Network Security Design: A Case Study Analysis on the Network Systems of Global Finance INC, Research Paper Example
Introduction
In the face of modern technology and communication systems, it has become a key source of confidence for modern business organizations to create established IT systems that would define their operations. Lately, IT has become a great source of defense and confidence in relation to the capacity of the organization to expand their capability to operate. The expansion of their operation however would be dependent on their ability to become more global based on the confidence of the IT systems that they are to use. Making a great impact towards the world’s business systems specifically make a definite indication of the possibility of expansion that a particular organization hopes to incur.
In this particular case, an assessment of Global Finance Inc’s network system shall be given attention to. The operation of the business based on its network specifically situated in the internet shall be given specific examination. Looking through the system’s structure and understanding the risks that it posts for the operation of the business in relation to its connection with its users and other stakeholders in the internet. The assessment of these risks shall be utilized to identify the possibility by which the modern businesses are supposed to operate in relation to their desire of extending their operation in connection to the being of the organization in the face of international business competitions.
The Current Company Network
GFI or Global Finance Inc is one of the fastest growing financial organizations that is specifically making a great impact in the face of commercial industry especially in relation to international operations. What makes this institution a strong source of industrial confidence is the fact that it is able to make a distinctive approach in making a relative connection to the world especially in the aspect of serving the general needs of their clients coming from the different parts of the globe. Relatively, such condition of operation calls for an expansive system that could regulate activity that simultaneously occurs through the internet. Undeniably, such system of operation requires high maintenance especially in relation to the kind of security that the network has to be dependent upon. Considering that it serves a set of clients from the global scene, the security protection should be relatively based on a 24-hour operation, which could assure that the network would not be invaded by any particular disturbance from its outside users.
The optimal performance of the network system is based upon the desire of the institution to serve as much clients as possible. Relatively, the need for an operative system that would be able to comprehend with the rate of activity that comes in as supported by the bandwidth that the institution uses. It is with this particular sense of understanding that makes a distinctive indication that the organization specifically needs a strongly protected network that would help avoid the instance by which invaders would be able to access to important and confidential information stored in their database.
There are currently several divisions of specific operations that GFI’s servers intend to host. The financial services that the business offers are all stored in the main database and are accessible to both the internal operators [such as financial advisers] and the direct external users [mainly the clients]. The vulnerability of the system to possible invaders and hackers may actually have a great impact on how the organization operates in an overall aspect. Relatively, the capacity of the business to continue catering to the enlarging group of clients that are hoping to be served by the company. Understandably, protecting all the division of operations that the company holds means protecting the business as a whole. To be able to do this, setting up a firewall protection within the current system that the organization uses is essential. It is not enough that the number of personnel monitoring the ongoing activities in the network be increased. The focus of the operational development should be more dependent on how the information kept in the database ought to be protected based on coding and filter systems that are supposed to establish specific authorization system that would only allow authenticated codes to access specific information. To further asses the capacity of the current network of GFI to handle the incoming activities from its primary stakeholders, a SWOT analysis is presented herein:
Strengths
The specific divisions that are included in the system define the network’s capacity to welcome several activities and define their impact on the business’ operation based on an overall assessment. This means that the establishment of these divisions specifically allows massive activities to occur simultaneously within the network. The systematic operation by which the set of information have been specifically divided into gives an indication that the administration has already managed to set a supposed design on how to direct their clients and other stakeholders and users of the network towards the specific service that they hope to be served with.
Weaknesses
With the wide systems of operation that the network has to consider in relation to its connective servers specifically situated in the internet, it could not be denied that the possibility of having the need to deal with malicious users is a constant fear that must be managed through an established security system.
Opportunities
In relation to the instances by which the institution serves its internal and external stakeholders, it is a great opportunity for GFI to provide a more specific system of operation that would relatively create a definite indication of service that would provide a constructive reputation for the organization itself. What makes the organization more effective is that of its capability to provide the service that the clients specifically need. This situation gives the organization the opportunity to make a distinctive source of confidence especially in establishing a rate of correlative reputation in becoming one of the most competent financial institutions in the industry.
Security is an outmost concern for most clients of the financial industries. This is especially true when it comes to the manner by which the modern industry of financial advice and operations tend to establish a name. What makes this opportunity specifically effective especially when it comes to reestablishing the name of the business in connection to secured operations is that of its capacity to make GFI a reputable institution to complete their transactions with. The opportunity of becoming a more defined organization that is respected and trusted by the market shall provide GFI a more marketable service in the industry.
Threats
Even though the network system of GFI I s effectively organized, its weakness based on security measures specifically endangers the directive operations engaged in by the business in relation to its clients and its internal connections as well. Aside from this particular situation, the growth of the institution is also threatened by the fact that there are other organizations that are coming into the industry and they are ready to hold more relative indications of more secured services.
Based on this particular SWOT analysis, it could be seen how GFI tends to provide great service to its clients through internet-based operations that is networked towards the main servers of the business. Although the aim of service is based on the most prominent services needed by their target market, it could be seen how the issue of network security specifically hurts such kind of operational excellence. Some of the most specific risks that the organization should look after shall be further discussed in the section that follows.
Risks of Unsecured Network
In consideration with the nature of services that GFI is engaged with, it could be realized that the issues of security could be connected to the need of protecting the personal data that the clients share as they chose to transact with the organization through an open network in the internet. The threat of dealing with identity thieves specifically make a specific source of concern for those who GFI hopes to serve in the market. People who are willing to transact in the internet should also be willing to share personal and private information about themselves. However, getting such willingness from clients is not an easy path to consider. Most likely, such condition has become a source of issue for most individuals engaging in online transactions. This is the reason why establishing a more secured network is essential especially when it comes to convincing clients that they could trust the system hence making it easier for the clients to decide in closing the deal with the company. Among the other risks that the company should be ready to face in connection with having an unsecured network could be accounted for as follows:
(a) Malicious transfer of information from the database to personal computers of malicious users
Because of an unprotected network system, it would be easy for malicious users to transfer information from the database into another storage system directly. This could endanger the whole system especially in consideration with the division of the information that the administration uses to define the data that they are storing in the system. Realizing this risk, the organization must know how to mandate the manner by which individuals from outside the institution intend to utilize the information they get from the company’s website. Unauthorized individuals who are allowed to enter the premises of the system’s private network should be redefined accordingly.
(b) Downloading of important information about the company and its clients through a remote access
Downloading information such as forms and database codes should be well protected. Not securing such activity form being used maliciously against the company would result to massive conditions of information breech thus creating a system laps on the direction by which the function of the website is managed.
(c) Hacking of transactions and even money transfer systems that would benefit online hackers
Transactions made and kept online for storage are supposed to be firewalled. Of course, this is a protocol in defining a networked website through the internet. However, not providing enough firewall for such information would not only endanger the established business transaction between the company and its clients but could also make a specific breach on the contracts formed between the said two parties.
(d) Loss of business edge and business intelligence to competition
When companies standing as competitors of the organization use the said weakness as their source of business competence, the organization [GFI] might lose particular intelligence that serves as the business’ asset in the industry. This could include programs that are shared between organizational operators who are aiming to make a distinctive system of connection in the aim of creating a more relative system of institutional domain that could serve the best interests of the market that they serve.
(e) Loss of Goodwill
Once the information shared between the clients and the company becomes endangered through malicious users, the goodwill that the parties mentioned share shall diminish. This means that the trust of the clients on the company’s capacity to serve their needs will be jeopardized. It should be remembered that things like this becomes an easy source of reputation-breakdown for most business organizations hence resulting to slow-death when it comes to the growth that the organizations hope to pursue.
(f) Legal and Financial risks
When information shared by the clients are shared through an unscrupulous manner, then the company faces specific points of legal sanctions. This could hinder the organization’s growth and all the more redefine the situation by which the organization is able to serve its function to the market it hopes to offer services to. The name of the whole organization will be compromised and its position in the market shall be under specific scrutiny for a long time.
Defense of Assumptive Risks
The risks that were presented in this section provide a great source of information as to what specific dangers the company network faces as it opens up to new edges of connecting to its clients through the worldwide web. Operators of the network, although they are well trained and are expected to do a good job, cannot fully handle the rate of activity that is supposed to be handled by the capacity of the website’s bandwidth. Since the operation of the business is held online, it is expected that the activity that would be coming in shall be ongoing for a span of 24 hours every day. In this case, the personnel assigned to monitor such activities need to undergo shifting duties. The process of handling such job with efficiency may not be that easy to consider especially in relation to the risk of losing track on some of the hidden activities of expert hackers in the web.
To help in the process, a good system of network firewall and coding should then be created specifically to establish the security of the company’s website. It is suggested herein then that the application of a network layer or packet filters be considered by the administration. Not only will this approach lessen the burden of monitoring the activity of users entering the website but it will also redefine the capacity of the network system to protect itself from malicious activities promulgated by scrupulous users. It should be realized that when it comes to hacking, there are those operations that simply make it hard for human monitoring personnel to identify malicious activities as they happen. This is why an automatic network alarm should be created so as to make it easier for monitors to identify unauthorized downloading and manipulation of information in the website that could affect the main data storage of the server.
Vulnerabilities of Network Security
When a network of information is shared through a public portal such as the internet, it immediately becomes vulnerable to risks. These risks [as mentioned in the previous section] would not only cost the business’ operation in the industry but also that of its reputation that stands to be the basis of its face in the market. Relatively, this will jeopardize any chance of growth that the company aims to embrace in the future. The market, being warned that the organization was not able to withstand a security breach in the past, may not be as trusting as it is supposed to be especially when it comes to creating and closing transactions with the business through online connections.
For the case of GFI, knowing that their operation in the worldwide web is vastly growing and is becoming a distinctive source of confidence for the whole organization, securing their operation is a must. Surely , they would not want what they have worked hard for a long time be subjected to social scrutiny just because of a single issue on security and information protection. True, such condition of assuring website security might mean a relative amount of investment. Nevertheless, making a distinctive move on assuring such source of confidence on the part of their clients would amount to more profit in the future and a better established name that would provide the company the chance to expand further. The adjustments that need to be made for the sake of accepting the changes that a new system of a protected network shall impose should be considered accordingly hence making sure that an investment dedicated to network security would give more confident business transactions between GFI and its clients in the market.
Suggestions for Risk Mitigation
Establishing network layer firewalls is assumed to be the best choice of security for GFI. Considering the current structure of the network it uses for internet operations, it is seen that the division of information it stores within its database could be best protected through layer firewalls. This TCP/IP protocol would provide the network a sense of layered protection especially in relation to what specific type of user is to be given authorization to access the information kept within a certain division of the network. Creating codes of commands that would establish specificity of access shall not only make the navigation of the website easier for users but shall also secure information that is not supposed to accessed by a certain user.
As of now, the company’s operational and administrative network is divided into three aspects namely that of the accounting department, the loan department and the customer service department. Allowing users to enter the website only based on their needs shall protect the other data that are not connected to their interest away from being exploited accordingly. The operators of the said departments are also to be given authorization ids that they are supposed to use when they are to access the company system when needed. Clients coming in for the first time shall be granted visitor passes when they are already in need of accessing confidential business forms that they wish to sign for the sake of transacting with the organization. Relatively, this will lead them to downloading the correct forms and submitting them back in the correct portals hence making transactions easier to monitor.
Accordingly, a hierarchical arrangement of authentication shall be followed. Not all administrators are given the chance to see what the other departments are supposed to handle in their own networks. This will not only establish protection on the part of the information being kept in the database, but it will also provide focus on the department heads of the organization as to what issues they should be able to handle accordingly in relation to the overall operation of the business in the internet.
Redrawing the Diagram
The following illustration of protection shall be embedded with the existing diagram of networking operations of GFI:
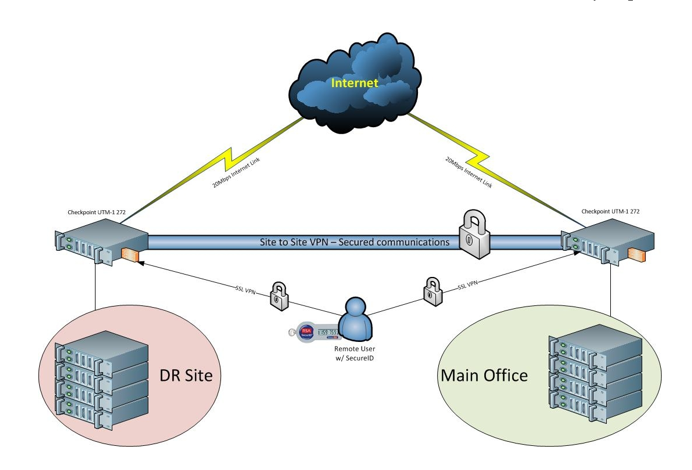
This system is expected to provide a more protective system of website navigation both to the public users and the administrators of the business as they intend to establish online transactions and to close up deals through the internet. Observe that the locked connections indicate an authorization system protocol that would require users to encode in some codes provided by the website monitors every time they would like to access particular private information stored in the company’s database.
Conclusion
Just like in mortar-and-brick businesses, gates and locks are used to protect the important files and properties of an organization. In the internet, the same rule applies. To protect the name, the reputation and the connection of the business with its clients, it is also important to establish security. Especially in the aspect of dealing with global clients without actually physically dealing with them, the need for such protection is vital. Based on this discussion, GFI would best be able to depend on a secured website system if it is ready enough to mandate change that would affect its overall operation in connection to the current operation that it hopes to present its clients with. With such an investment of creating a firewall program for the website, more profit is expected to come in based on customer loyalty and trust.
References:
Ingham, Kenneth; Forrest, Stephanie (2002). “A History and Survey of Network Firewalls” (pdf). http://www.cs.unm.edu/~treport/tr/02-12/firewall.pdf. (Retrieved on March 14, 2013).
Chang, Rocky (October 2002). “Defending Against Flooding-Based Distributed Denial-of-Service Attacks: A Tutorial.”. IEEE Communications Magazine 40 (10): 42–43.
Cheswick, William R., Steven M. Bellovin, Aviel D. Rubin (2003). “Google Books Link“. Firewalls and Internet security: repelling the wily hacker. http://books.google.com/books?id=_ZqIh0IbcrgC&lpg=PA142&dq=Firewalls%20and%20Internet%20Security%2C%20by%20Cheswick%20et%20al.&pg=PA176#v=onepage&q=Firewalls%20and%20Internet%20Security,%20by%20Cheswick%20et%20al.&f=false. (Retrieved on March 14, 2013).
Conway, Richard (204). Code Hacking: A Developer’s Guide to Network Security. Hingham, Massachusetts: Charles River Media. pp. 281.
Oppliger, Rolf (May 1997). “Internet Security: FIREWALLS and BEYOND“. Communications of the ACM 40 (5): 94.

Time is precious
don’t waste it!

Plagiarism-free
guarantee

Privacy
guarantee

Secure
checkout

Money back
guarantee






