 All papers examples
All papers examples
Disciplines

- MLA
- APA
- Master's
- Undergraduate
- High School
- PhD
- Harvard
- Biology
- Art
- Drama
- Movies
- Theatre
- Painting
- Music
- Architecture
- Dance
- Design
- History
- American History
- Asian History
- Literature
- Antique Literature
- American Literature
- Asian Literature
- Classic English Literature
- World Literature
- Creative Writing
- English
- Linguistics
- Law
- Criminal Justice
- Legal Issues
- Ethics
- Philosophy
- Religion
- Theology
- Anthropology
- Archaeology
- Economics
- Tourism
- Political Science
- World Affairs
- Psychology
- Sociology
- African-American Studies
- East European Studies
- Latin-American Studies
- Native-American Studies
- West European Studies
- Family and Consumer Science
- Social Issues
- Women and Gender Studies
- Social Work
- Natural Sciences
- Anatomy
- Zoology
- Ecology
- Chemistry
- Pharmacology
- Earth science
- Geography
- Geology
- Astronomy
- Physics
- Agriculture
- Agricultural Studies
- Computer Science
- Internet
- IT Management
- Web Design
- Mathematics
- Business
- Accounting
- Finance
- Investments
- Logistics
- Trade
- Management
- Marketing
- Engineering and Technology
- Engineering
- Technology
- Aeronautics
- Aviation
- Medicine and Health
- Alternative Medicine
- Healthcare
- Nursing
- Nutrition
- Communications and Media
- Advertising
- Communication Strategies
- Journalism
- Public Relations
- Education
- Educational Theories
- Pedagogy
- Teacher's Career
- Statistics
- Chicago/Turabian
- Nature
- Company Analysis
- Sport
- Paintings
- E-commerce
- Holocaust
- Education Theories
- Fashion
- Shakespeare
- Canadian Studies
- Science
- Food Safety
- Relation of Global Warming and Extreme Weather Condition
Paper Types

- Movie Review
- Essay
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- GCSE Coursework
- Grant Proposal
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- Essay
- GCSE Coursework
- Grant Proposal
- Interview
- Lab Report
- Literature Review
- Marketing Plan
- Math Problem
- Movie Analysis
- Movie Review
- Multiple Choice Quiz
- Online Quiz
- Outline
- Personal Statement
- Poem
- Power Point Presentation
- Power Point Presentation With Speaker Notes
- Questionnaire
- Quiz
- Reaction Paper
- Research Paper
- Research Proposal
- Resume
- Speech
- Statistics problem
- SWOT analysis
- Term Paper
- Thesis Paper
- Accounting
- Advertising
- Aeronautics
- African-American Studies
- Agricultural Studies
- Agriculture
- Alternative Medicine
- American History
- American Literature
- Anatomy
- Anthropology
- Antique Literature
- APA
- Archaeology
- Architecture
- Art
- Asian History
- Asian Literature
- Astronomy
- Aviation
- Biology
- Business
- Canadian Studies
- Chemistry
- Chicago/Turabian
- Classic English Literature
- Communication Strategies
- Communications and Media
- Company Analysis
- Computer Science
- Creative Writing
- Criminal Justice
- Dance
- Design
- Drama
- E-commerce
- Earth science
- East European Studies
- Ecology
- Economics
- Education
- Education Theories
- Educational Theories
- Engineering
- Engineering and Technology
- English
- Ethics
- Family and Consumer Science
- Fashion
- Finance
- Food Safety
- Geography
- Geology
- Harvard
- Healthcare
- High School
- History
- Holocaust
- Internet
- Investments
- IT Management
- Journalism
- Latin-American Studies
- Law
- Legal Issues
- Linguistics
- Literature
- Logistics
- Management
- Marketing
- Master's
- Mathematics
- Medicine and Health
- MLA
- Movies
- Music
- Native-American Studies
- Natural Sciences
- Nature
- Nursing
- Nutrition
- Painting
- Paintings
- Pedagogy
- Pharmacology
- PhD
- Philosophy
- Physics
- Political Science
- Psychology
- Public Relations
- Relation of Global Warming and Extreme Weather Condition
- Religion
- Science
- Shakespeare
- Social Issues
- Social Work
- Sociology
- Sport
- Statistics
- Teacher's Career
- Technology
- Theatre
- Theology
- Tourism
- Trade
- Undergraduate
- Web Design
- West European Studies
- Women and Gender Studies
- World Affairs
- World Literature
- Zoology
Network Security at the Data Link Layer, Essay Example
Hire a Writer for Custom Essay
Use 10% Off Discount: "custom10" in 1 Click 👇
You are free to use it as an inspiration or a source for your own work.

Big Switch Network Design
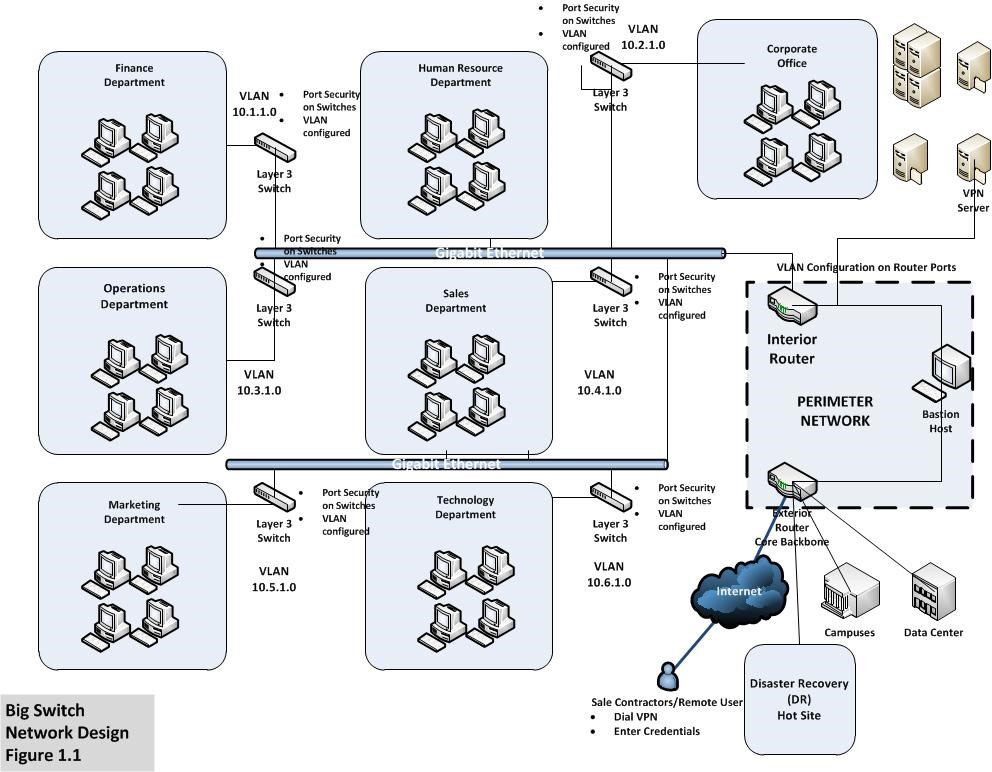
As shown in fig 1.1, the proposed network design for a small medium size enterprise. The primary objective for the newly designed network is to minimize or prevent MAC layer attacks, Virtual LAN attacks, Spoofing attacks, securing network switches and configuring Virtual LAN across the network. For providing security mechanism to the internal data communication, Virtual local area networks (VLAN) are recommended. The VLAN separates the domain of the departments within the organization. VLAN uses encryption techniques for transmitting data over the network. Access policy list is also configured in the VLAN for defining the routes. Moreover, VLAN is considered as a broadcast domain. It concludes that the broadcast generates from one computer can only be received to the destination which is defined by some criteria in the broadcast domain. The advantage of VLAN implementation includes an efficient way of bandwidth utilization and eliminating the network from possible broadcast storms, which results in denial of service. Furthermore, by implementing VLANs, the capacity of switching technology is utilized to its full potential. VLAN also supports ‘VLAN trunking protocol’. The ‘VLAN trunking protocol’ will significantly reduce administration for the switched network.
Addressing Security Issues and Deployment Approach for WAN
A router is a core computing and packet processing devices in the big switch computer network. Router connects two or more networks with different subnets, enabling the networks to expand on an enterprise level. Logically the router builds a routing table, where it stores all the route addresses. For example, the data packet source and destination is stored in the routing table. The network administrator can statically define the network addresses which are called as ‘static routes’. The dynamic routing protocol is used for the automation of exchanging data packets with other routers located in campuses of Big switch. The selection criterion of the router depends on the network requirements. The data transmission gauge, which is also called as the maximum transmission unit (MTU) is also considered for optimal network efficiency. To support the current scenario, the router must support redundancy and security features for the Big switch enterprise network. As the current network design incorporates a core backbone, it is essential for the network to be operational and efficient. Cisco 3845 integrated service router will fulfill all the network requirements.
The Cisco 3845 Integrated Services Router provides optimal performance for parallel services on the local area network including security, voice and enhanced services. Improved speculation is achievable by increased performance and modularity. The Cisco 3845 ISR consist of robust ‘WAN’ slots to improve density. The router supports over 90 modules for enhanced and latest network functionality. The router supports both copper and fiber interface. Keeping in mind that the cost must be kept to a minimum, the router supports power over Ethernet (POE). It is the revolutionary technology integrating data, voice and power on a standard CAT 5 Ethernet infrastructure. This technology provides power to the devices connected on the network in parallel. The security aspect is attractive as the router has built in features for data encryption. The router also supports up to 2500 Virtual Private Network tunnels for creating connectivity with campuses of Big switch enterprise network. However, the AIM-HPII-PLUS Module is required to support VPN capability in the router. VPN is further elaborates as it is created to improve security and productivity by combining Cisco VPN technology. Cisco VPN has proved to be a reliable name in the industry to connect remote offices, remote users and remote sites in a secure way. VPN is most widely used for remote connectivity solutions in all sizes of organizations. It is affordable due to the provision of public switched telephone networks (PSTN) (Tiso,). The deployment of router will be carried out by connecting the hot site initially with the current operational network. After establishing connectivity with the hot site, router will be replaced by the vendors or the staff available at big Switch.
Moreover, cost savings and productivity is also supported encryption and authentication techniques that defend data in transportation from unauthorized access and attacks. The Cisco based VPN server uses highly secure communication mechanism with integrated access rights to specific users. The network administrator can quickly add remote sites and users without expanding the current infrastructure. It will improve productivity by extending the current network, applications and collaborative tools. These features enable to reduce the communication cost by a significant level along with improving the efficiency of administrative tasks and configuration. The Big switch can adopt VPN technologies.
As per fig 1.1, VLAN configuration is carried out in data switches and it is also configured in the ports of the router. In order to secure the network from threats associated with VLAN, for instance, VLAN hopping is a type of network attack in which the workstation of the end user broadcast data packets to another VLAN instead of the legitimate VLAN. As VLAN do not allow data packets to be send at another VLAN, the traffic is marked with another VLAN ID that belongs to the end user workstation. Similarly, in this scenario, an attacker may act like a data switch and can convey trunking for sending and receiving data from other VLANs. In order to mitigate attacks associated with VLAN, configuration needs to be done in the router and the switch as well. The first primary objective is to dedicate VLAN identifications for all available trunk ports. Moreover, there is also a requirement of de activating all the unused switch ports and allocate port numbers in unused VLANs. Furthermore, all the ports already accessible by the users must be set to non-trunking mode by de activating DTP (Network security at the data link layer (layer 2) of LAN). For addressing Media Access Control (MAC) spoofing attacks, there is a requirement of analyzing the functionality and approach of the threat. MAC spoofing attack incorporates learning of a MAC address pertaining to another host for making an attempt to the target switch. The switch will forward the frames destined for the host connected remotely to the attacker. In process of sending frames with dissimilar source address, the attacker gets the chance to overwrite the Content Addressable Memory (CAM) table entry (Network security at the data link layer (layer 2) of LAN). The modification to the CAM table enables the attacker to forward destined data packets of the host to the attacker. As per fig 1.1, port security is incorporated to every layer 3 switch to eliminate or minimize MAC spoofing. Likewise, port security is capable of specifying the MAC address for workstations that are connected to a specific port. If there is any violation in terms of connecting other workstation other than the authentic one, logs are generated that can be viewed by the network administrators for rectification.
The perimeter network shown in Fig 1.1 demonstrates interior router that is connected to the internal network and exterior router is connected to the external network i.e. Internet, campuses, sale contractors. The perimeter network provides robust security by deploying a bastion host between the two routers. Bastion host is similar to intrusion detection system and reports immediate whenever anomalies are detected within the network. However, Demilitarize Zone (DMZ) is also ideally placed at the perimeter network, when operating on a domain based computer network. The demilitarized zone operates as a part of a firewall configuration in order to secure the local area networks. If a DMZ is configured on the whole network or on specific workstations, they are known to be in a DMZ. Moreover, the zone also facilitates workstations that are configured behind the firewall to initialize request that are considered as outbound traffic to the DMZ. The functionality of DMZ is similar to a proxy server, as the workstations configured in DMZ interact with the public networks. Furthermore, the most significant advantage for a DMZ is that it protects the local area network domains by segregating the network layer (RE: [FW1] DMZ advantages). Likewise, the disadvantages associated with DMZ are not significant, but one issue can be highlighted, as the segregation may create a hassle for the network administration because DMZ requires frequent updates and maintenance. Moreover, the hardware cost is high and requires dedicated hardware in order to implement DMZ within the network. Deployment includes a switch, separate firewall and IDS etc.
In order to protect the computer network, organizations emphasize on implementing hardware and software application as well as a framework in terms of surveillance security. Network security issues can lead to many different aspects. For example, if the server containing customer data is breached, organization will lose its credibility and trust among the customer and that will result in business loss. Similarly, if a critical system storage device is stolen by internal or external sources, organization’s financial data along with goals and objectives can be revealed to other competitors. In the proposed network design for Big switch, surveillance security is incorporated for protecting unauthorized access to switches located at each department. The surveillance security will provide following features:
- It will track unauthorized access of employees to departments
- Monitor activities of employees related to physical interference with critical hardware components
- User activity on the network and unusual behaviors will be monitored
- User authentication and Authorization will be implemented
- IP cameras to monitor their critical information assets on the network.
Addressing Deployment Approach for Departments
Star topology is recommended for the wired local area network. It is the most widely adopted topology. The star topology supports the centralized provision of network resources and services. The support staff can manage the network administrative and troubleshooting tasks centrally. Star topology helps to implement centralized security architecture for improved and enhanced security of the network. The network implementation cost can be saved by provisioning the core systems located centrally. The security controls and backup systems are also located centrally for better troubleshooting and management.
For deploying the local network for Big switch, CAT 5 cable is the best option. It supports both voice and data transmission. CAT-5 is in the form of twisted pairs. This cable consists of 4 copper wire pairs, connecting the network node with RJ 45 connectors.CAT-5 supports up to 100 to 1000 MHz speeds in a ‘full duplex’ mode (Category 5 cable.2007). The Big switch enterprise network will corresponds to request related to internet applications, online transactions, requests by sale contractors, file transfer protocol and Emails. CAT 5 can support these features with ease. However, CAT 5 cable can support up to 300 feet equal to 100 meters in distance. A requirement of the switch is mandatory for every 300 feet.
Data switches perform packet distribution tasks within the local area network. Acting as a core backbone, Big switch network requires fast Ethernet switches to support the internet and external communication. The Cisco Catalyst 3750 v2 series switch is recommended to cater the requirements for the current scenario as well as for the future. The deployment of switches will be carried out by disconnecting one department at a time on a non-working day, as the installation will be conducted by the vendors or the staff available at big Switch. From each of these available departments, human resource department will be the first one to be replaced with the new switch supporting VLAN and addressing security issues. The next department will be the technology department itself for enabling compatibility with the human resource department switch, as proper configuration and testing is required. Each department follows the similar approach with finance department to be the last one.
Cisco Catalyst 3750 is the OSI layer 3 stackable switch, supporting the energy efficiency factor. Stackable means that more switches can be added to the current switch configuration for providing more network nodes. This switch supports the Cisco Energy Wise technology, which assist in the provision of power management of the big switch network. At the same time, the Cisco energy wise technology reduces the cost and carbon foot prints. The latest invention to the energy wise technology is the ‘Cisco EnergyWise’ Orchestrator which is a dedicated turnkey power management solution for the network and information systems. The Cisco Energy Wise Orchestrator enables to administer the energy requirements of Power over Ethernet (POE) enabled devices. It also extends the enterprise power management to workstations and laptops (Newswire, 2012).
Conclusion
We have incorporated six layer 3 Cisco Catalyst 3750 v2 manageable switches for operational effectiveness and efficiency for the internal network functionality. Moreover, two Cisco 3845 Integrated Services routers that are connected to establish a perimeter network along with a bastion host for detecting anomalies. Furthermore, we have also proposed a surveillance framework that will record and main access logs for employees entering and exiting departments containing critical network appliances such as switches, routers and data storage devices.
References
Category 5 cable. (2007). Network Dictionary, , 88-88.
Newswire, P. (2012). Server technology’s intelligent rack mount power distribution units now cisco® EnergyWise™ certified. PR Newswire US,
Network security at the data link layer (layer 2) of LAN Retrieved 7/15/2012, 2012, from http://www.javvin.com/networksecurity/NetworkSecurity.html
Tiso, J.Designing cisco network service architectures (ARCH) foundation learning guide: (CCDP ARCH 642-874) (3rd edition) (foundation learning guides) Cisco Press.

Stuck with your Essay?
Get in touch with one of our experts for instant help!

Time is precious
don’t waste it!
writing help!


Plagiarism-free
guarantee

Privacy
guarantee

Secure
checkout

Money back
guarantee

