 All papers examples
All papers examples
Disciplines

- MLA
- APA
- Master's
- Undergraduate
- High School
- PhD
- Harvard
- Biology
- Art
- Drama
- Movies
- Theatre
- Painting
- Music
- Architecture
- Dance
- Design
- History
- American History
- Asian History
- Literature
- Antique Literature
- American Literature
- Asian Literature
- Classic English Literature
- World Literature
- Creative Writing
- English
- Linguistics
- Law
- Criminal Justice
- Legal Issues
- Ethics
- Philosophy
- Religion
- Theology
- Anthropology
- Archaeology
- Economics
- Tourism
- Political Science
- World Affairs
- Psychology
- Sociology
- African-American Studies
- East European Studies
- Latin-American Studies
- Native-American Studies
- West European Studies
- Family and Consumer Science
- Social Issues
- Women and Gender Studies
- Social Work
- Natural Sciences
- Anatomy
- Zoology
- Ecology
- Chemistry
- Pharmacology
- Earth science
- Geography
- Geology
- Astronomy
- Physics
- Agriculture
- Agricultural Studies
- Computer Science
- Internet
- IT Management
- Web Design
- Mathematics
- Business
- Accounting
- Finance
- Investments
- Logistics
- Trade
- Management
- Marketing
- Engineering and Technology
- Engineering
- Technology
- Aeronautics
- Aviation
- Medicine and Health
- Alternative Medicine
- Healthcare
- Nursing
- Nutrition
- Communications and Media
- Advertising
- Communication Strategies
- Journalism
- Public Relations
- Education
- Educational Theories
- Pedagogy
- Teacher's Career
- Statistics
- Chicago/Turabian
- Nature
- Company Analysis
- Sport
- Paintings
- E-commerce
- Holocaust
- Education Theories
- Fashion
- Shakespeare
- Canadian Studies
- Science
- Food Safety
- Relation of Global Warming and Extreme Weather Condition
Paper Types

- Movie Review
- Essay
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- GCSE Coursework
- Grant Proposal
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- Essay
- GCSE Coursework
- Grant Proposal
- Interview
- Lab Report
- Literature Review
- Marketing Plan
- Math Problem
- Movie Analysis
- Movie Review
- Multiple Choice Quiz
- Online Quiz
- Outline
- Personal Statement
- Poem
- Power Point Presentation
- Power Point Presentation With Speaker Notes
- Questionnaire
- Quiz
- Reaction Paper
- Research Paper
- Research Proposal
- Resume
- Speech
- Statistics problem
- SWOT analysis
- Term Paper
- Thesis Paper
- Accounting
- Advertising
- Aeronautics
- African-American Studies
- Agricultural Studies
- Agriculture
- Alternative Medicine
- American History
- American Literature
- Anatomy
- Anthropology
- Antique Literature
- APA
- Archaeology
- Architecture
- Art
- Asian History
- Asian Literature
- Astronomy
- Aviation
- Biology
- Business
- Canadian Studies
- Chemistry
- Chicago/Turabian
- Classic English Literature
- Communication Strategies
- Communications and Media
- Company Analysis
- Computer Science
- Creative Writing
- Criminal Justice
- Dance
- Design
- Drama
- E-commerce
- Earth science
- East European Studies
- Ecology
- Economics
- Education
- Education Theories
- Educational Theories
- Engineering
- Engineering and Technology
- English
- Ethics
- Family and Consumer Science
- Fashion
- Finance
- Food Safety
- Geography
- Geology
- Harvard
- Healthcare
- High School
- History
- Holocaust
- Internet
- Investments
- IT Management
- Journalism
- Latin-American Studies
- Law
- Legal Issues
- Linguistics
- Literature
- Logistics
- Management
- Marketing
- Master's
- Mathematics
- Medicine and Health
- MLA
- Movies
- Music
- Native-American Studies
- Natural Sciences
- Nature
- Nursing
- Nutrition
- Painting
- Paintings
- Pedagogy
- Pharmacology
- PhD
- Philosophy
- Physics
- Political Science
- Psychology
- Public Relations
- Relation of Global Warming and Extreme Weather Condition
- Religion
- Science
- Shakespeare
- Social Issues
- Social Work
- Sociology
- Sport
- Statistics
- Teacher's Career
- Technology
- Theatre
- Theology
- Tourism
- Trade
- Undergraduate
- Web Design
- West European Studies
- Women and Gender Studies
- World Affairs
- World Literature
- Zoology
Physical Security, Essay Example
Hire a Writer for Custom Essay
Use 10% Off Discount: "custom10" in 1 Click 👇
You are free to use it as an inspiration or a source for your own work.

Question 1
What elements would you include in providing a layered security system for a three-building corporate campus that includes a five-story building housing a financial services company in the following scenario?
The campus is located adjacent to a river that flows into Chesapeake Bay and sits on ground 8 feet above sea level. The building is in a suburban location, sited on approximately five acres adjacent to an interstate highway ramp. Parking is included within the campus boundary and approximately 250 employees are present daily, plus approximately 50 visitors.The loading docks can be accessed from the parking lot via side roads.
Building 1 contains the headquarters offices of the financial service company; Building 2 contains the physical files and computer equipment room; and Building 3 holds administrative offices and storage facilities.The computer room is in the basement to provide a cool operating environment. The storage facilities hold equipment and supplies used to maintain the grounds.
See the map on the next page. Light poles are indicated by the “+” symbol.
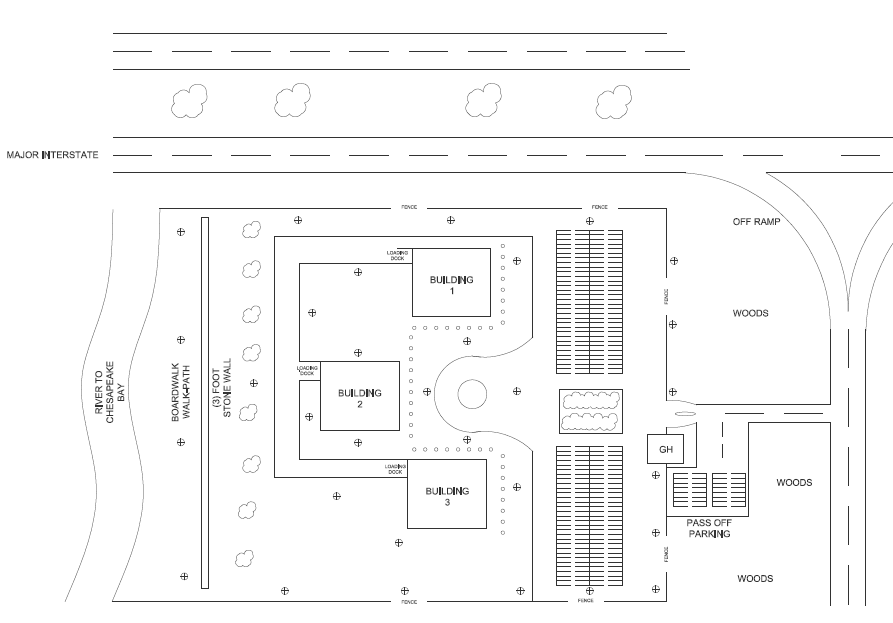
Access to university campuses during business hours is typically open to the public. With the exception of certified employment access to the various limited access locations located in the computer room in the basement and storage facility, and also buildings 1, 2, and 3, the headquarters offices of the financial service company; physical files and computer equipment room; and administrative offices and storage facilities respectively, no particular form of security beyond video cameras will likely be employed during daylight hours. During the evening hours, weekends and holidays, campus closure must be secured with limited access cards allocated to employees.
Smart cards present the most viable option to a multilayered security environment with little option for total physical enclosure. Although 6’ fencing, security windows of double to triple thickness, and multiple locking systems should be built into infrastructure of the entire campus, additional security might be added to the financial services building and the mainframe computer environment. Electronic lifting steel barriers at entrances for vehicle passage should be active for control to parking access in no-visitor areas at all times. Much of the physical security of the campus might be best monitored and secured with biometric cards that enable the embedding of unique identification of personnel into the cares for optimum reliability in control of credential. Biometric proponents cite that biometrics cost equivalent to the more used radio frequency identification (RFID) cards on the market.
The smart cards offer easy swipe entrance into secured locations, and can of course be limited according to range of identified credentials within each individual profile. The cards make everything from entrance into an enclosed area by car, parking, and also access to designated buildings and elevators according to level of access ensured by allocation of university administration. Remote sensing capabilities connected to the cards must be also be monitored as information might be modified by satellite. Furtherance of surveillance on the campus might include thermal imaging technologies (i.e. infrared cameras) for night security in high security areas related to information control.
Question 2
What CPTED strategies would you use for a typical hospital? Consider the area around the building(s) as well. Be sure to refer to the CPTED principles stated in the lecture notes.
Do not use outside resources except for gathering background information about hospitals in general.
The architectural design of most hospital environments tends to incorporate a high degree of control in terms of access nodes, and thoroughfare channels that might be reached by the public. External qualities to hospital construction share much of the institutional material (i.e. security windows) inputs akin to other institutions seeking a high degree of security despite public access (i.e. universities). If hospitals seek basic Crime Prevention Through Environmental Design (CPTED), they also employ a range of strategies for protection of patients and IT systems integral to patient care. Healthcare Management Information Systems (HMIS) IT interfaces can be augmented with a number of standardized security architectures, dependent upon the types of platforms controlling database and distributed control system (DCS) (i.e. chemicals) within the network. Hazard zones subject to regulatory management by OSHA must be marked with signage, and also monitored according to the institution’s risk assessment and management protocol.
The Health Insurance Portability and Accountability Act (HIPAA) set the framework for privacy and security regulations in the US healthcare industry, and sets established standards for the global e-health industry. Hybrid Public Key Infrastructure (HPKI) solutions comply with HIPAA regulations as cryptographically strong PKI schemes are deployable for mutual authentication and distribution of sensitive yet computational non-intensive data; at the same time efficient symmetric cryptographic technology is available for storage and transmission of high volume of medical data like medical images.
Due to the high security focus of all retention of integrity and non-disclosure factors within patient record, technological security is heightened as lead institutions begin to expand HMIS toward linking insurance providers, patients, specialists, suppliers and the entire referral network into their systems. The utilization of smart cards is again prevalent here, as either biometric or radio frequency identification (RFID) cards allow for maximum control over the physical environment, while offering different levels of access to information and data distribution pertaining to care of patients. Traditional security locking equipment, medication, syringes will of course be present, and can require digital signatory for access and dual locked with both key and card security. Video cameras within the internal and external environment will be monitored around the clock at all points within the facility as protection of patients is linked to institutional liability to a duty of a standard of care within physician-patient law.
Question 3
Report the findings of a comprehensive physical security risk assessment of the facilities (A Large auto dealer (such as CarMax)) listed — be sure to address each of the basic elements of the assessment process.
Large auto dealer (such as CarMax)
Do not use outside resources except for gathering background information about the facility.
Auto dealers in urban setting are designed for maximum security of property. Due to the fact that city dealers typically store vehicles in a multistoried parking lot, control of movement is relatively easy in that physical control of entrance and exit ramps can be achieved by actual raised barriers with limited employee access outside of business hours. Video cameras offer security guards universal monitoring capacity. Vehicles can be locked with keys that are then locked in a secure area of the administrative offices in the showroom, and additional physical security such as tire boots and steering wheel blocks might be employed in high crime areas. Showroom windows contain electronic alarm facility to warn would be intruders upon touch or proximity in the case of infrared systems.
Car dealers that inventory vehicles on outdoor lots use similar strategies, and typically chain the area with iron posts. In all models of the auto dealer showroom and inventory facility, employees might be provided smart cards as an option for control of building and other access. Limited use of keys at auto dealer facilities, if nothing else, might lead to reduction of minor property damage. Fortunately, unlike clinical and urgent care settings, most of the damage caused on location at auto dealers is property related, and not pertaining to direct human impact. Indemnity of property allows for less concern. Still, cyber-security of inventory and fiscal information toward ensured privacy of audit and protection against corporate espionage (i.e. competitor spying) is substantial.
References
Biringer, B.E. et al. (2007). Security Risk Assessment and Management: A Professional Practice Guide for Protecting Buildings and Infrastructures. Hoboken, NJ: Wiley.
Demkin, J.A. (2003). Security Planning and Design: A Guide for Architects and Building Design Professionals. Hoboken, NJ: Wiley

Stuck with your Essay?
Get in touch with one of our experts for instant help!
Tags:

Time is precious
don’t waste it!
writing help!


Plagiarism-free
guarantee

Privacy
guarantee

Secure
checkout

Money back
guarantee

