCSE Coursework
- Grant Proposal
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- Essay
- GCSE Coursework
- Grant Proposal
- Interview
- Lab Report
- Literature Review
- Marketing Plan
- Math Problem
- Movie Analysis
- Movie Review
- Multiple Choice Quiz
- Online Quiz
- Outline
- Personal Statement
- Poem
- Power Point Presentation
- Power Point Presentation With Speaker Notes
- Questionnaire
- Quiz
- Reaction Paper
- Research Paper
- Research Proposal
- Resume
- Speech
- Statistics problem
- SWOT analysis
- Term Paper
- Thesis Paper
- Accounting
- Advertising
- Aeronautics
- African-American Studies
- Agricultural Studies
- Agriculture
- Alternative Medicine
- American History
- American Literature
- Anatomy
- Anthropology
- Antique Literature
- APA
- Archaeology
- Architecture
- Art
- Asian History
- Asian Literature
- Astronomy
- Aviation
- Biology
- Business
- Canadian Studies
- Chemistry
- Chicago/Turabian
- Classic English Literature
- Communication Strategies
- Communications and Media
- Company Analysis
- Computer Science
- Creative Writing
- Criminal Justice
- Dance
- Design
- Drama
- E-commerce
- Earth science
- East European Studies
- Ecology
- Economics
- Education
- Education Theories
- Educational Theories
- Engineering
- Engineering and Technology
- English
- Ethics
- Family and Consumer Science
- Fashion
- Finance
- Food Safety
- Geography
- Geology
- Harvard
- Healthcare
- High School
- History
- Holocaust
- Internet
- Investments
- IT Management
- Journalism
- Latin-American Studies
- Law
- Legal Issues
- Linguistics
- Literature
- Logistics
- Management
- Marketing
- Master's
- Mathematics
- Medicine and Health
- MLA
- Movies
- Music
- Native-American Studies
- Natural Sciences
- Nature
- Nursing
- Nutrition
- Painting
- Paintings
- Pedagogy
- Pharmacology
- PhD
- Philosophy
- Physics
- Political Science
- Psychology
- Public Relations
- Relation of Global Warming and Extreme Weather Condition
- Religion
- Science
- Shakespeare
- Social Issues
- Social Work
- Sociology
- Sport
- Statistics
- Teacher's Career
- Technology
- Theatre
- Theology
- Tourism
- Trade
- Undergraduate
- Web Design
- West European Studies
- Women and Gender Studies
- World Affairs
- World Literature
- Zoology
Developing a Personal Calendar System Across Multiple Microsoft Platforms, Research Paper Example
Hire a Writer for Custom Research Paper
Use 10% Off Discount: "custom10" in 1 Click 👇
You are free to use it as an inspiration or a source for your own work.

A. Naming and Programming Conventions
It is required of a naming convention to allow ascertaining of some useful information that describes the targeted host (s). For you to be able to address any particular subdivision of an environment being managed, you should be able to incorporate some amount of reasoning into the naming systems. A good naming system should carry the following characteristics:
i) Parsability- This is the ability to parse the convention(s) for meaning.
– It also enables the building of programming and automation in a structured convention.
thus easing on the categorization of computers.
ii). Information components having a number of characteristics- All information components should have every possible value identified and noted documented before adopting the convention. Additionally, other values can be added later if it is required.
iii). All of the computer names having a consistent amount of characters-
Iv). It is advisable that a computer’s name should not change during its lifetime or until it is redeployed, thus the information component s should be chosen carefully.
v). Incorporation of logic and consistency
B. The Likely Components for Naming Conventions
Here is a list of some of the components you are encouraged to include in your naming convention:
- The environment in which it is operating e.g. development, Production or test
- Location e.g. nation, city, office or building
- Usage category e.g. public, home or office
- Organizational Department e.g. human resource or production
- The username of the employee
- The employment type of the employee
- Portability e.g. desktop or laptop
- Server/Client
- The platform
C Specific Examples of Naming Conventions
Some naming conventions have regulations that go beyond the consideration of a specific domain. They therefore represent bigger conventional values that are defined by software architectures in the programming language:
- The Hungarian notation
It is the most recognized notation that encodes either the type (systems Hungarian) or the purpose (apps Hungarian). For instance a prefix “sz” for the szName variable is an indication that the variable has a zero value that is null. It is also important to note that the Hungarian notation has been particularly used to prefix variables that [have information relating to their type i.e. whether it is a double or an integer. However, this is not the best thing to do since the IDE is responsible for telling you about a variable’s type, hence it can lead to names that have funny and complex characteristics. Those who came up with the idea of Hungarian had this general thought in mind: creation of abstract types that will be able to describe how a variable is put into usage and not its representation. The importance of this idea is that integers and pointers are kept apart and therefore cannot mix. Another very vital role of this feature is that it can really become a great technique that can aid in the separation of concepts that are in most cases used alongside each other, but which are not supposed to be mixed. This therefore shows the vitality of the Hungarian notation in improving the software performance in a number of platforms.
- C and C++
Both of them are language specific conventions. In both the C++ and C, the standard library and keywords identifiers are lowercase in most cases. The abbreviation of names is very common in the C standard library. An example is isalnum with the aim of testing if a character is alphanumeric or not. The standard library of the C++ employs an underscore that acts as the word separator in most cases. A good example in this context is out_of_range. It is by convention that all identifiers that represent macros should be written by use of upper case letters and underscores only. This is relevant to the convention that many programming languages use i.e. constraints should be represented by identifiers that are all-upper-case. Nonetheless, held in reserve for implementation are names that begin with an underscore or those that contain a double underscore and capital letters.
- Java
Java communities for example Ambysoft are responsible for establishing and suggesting the naming conventions for the identifiers. No java compiler has ever imposed the rules they come up with, on the other hand failure to follow these rules results confusion and errors in coding. Another java coding that is often used requires the LowerCamelCase and UpperCamelCase to be put into use in both methods and instances. As a result, some IDE have utilized this feature in their shortcuts. Therefore typing words such as NPE and activating the assistance of the content will bring this suggestion, NullPointerException
It is important to note that the main reason why programmers do not construct everything in the assembly code is because of the issue of readability. This is aimed at reducing the accessibility of the coded information from many users. One should also have it in mind that the first universal rule in naming conventions is that programmers should select identifiers that are meaningful for all the constructs.
D. It Troubleshooting Best Practices
Windows Azure Troubleshooting
In order to schedule a job, you must first create a job object, and then add it to a flow or create a new flow. A deployed flow is a group of jobs and their dependencies that have been deployed for scheduling.
From the navigation tree, select the Schedule Manager plug-in, and then select New Flow from the Actions menu, the pop-up menu, or the toolbar. The New Flow window appears.
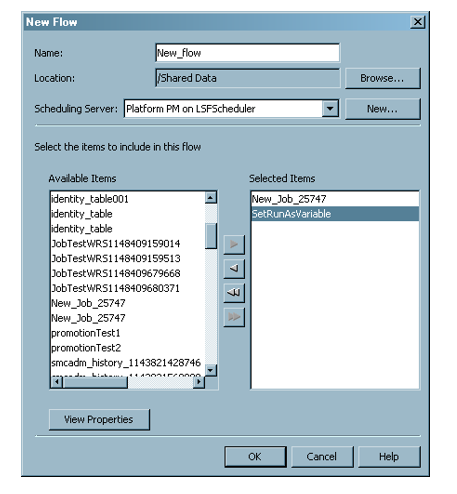
No matter the hosting model or language, you should focus your efforts in the areas below:
- Graceful handling of infrastructure failures or those of the dependent services
- Proper monitoring, error logging and tracing of all the components services
- Debugging of errors as earlier as before promotion for production up to the network and component level
An application designed with these ideas in mind assures you the provision of vital information by the application that will enable you to trail the origin of the unexpected behaviors.
Graceful handling of errors
Graceful handling of errors is important especially to the nature of the distributed windows azure. A good troubleshooting process will begin with a handling design of a transient-failure. Transient errors are the main cause of the failures of cloud applications. These errors arise as a result of latencies and network connections that are intermittent. These errors can be dealt with by doing the following: (1) loose coupling of Window Azure applications, (2) making asynchronous calls to avoid last minute rush, and (3) using a transient error handling approach which executes to solve the issues. The call to services should make use the layer of the transient handling error in detecting failure scenarios and thereafter retry calling based on the configuration settings.
Appropriate logging and tracing
The two are of utmost importance compared to the traditional debuggers that focus on one process. Execution of your application with the relevant data is shared across a number of services hosted on different machines. This becomes almost impossible in the case of large scale distributed applications. Thus tracing and logging will help you to follow an application’s execution and data streaming hence giving you an increased understanding of the application’s state. Windows Azure applications have an in-built tracing and logging strategy that makes it easier to locate issues and repair them as quickly as possible thus saving you the need to call Microsoft for assistance.
Monitoring the application
This is essential since it enables you to do the following:
- Discover the available Windows Azure application
- Determining the status of each of the role instances
- Monitor and gather performance information such as latency
- Monitor and assemble events
- Monitor and collect trace message
- Monitor the quality of the service metrics
- Execute capacity planning
- Perform the analysis of traffics such as users and views
- Make an estimation of the billing and
- Perform the auditing exercise
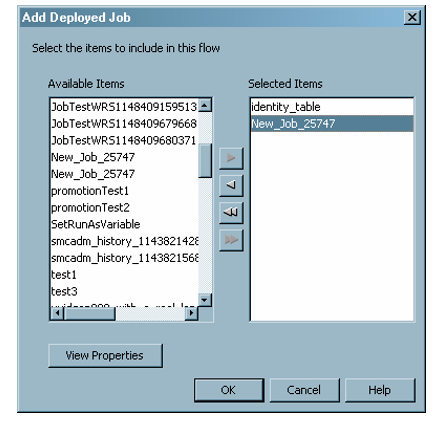
You can add jobs to an existing deployed flow after it has been created. Select a flow, and then select Add a Job from the pop-up menu, the toolbar, or the Actions menu. Use the Add Deployed Job dialog box to select from the jobs that have been deployed for scheduling.
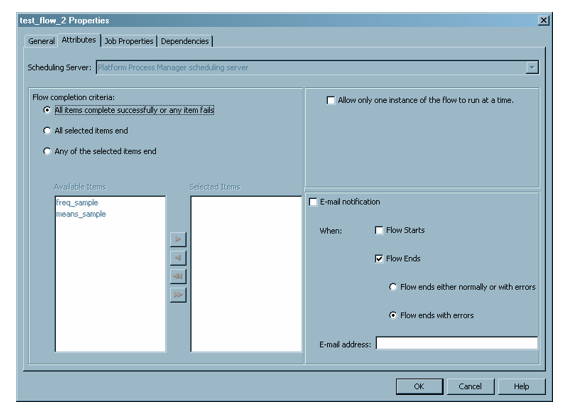
Setting Deployed Flow Properties
The Properties window for a flow also lets you specify options for the flow. The Attributes tab enables you to specify the condition for the flow to be considered as completed, whether only one instance of the flow can run at once, and any e-mail notifications that you should receive based on the condition of the flow. The attributes available depend on the type of scheduling server associated with the deployed flow.
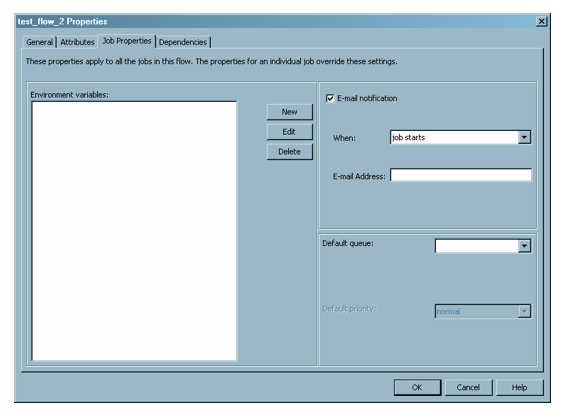
The Job Properties tab specifies the properties that are applied to all jobs in the flow, including environment variables, e-mail notification for job events, and the default queue. However, any properties that you set on an individual job override the properties set on the Job Properties tab.
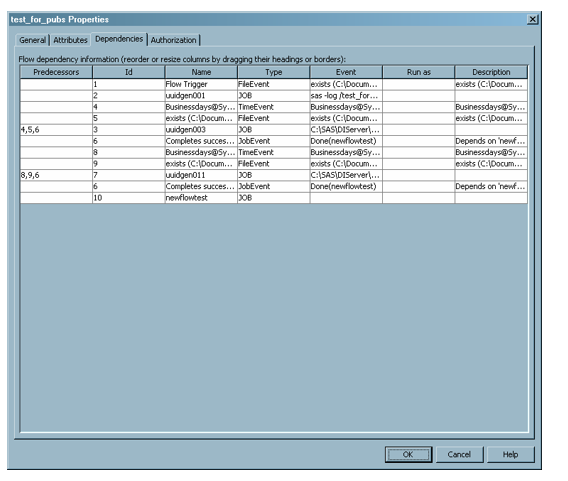
The Dependencies tab contains a table of all the dependencies in the flow and their relationships to the jobs in the flow.
- The Monitoring Pack for Windows Azure by Microsoft System Center
This pack allows you to be able to use the operations manager to monitor the availability and state of the Windows Azure applications.
- The Management Tool by Windows Azure Platform (MMC)
It is used to manage the Windows Azure host services and storage accounts. This tool comes as a model and has a source code that you can use to carry out the various configuration and management exercises by using the Diagnostics Applications in Windows Azure Management.
- Celebrate tools
Include the Azure Diagnostic Manager and Cloud Storage Studio. Azure Diagnostic Manager enables you to view, manage and download diagnostic data that has been collected by the applications. Cloud Storage Studio manages Windows Azure storage
- Network Monitoring: AlertBot, Keynote and Pingdom
These are solutions for monitoring the applications remotely. They allow you to monitor your applications’ availability and give you ways of boosting their performance. Services such as Pingdom have email, desktop and SMS notifications whenever an error is detected.
- Azure Check
It monitors your Windows Azure web applications from outside. You are required to download the code and then add it as a startup task in your deployment. One of its advantages is that it does not require you to store logs in the storage accounts and in this case highly lessens the cost of monitoring your Windows.
- AVIcode
It is provided by Microsoft and is part of the Microsoft Systems Center. It is responsible for delivering .NET applications optimization capabilities as well as providing a diverse application monitoring suite.
- Performance Profiling
This enables you to keep a profile of your Windows Azure Application when it is running in Azure so as to determine performance issues that are available.
- Windows Azure VM Assistant
This is a CodePlex project that collects troubleshooting data in a central place after you remote the computer into a virtual machine.
- Debugging of errors wherever possible
You are encouraged to locally debug your application before you set up an application in Windows Azure. After doing this, the instrumentation built in your application is the one that will show the point at which the problems are rooted.
- Debugging Node.js applications
In this scenario, you can use the Node-Inspector tool which is run on your development machine locally using the storage emulator. You are encouraged to install a full version of the IINode that can be found at GitHub.
- IntelliTrace
This is helpful for debugging applications before they are deployed into production. This tool can be found in Microsoft Visual Studio 2010 Ultimate.
- Fiddler
This is a web-based debugging proxy that is capable of logging all the http(s) traffics between your computer and the internet. It gives you he ability to inspect traffic, set the breakpoints and be able to fiddle outgoing and incoming data. This tool is very useful for troubleshooting the Windows Azure Storage. Here is the process you should follow:
- Launch the fiddler
- Launch the service in development fabric
- Browse to the url http://ipv4.fiddler:/. After doing all this, fiddler will be able to trace the request.
References
Humphrey, Watts, S., a Discipline in Software Engineering, Addison-Wesley, Reading 1995.
Labrosse, Jean J., an2000: C Coding Standard, HTTP://WWW.micrium.com
Meyer, Bertrand, Object-Oriented Software Construction 2nd Edition, Prentice Hall, 1997. Isbn: 0-136-29155-4
Motor Industry Software Reliability Association (Misra), Misra Limited, Misra-C:1998 Guidelines for the Use of the C Language in Vehicle Based Software, April 1998, Isbn 0-9524156-9-0. See Also HTTP://WWW.misra.org.UK
Portable Inheritance and Polymorphism in C, ESP, December 1997
Samek, Miro, Practical St

Stuck with your Research Paper?
Get in touch with one of our experts for instant help!

Time is precious
don’t waste it!
writing help!


Plagiarism-free
guarantee

Privacy
guarantee

Secure
checkout

Money back
guarantee

