 All papers examples
All papers examples
Disciplines

- MLA
- APA
- Master's
- Undergraduate
- High School
- PhD
- Harvard
- Biology
- Art
- Drama
- Movies
- Theatre
- Painting
- Music
- Architecture
- Dance
- Design
- History
- American History
- Asian History
- Literature
- Antique Literature
- American Literature
- Asian Literature
- Classic English Literature
- World Literature
- Creative Writing
- English
- Linguistics
- Law
- Criminal Justice
- Legal Issues
- Ethics
- Philosophy
- Religion
- Theology
- Anthropology
- Archaeology
- Economics
- Tourism
- Political Science
- World Affairs
- Psychology
- Sociology
- African-American Studies
- East European Studies
- Latin-American Studies
- Native-American Studies
- West European Studies
- Family and Consumer Science
- Social Issues
- Women and Gender Studies
- Social Work
- Natural Sciences
- Anatomy
- Zoology
- Ecology
- Chemistry
- Pharmacology
- Earth science
- Geography
- Geology
- Astronomy
- Physics
- Agriculture
- Agricultural Studies
- Computer Science
- Internet
- IT Management
- Web Design
- Mathematics
- Business
- Accounting
- Finance
- Investments
- Logistics
- Trade
- Management
- Marketing
- Engineering and Technology
- Engineering
- Technology
- Aeronautics
- Aviation
- Medicine and Health
- Alternative Medicine
- Healthcare
- Nursing
- Nutrition
- Communications and Media
- Advertising
- Communication Strategies
- Journalism
- Public Relations
- Education
- Educational Theories
- Pedagogy
- Teacher's Career
- Statistics
- Chicago/Turabian
- Nature
- Company Analysis
- Sport
- Paintings
- E-commerce
- Holocaust
- Education Theories
- Fashion
- Shakespeare
- Canadian Studies
- Science
- Food Safety
- Relation of Global Warming and Extreme Weather Condition
Paper Types

- Movie Review
- Essay
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- GCSE Coursework
- Grant Proposal
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- Essay
- GCSE Coursework
- Grant Proposal
- Interview
- Lab Report
- Literature Review
- Marketing Plan
- Math Problem
- Movie Analysis
- Movie Review
- Multiple Choice Quiz
- Online Quiz
- Outline
- Personal Statement
- Poem
- Power Point Presentation
- Power Point Presentation With Speaker Notes
- Questionnaire
- Quiz
- Reaction Paper
- Research Paper
- Research Proposal
- Resume
- Speech
- Statistics problem
- SWOT analysis
- Term Paper
- Thesis Paper
- Accounting
- Advertising
- Aeronautics
- African-American Studies
- Agricultural Studies
- Agriculture
- Alternative Medicine
- American History
- American Literature
- Anatomy
- Anthropology
- Antique Literature
- APA
- Archaeology
- Architecture
- Art
- Asian History
- Asian Literature
- Astronomy
- Aviation
- Biology
- Business
- Canadian Studies
- Chemistry
- Chicago/Turabian
- Classic English Literature
- Communication Strategies
- Communications and Media
- Company Analysis
- Computer Science
- Creative Writing
- Criminal Justice
- Dance
- Design
- Drama
- E-commerce
- Earth science
- East European Studies
- Ecology
- Economics
- Education
- Education Theories
- Educational Theories
- Engineering
- Engineering and Technology
- English
- Ethics
- Family and Consumer Science
- Fashion
- Finance
- Food Safety
- Geography
- Geology
- Harvard
- Healthcare
- High School
- History
- Holocaust
- Internet
- Investments
- IT Management
- Journalism
- Latin-American Studies
- Law
- Legal Issues
- Linguistics
- Literature
- Logistics
- Management
- Marketing
- Master's
- Mathematics
- Medicine and Health
- MLA
- Movies
- Music
- Native-American Studies
- Natural Sciences
- Nature
- Nursing
- Nutrition
- Painting
- Paintings
- Pedagogy
- Pharmacology
- PhD
- Philosophy
- Physics
- Political Science
- Psychology
- Public Relations
- Relation of Global Warming and Extreme Weather Condition
- Religion
- Science
- Shakespeare
- Social Issues
- Social Work
- Sociology
- Sport
- Statistics
- Teacher's Career
- Technology
- Theatre
- Theology
- Tourism
- Trade
- Undergraduate
- Web Design
- West European Studies
- Women and Gender Studies
- World Affairs
- World Literature
- Zoology
The DNS Server, Essay Example
Hire a Writer for Custom Essay
Use 10% Off Discount: "custom10" in 1 Click 👇
You are free to use it as an inspiration or a source for your own work.

DNS server Benefits
As we have already selected a domain environment for Jane and Kim’s network, now there is a requirement of setting up a DNS server. DNS server has various benefits and organizations prefer to maintain DNS servers for their internal computer networks rather than relying on ISP DNS servers that are slow and may become vulnerable. Primary reason for maintain a private DNS server ensures security, reliability, robustness and consistency. In order to provide security, all the employees will access the DNS server via 128 bit encryption with SSL connections. Moreover, security controls must be up to date on the servers, for instance, security patches. DNS servers also provide error checking so that websites can be resolved without disruption. Moreover, network administrators can manage many Internet domains and sub domains (Benefits and features of DNS for your server, n.d). As Jane and Kim’s network is connected to an Internet gateway, DNS server is required to resolve IP addresses in to host names. Likewise, DNS server is also required for identifying network nodes. For instance, if any user wants to share a file, DNS will resolve the IP address of that computer to a specific computer name that is easy to understand. Moreover, DNS server will also maintain host names and IP addresses and all the computers available on the network. If we move one step further, step by step process for a typical DNS process consists of a file that is transmitted to a specific location i.e. on the Internet or computer within the network, the request will initially reach to the DNS server for translating hostname to IP addresses. After retrieving the required IP address, connectivity will be established for transferring the file. DNS server is recommended because it will provide security, reliability and fast access to web requests. For instance, if any user wants to open a website, web request will initially ask the DNS to resolve the names in to numbers. If an organization does not have a DNS server, web request will reach the DNS server of the ISP that will consume time.
There are some issues related to DNS servers that clients may face. For instance, DNS server stops responding to client’s request. The cause for this issue is due to a network failure. Solution will be to check the connectivity of DNS server with the local network, check the Ethernet system software or physical hardware status and perform basic troubleshooting procedures for restoring services. In order to test the effectiveness of a DNS server, network administrators can execute ‘nslookup’ command, as there are issues related to restricting certain IP addresses. Restrictions were applied in a testing phase and were not removed since then (Troubleshooting DNS servers: Domain name system (DNS), n.d ).
DNS servers are exposed to threats if all issues and proper configuration options are not addressed. Threats may involve foot printing, redirection, cache pollution and Denial of Service (DOS) attacks. Foot printing is a type of a threat that retrieves resource records of specific servers of an organization from the DNS server (Snedaker, Shinder, & Shinder, 2004). After getting the resource records, attackers successively attacks these system and find out the purpose of these systems in an internal network. Vulnerability for this threat triggers when zone transfers are not protected. If the zone transfers are not secure, attacker may initialize a name dump that can be executed from authoritative servers. Likewise, ‘nslookup -ls’ command is executed to successfully perform this attack (Snedaker, Shinder, & Shinder, 2004). Cache pollution is another threat that can be achieved by recursion to query the locally configured DNS server for targeting resources that are located in the attacker’s domain. Mitigation can be done by deactivating recursion option from the DNS server. Furthermore, Denial of service attacks are performed, when the DNS server is overloaded or receiving many requests and denies any further request for translation. At this point, attackers can use a TCP/UDP port 53 for buffer overflow. However, counter measures are to configure two or more DNS servers for this purpose, so that if anyone of them is compromised, it can be isolated and there will be no operational and business impact (Snedaker, Shinder, & Shinder, 2004).
DNS Installation
After installing Active Directory, step by step guide of DNS server installation is illustrated below:
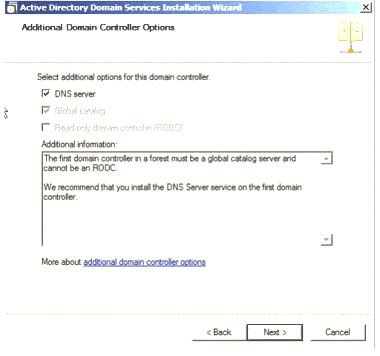
Figure 1.1
Click on the ‘Active Directory Services Installation Wizard’, options will appear, as shown in Fig 1.1. Click ‘Next’
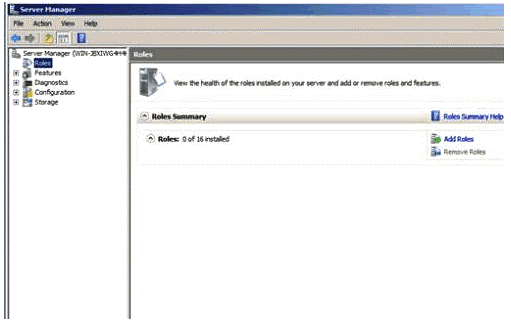
Figure 1.2
Expand and click on the option named as‘roles’, as specified in Fig 1.2
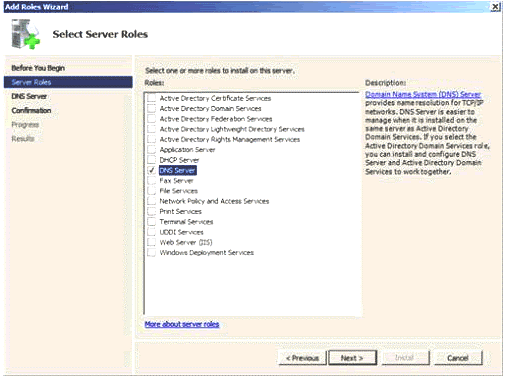
Figure 1.3
Select ‘Add Roles’ and select DNS role in order to execute a wizard, as shown in Fig 1.3.
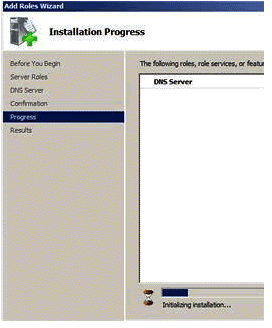
Figure 1.4
Install the DNS Server, as shown in Fig 1.4
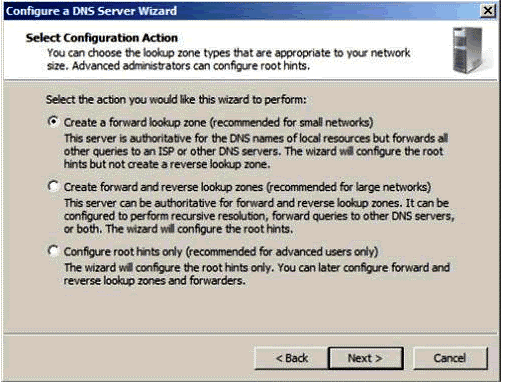
Figure 1.5
As shown in Fig. 1.5, forward lookup zone will only be used for address resolution. Forward and reverse lookup zone facilitates the DNS server to discover host names. Lastly, root hints are easy to configure and contains overall DNS server functionality. Click next to create a ‘forward lookup zone’.
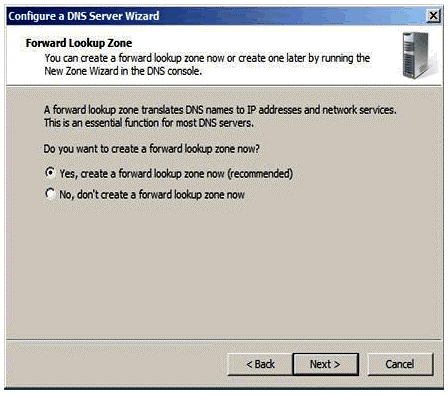
Figure 1.6
Click ‘yes’ to create the forward lookup zone
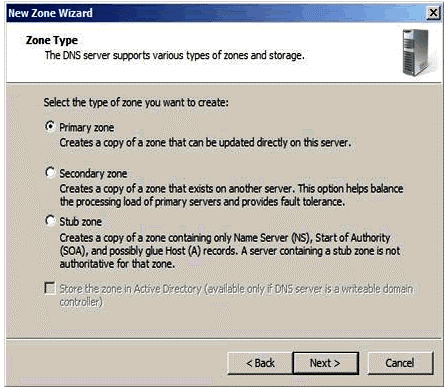
Figure 1.7
As shown in Fig 1.7, a primary and secondary option requires active directory installation and the stub zone option is for load balancing. As we have considered a domain environment, primary zone will be selected.
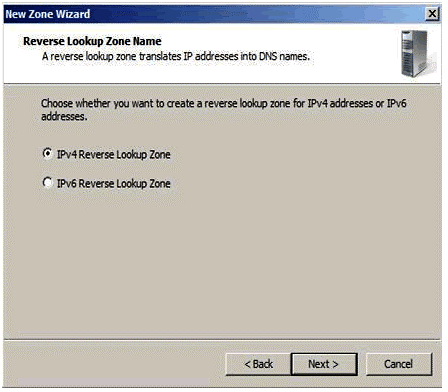
Figure 1.8
It depends, whether the network infrastructure is based on IPv4 or IPv6. User will select the options that are identical to the network.
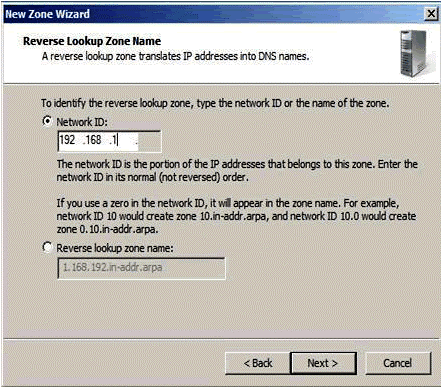
Figure 1.9
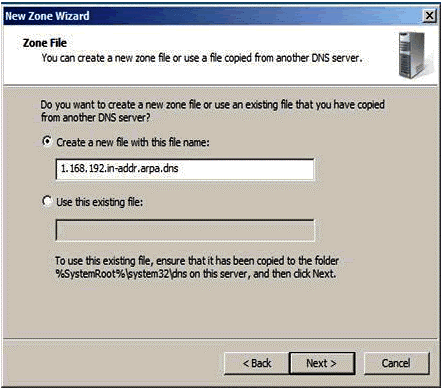
Figure 1.10
User will define a new zone file in case of new DNS server installation.
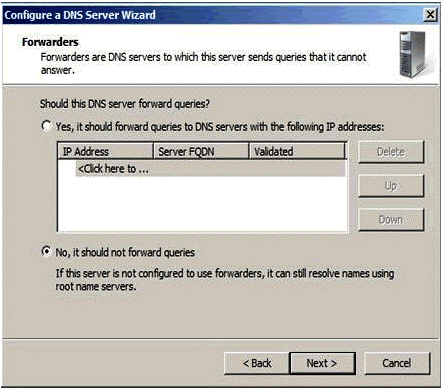
Figure 1.11
In fig 1.11, the selection will be ‘No, it should not forward queries’ in case of a single DNS server. If an organization is maintain more than one DNS servers, and then the selection will be yes.
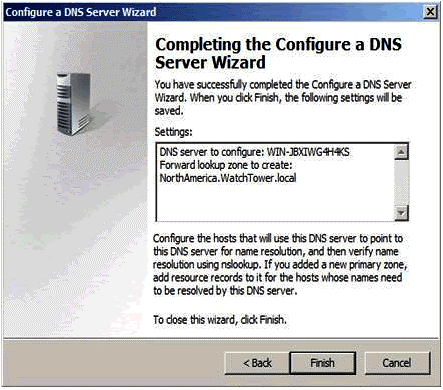
Figure 1.12
After setting up all the options, click finish to end the installation.
The proposed domain will be integrated via Microsoft active directory that will maintain access management functions associated with services on the network. However, users, groups, DNS server, active directory and Windows server operating system will operate as a domain controller, in order to provide effective management of a domain environment. Moreover, more than one domains controllers will lead to significant advantages including additional security in terms of service availability and supporting load balancing features in peak business hours.
References
Benefits and features of DNS for your server, (n.d) Retrieved 10/17/2011, 2011, from http://dns.servers.co.uk/dns-features-and-benefits
Troubleshooting DNS servers: Domain name system(DNS) (n.d) Retrieved 10/17/2011, 2011, from http://technet.microsoft.com/en-us/library/cc787724(WS.10).aspx
Snedaker, S., Shinder, D. L., & Shinder, T. W. (2004). The best damn windows server 2003 book period . Burlington: Syngress Publishing.

Stuck with your Essay?
Get in touch with one of our experts for instant help!

Time is precious
don’t waste it!
writing help!


Plagiarism-free
guarantee

Privacy
guarantee

Secure
checkout

Money back
guarantee

