 All papers examples
All papers examples
Disciplines

- MLA
- APA
- Master's
- Undergraduate
- High School
- PhD
- Harvard
- Biology
- Art
- Drama
- Movies
- Theatre
- Painting
- Music
- Architecture
- Dance
- Design
- History
- American History
- Asian History
- Literature
- Antique Literature
- American Literature
- Asian Literature
- Classic English Literature
- World Literature
- Creative Writing
- English
- Linguistics
- Law
- Criminal Justice
- Legal Issues
- Ethics
- Philosophy
- Religion
- Theology
- Anthropology
- Archaeology
- Economics
- Tourism
- Political Science
- World Affairs
- Psychology
- Sociology
- African-American Studies
- East European Studies
- Latin-American Studies
- Native-American Studies
- West European Studies
- Family and Consumer Science
- Social Issues
- Women and Gender Studies
- Social Work
- Natural Sciences
- Anatomy
- Zoology
- Ecology
- Chemistry
- Pharmacology
- Earth science
- Geography
- Geology
- Astronomy
- Physics
- Agriculture
- Agricultural Studies
- Computer Science
- Internet
- IT Management
- Web Design
- Mathematics
- Business
- Accounting
- Finance
- Investments
- Logistics
- Trade
- Management
- Marketing
- Engineering and Technology
- Engineering
- Technology
- Aeronautics
- Aviation
- Medicine and Health
- Alternative Medicine
- Healthcare
- Nursing
- Nutrition
- Communications and Media
- Advertising
- Communication Strategies
- Journalism
- Public Relations
- Education
- Educational Theories
- Pedagogy
- Teacher's Career
- Statistics
- Chicago/Turabian
- Nature
- Company Analysis
- Sport
- Paintings
- E-commerce
- Holocaust
- Education Theories
- Fashion
- Shakespeare
- Canadian Studies
- Science
- Food Safety
- Relation of Global Warming and Extreme Weather Condition
Paper Types

- Movie Review
- Essay
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- GCSE Coursework
- Grant Proposal
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- Essay
- GCSE Coursework
- Grant Proposal
- Interview
- Lab Report
- Literature Review
- Marketing Plan
- Math Problem
- Movie Analysis
- Movie Review
- Multiple Choice Quiz
- Online Quiz
- Outline
- Personal Statement
- Poem
- Power Point Presentation
- Power Point Presentation With Speaker Notes
- Questionnaire
- Quiz
- Reaction Paper
- Research Paper
- Research Proposal
- Resume
- Speech
- Statistics problem
- SWOT analysis
- Term Paper
- Thesis Paper
- Accounting
- Advertising
- Aeronautics
- African-American Studies
- Agricultural Studies
- Agriculture
- Alternative Medicine
- American History
- American Literature
- Anatomy
- Anthropology
- Antique Literature
- APA
- Archaeology
- Architecture
- Art
- Asian History
- Asian Literature
- Astronomy
- Aviation
- Biology
- Business
- Canadian Studies
- Chemistry
- Chicago/Turabian
- Classic English Literature
- Communication Strategies
- Communications and Media
- Company Analysis
- Computer Science
- Creative Writing
- Criminal Justice
- Dance
- Design
- Drama
- E-commerce
- Earth science
- East European Studies
- Ecology
- Economics
- Education
- Education Theories
- Educational Theories
- Engineering
- Engineering and Technology
- English
- Ethics
- Family and Consumer Science
- Fashion
- Finance
- Food Safety
- Geography
- Geology
- Harvard
- Healthcare
- High School
- History
- Holocaust
- Internet
- Investments
- IT Management
- Journalism
- Latin-American Studies
- Law
- Legal Issues
- Linguistics
- Literature
- Logistics
- Management
- Marketing
- Master's
- Mathematics
- Medicine and Health
- MLA
- Movies
- Music
- Native-American Studies
- Natural Sciences
- Nature
- Nursing
- Nutrition
- Painting
- Paintings
- Pedagogy
- Pharmacology
- PhD
- Philosophy
- Physics
- Political Science
- Psychology
- Public Relations
- Relation of Global Warming and Extreme Weather Condition
- Religion
- Science
- Shakespeare
- Social Issues
- Social Work
- Sociology
- Sport
- Statistics
- Teacher's Career
- Technology
- Theatre
- Theology
- Tourism
- Trade
- Undergraduate
- Web Design
- West European Studies
- Women and Gender Studies
- World Affairs
- World Literature
- Zoology
Network Forensics, Essay Example
Hire a Writer for Custom Essay
Use 10% Off Discount: "custom10" in 1 Click 👇
You are free to use it as an inspiration or a source for your own work.

Introduction
Internet Crime and particularly illegal entry into other computer systems i.e. hacking is deemed to be a Federal Offence in the USA and falls under the investigative jurisdiction of the Federal Bureau of Investigation (FBI). Criminal computer hacking has been legally defined as any person who willingly and knowingly commits an act of cyber terrorism, credit card fraud, malicious vandalism, identity theft or other cyber-crime by hacking into a Corporate or Government system. Such criminal acts are treated very seriously in the USA and will be subject to harsh penalties. Such intrusions are capable of creating a tremendous amount of malicious damage.
In the subject of Identity Theft this has taken on added dimensions with the large amount of confidential personal data retained on computer systems. This makes such systems vulnerable to cyber crime. (Seger, A. 2007)
Identity theft
With computer systems the concept of identity theft can be placed into three broad categories:
- Where information or data is extracted through a physical theft from the computer systems. This being achieved by such methods as hacking, illegal external entry, phishing or internal theft;
- Where Identity information is acquired illegally from a system and subsequently sold for illegal purposes i.e. credit card theft, bank teller machines, false identification cards, fraudulent acquisition of goods
- Where Identity information is extracted with the deliberate attempt to commit fraud. This covering a comprehensive list of unlawful activities.
Identity Theft Investigation
Fig 1 describes the Forensic investigation steps that were followed in the examination procedures of an Identity theft. The investigation defined the incident in terms of how the ID theft was accomplished, the information that was stolen (accessed), the location of the data on on the system, the severity and sensitivity of this information, the security safeguards that were initially presented on the data i.e. encryptions. The Media Analysis comprising the physical observation and examination of the system. The Evidence Analysis that which indicates physical intrusion and attack on the system resulting in material theft and or damage to the system. Forensic evidence is collected at this point including digital imaging of appropriate back up systems. Scenario Construction attempts to trace the events that took place and look for forensic trails that lead to the source of the attack. This means tracking to computer IP addresses, tracing stolen documents or records, examination of criminal records that may provide clues to the attack looking at similarity indexes. Evaluation looks at the results from previous stages and consolidating the results into a single outcome of the investigation.
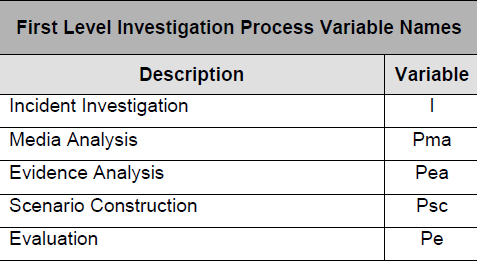
This investigation produced :- A Network intrusion report order to show information concerning the intruder to the system i.e. the IP Address, access details etc. In addition security information provided by the Network Security software that might include such items as access times and the type of data accessed. A physical sector image report , essentially a duplicate of the existing system that can be used for forensic examination purposes. A Network Security Audit , primarily a verification exercise that examines vulnerabilities and weak access points in the system. In addition examination of the security elements of the systems that include such items as firewalls, virus protection, encryptions and details on any hardware vulnerabilities.
The investigation used a sophisticated software forensics tool called X-Ways Forensics and described as “a powerful disk analysis tool: capturing free space, slack space, inter-partition space, and text, creating a fully detailed drive contents table with all existing and deleted files and directories and even alternate data streams (NTFS), Bates-numbering files, and more.” (XWays-Forensics, 2011). Investigations focused on specific network problem areas:
Rogue Wireless Area Networks: This is where someone may introduce an additional router to your network and thereby gain access to the wider network. This is essentially a hardware intrusion. Software applications like Network Magic will detect and report such intrusions to the network administrator.
Spoofing Internal Communications: This is a direct attack and intervention from outside computers wishing to gain access to your system. They simulate internal domains and essentially look harmless on the network maps.
Direct Theft of network resources: This is where your system is hacked and the intruder steals bandwidth to surf the internet. They can then indulge in a variety of illegal activities that indicates the source as your network. i.e. downloading pornography, music, video clips etc. Degradation of your network performance is an indication of this type of attack. (Bradley, 2007).
Conclusions
This was the result of an individual hacker that had a previous criminal record for conviction of similar offences. Forensic trails located his IP address and location of operation. Police records cross-referenced via a similarity index and subsequent investigation resulted in physical evidence being obtained on stolen material located on the identified computer.
References
Bradley, T. (2007, 12 6). Secure your wireless network. Retrieved 11 25, 2011
Seger, A. (2007). Identity theft and the convention on cybercrime. Courmayeur, Italy: United Nations ISPAC.
XWays-Forensics. (2011, 11 28). Network Intrusion Software. Retrieved from XWays-Forensics: http://x-ways.net/winhex/forensics.html

Stuck with your Essay?
Get in touch with one of our experts for instant help!

Time is precious
don’t waste it!
writing help!


Plagiarism-free
guarantee

Privacy
guarantee

Secure
checkout

Money back
guarantee

