 All papers examples
All papers examples
Disciplines

- MLA
- APA
- Master's
- Undergraduate
- High School
- PhD
- Harvard
- Biology
- Art
- Drama
- Movies
- Theatre
- Painting
- Music
- Architecture
- Dance
- Design
- History
- American History
- Asian History
- Literature
- Antique Literature
- American Literature
- Asian Literature
- Classic English Literature
- World Literature
- Creative Writing
- English
- Linguistics
- Law
- Criminal Justice
- Legal Issues
- Ethics
- Philosophy
- Religion
- Theology
- Anthropology
- Archaeology
- Economics
- Tourism
- Political Science
- World Affairs
- Psychology
- Sociology
- African-American Studies
- East European Studies
- Latin-American Studies
- Native-American Studies
- West European Studies
- Family and Consumer Science
- Social Issues
- Women and Gender Studies
- Social Work
- Natural Sciences
- Anatomy
- Zoology
- Ecology
- Chemistry
- Pharmacology
- Earth science
- Geography
- Geology
- Astronomy
- Physics
- Agriculture
- Agricultural Studies
- Computer Science
- Internet
- IT Management
- Web Design
- Mathematics
- Business
- Accounting
- Finance
- Investments
- Logistics
- Trade
- Management
- Marketing
- Engineering and Technology
- Engineering
- Technology
- Aeronautics
- Aviation
- Medicine and Health
- Alternative Medicine
- Healthcare
- Nursing
- Nutrition
- Communications and Media
- Advertising
- Communication Strategies
- Journalism
- Public Relations
- Education
- Educational Theories
- Pedagogy
- Teacher's Career
- Statistics
- Chicago/Turabian
- Nature
- Company Analysis
- Sport
- Paintings
- E-commerce
- Holocaust
- Education Theories
- Fashion
- Shakespeare
- Canadian Studies
- Science
- Food Safety
- Relation of Global Warming and Extreme Weather Condition
Paper Types

- Movie Review
- Essay
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- GCSE Coursework
- Grant Proposal
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- Essay
- GCSE Coursework
- Grant Proposal
- Interview
- Lab Report
- Literature Review
- Marketing Plan
- Math Problem
- Movie Analysis
- Movie Review
- Multiple Choice Quiz
- Online Quiz
- Outline
- Personal Statement
- Poem
- Power Point Presentation
- Power Point Presentation With Speaker Notes
- Questionnaire
- Quiz
- Reaction Paper
- Research Paper
- Research Proposal
- Resume
- Speech
- Statistics problem
- SWOT analysis
- Term Paper
- Thesis Paper
- Accounting
- Advertising
- Aeronautics
- African-American Studies
- Agricultural Studies
- Agriculture
- Alternative Medicine
- American History
- American Literature
- Anatomy
- Anthropology
- Antique Literature
- APA
- Archaeology
- Architecture
- Art
- Asian History
- Asian Literature
- Astronomy
- Aviation
- Biology
- Business
- Canadian Studies
- Chemistry
- Chicago/Turabian
- Classic English Literature
- Communication Strategies
- Communications and Media
- Company Analysis
- Computer Science
- Creative Writing
- Criminal Justice
- Dance
- Design
- Drama
- E-commerce
- Earth science
- East European Studies
- Ecology
- Economics
- Education
- Education Theories
- Educational Theories
- Engineering
- Engineering and Technology
- English
- Ethics
- Family and Consumer Science
- Fashion
- Finance
- Food Safety
- Geography
- Geology
- Harvard
- Healthcare
- High School
- History
- Holocaust
- Internet
- Investments
- IT Management
- Journalism
- Latin-American Studies
- Law
- Legal Issues
- Linguistics
- Literature
- Logistics
- Management
- Marketing
- Master's
- Mathematics
- Medicine and Health
- MLA
- Movies
- Music
- Native-American Studies
- Natural Sciences
- Nature
- Nursing
- Nutrition
- Painting
- Paintings
- Pedagogy
- Pharmacology
- PhD
- Philosophy
- Physics
- Political Science
- Psychology
- Public Relations
- Relation of Global Warming and Extreme Weather Condition
- Religion
- Science
- Shakespeare
- Social Issues
- Social Work
- Sociology
- Sport
- Statistics
- Teacher's Career
- Technology
- Theatre
- Theology
- Tourism
- Trade
- Undergraduate
- Web Design
- West European Studies
- Women and Gender Studies
- World Affairs
- World Literature
- Zoology
The Effect of Cyber Culture on Society, Essay Example
Hire a Writer for Custom Essay
Use 10% Off Discount: "custom10" in 1 Click 👇
You are free to use it as an inspiration or a source for your own work.

The internet has created a culture all its own. Sometimes referred to as cyberspace, cyber-culture, or simply the worldwide web, the influence of the internet can largely be seen in how the world works, human beings interact with the world and even how human beings interact with one another. The internet has established its own revolutionary form of economy in e-commerce, and redefined how individuals perceive themselves and what they consider to be human. Most importantly the internet has brought on whole new threat to civilization known as cyber-terrorism. This essay will attempt to assess the core aspects of how cyber culture has influenced society specifically as it relates to human identity, e-commerce, and the new threat of cyber-terrorism.
Cyber Culture and Human Identity
In Chrisitine Rosen’s The New Atlantis Article “Image Culture,” she takes the position that the large development of digitally altered images in society has destroyed the natural human ability to analyze images and assess what’s real or fake. It is her opinion that images were once viewed as jaw dropping are now disvalued in a society because people are exhausted with enhanced and doctored photos all ranked and measured based on their shock value. She shows that the excessive demand for more captivating and eye-catching images in collaboration with the ever more decreasing ability to appreciate images by the viewer points to a progressive addiction for altered images within society. Her concludes is that there is no real prevention to this phenomenon turning into an epidemic as both Western and Eastern media culture are willing to fuel this marketable addiction.
Rosen starts her article by mentioning the horrific way in which images of Hurricane Katrina victims were exploited by the media. She talks about how one can Google a term to find thousands of grotesque or eye catching images. She notes one search in particular where the person who posted a photograph which in past years may have been seen as horrific, with the comment “Remember when this was a shocking image? (Rosen, 2005)” She goes on remark, “The question is not merely rhetorical. It points to something important about images in society: They have, by their sheer number and ease of replication, become less magical and less shocking—a situation unknown until fairly recently in human history (Rosen, 2005).” This brings up another question, such as why are these images shared so frequently? The answer isn’t just the internet, but much of it has to do with the relationship the newspaper and the magazine industry has had with the cyberspace and this new culture of information driven society.
News journals are in the business of selling subscriptions and ads, and in many cases competition is so competitive their options are tamper with the cover shots or lose business. The issue Rosen concerns her article with has to do with the influence of software like Photoshop and other widely used programs. These programs allow people to edit their personal photos and now even their videos, it is not just the publications that are manipulating images but individuals on Social networks as well. These practices set an unrealistic bar for reality to live up to.
It is debatable as to whether publications have the right to tamper with the photos they use. Most newspapers justify taking a picture of one individual’s head and placing it on another’s body, or editing out cigarettes they might be holding to imply a cleaner image by crediting one photographer for the body image and a separate photographer for the head image. This is how they legally get around any lawsuits by crediting the different photographers at the bottom of the publication. This still deceives the average reader. An examples is in the “Photo Tampering throughout History” link, specifically in the 1989 TV Guide Oprah photo where they placed the famous media icon’s head atop Anne Margret’s body. In this particular case they got away with it, a more recent example where Maxim magazine’s January 2006 issue where they took Indian movie star Khushboo’s head and put it atop the body of a barely clothed model resulted in a lawsuit by Khushboo where she claimed she would not be settling out of court. Whether or not the courts rule in her favor will dictate whether these publications have the right to tamper with pictures the way they do.
It is undeniable that this form of editing in photography is in most cases a form of false advertisement, where if the readers don’t read the fine print they are in for a shock later. The article previously mentioned notes a tabloid article in Star Magazine where the cover read “Brad and Angelina Caught Together.” While the cover image placed them side by side, the author notes that the picture of Brad was located out of the country while the picture of Angelina was taken in Virginia. Who is to say this doctored image didn’t have some influence on getting them together in the first place. A classic case of photo altering can be seen in the O.J. Simpson Time Magazine cover, which was originally taken from News Week. The irony of this alteration is that TIME notably has a more credible name backing it and a history of employing more experienced writers as well as writing intuitive and insightful pieces. The credible publication edited O.J.’s skin to make it noticeably darker.
The powerful influence of the use of subliminal imagery and semiotics in advertising can be seen in a recent Carslberg Beer ad. Two billboards created by the Beer company involve the use of air brushed models holding their product, who through digital enhancements appear more stunning than naturally possible. The eyes of each model are enhanced and their pupils are dilated. They are imposed over a background of the company’s logo. It appears to be the bottle.. Puttingthese images next to one another implies that the women and the bottle of beer are one in the same. In the ight hand corner of the ad there is a slogan that reads, “like us?” This is directed towards the onlooker who is expected to equate the brand the sexually appealing model as being the same thing. The use of these images by Carslberg to promote their brand of beer relates back to Rosen when she quotes Roger Scruton who said, “photographic images, with their capacity for realization of fantasies, have a distracting character which requires masterly control if it is not to get out of hand (Rosen, 2005).”
Cyber Terrorism & Society
Since many have diverging opinions on whether or not cyberterrorism is even a threat, and those who recognize it as one are also in disagreement over the extent of its power, this poses a very serious question. Is it possible for cyberterrorists to access online accounts? If so, this would be a very pose a very critical threat to the stability of America. Gordon confronts what is unknown about the nature of cyberterrorism with what is known. The first example she refers to of cyberterrorism in action is a circumstance in Delray Beach, Florida where terrorists made travel plans online. They used public library computers to purchase tickets, and this is very similar to the method used during the September 11 th attacks. The following is a chart used in Sproles and Byars study to display the discrepancies between terrorist and hacker involvement on the internet:
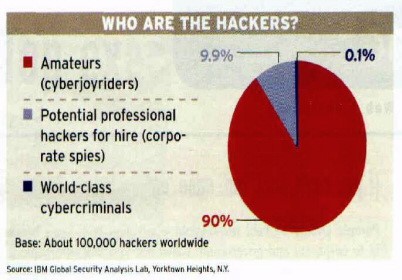
Fig 1 Weimann, G., (2004).
In his predictive analysis of cyber attacks as they relate to the real war on terror, Michael A. Vatis used the following graph in his publication through the Institute for Security Technology Studies at Dartmouth College. It basically shows the frequency at which cyber attacks occurred in Israel and their relation to actual real life terrorist events over a 13 month span from late 1999 to early 2001. The graph shows that in comparing the Middle East’s most violent conflicts with the prevalent battle in cyberspace, there is a significant relation: Fig 2 (Vatis, 2001) As of May 21 st 2001, attrition.org ended its active process of mirroring website activity and defacement, this had made it no longer possible to asses such a connection between real-time physical terror and it influence on cyberspace, or vise versa (Vita, 2001). The following is the official statement of the methodology used by the Symantec Corporation in constructing a definitive understanding of cyberterrorism: Summary & Conclusion (Gordon, 2003) The influence of the internet on society is undeniable.
Cyber Culture & the Economy = E-commerce
No company beterr exemplifies the direction of E-Commerce to date than the success of the company Qualcomm. A significant portion of Qualcomm’s revenue to date can be traced to their royalty ownership of the UMTS interfaces, which is the 3G patent technology the bulk of the mobile wireless industry is grounded in. Their motto is “we bring minds and ideas together.” With Qualcomm’s patent control over the 3G wireless and the use of tracking chips, the company has become a leading contributor to advancements in E- government and e-commerce expansion and the security. The delivery of government services through the use of the Internet is most commonly classified as E-government. The use of many of the data banking chips found on debit cards, are very similar to the smart chips used for government tools and In their essay Statistics On Cyberterrorism Allan Collins estimated a large number of the individuals doing illegal acts on the internet are classified as amateur hackers. Despite this Qualcomm OmniTrac technology has been allowing companies to maintain secure correspondence within company networks for decades. Now, the company has expanded to provide communication services E-government networks, specifically in the U.S. and U.K.
Qualcomm is the definition of a new age company. Their benefits and salaries outmatch many traditional markets, and yet they are entirely based on a cyber driven market. Tuition Qualcomm offers tuition assistance of up to $5,000 for the cost of books and tuition for employees seeking undergraduate degrees such as an Associates degree, a certification or a Bachelor’s. They also offer up to $10,000 in reimbursement for tuition spent by employees in pursuit of graduate or PHD level degrees. (“Qualcomm,” 2010) Vacation Each regular employee working 30 plus hours per week is allotted 3 weeks vacation time per year. Once they have worked for the company for up to 5 years this vacation time increases to 4 weeks per year and then 5 weeks once they have worked for the company for 10 years. (“Qualcomm,” 2010) Health and Wellness Among Qualcomm’s Benefits is its medical plan which include dental, vision and healthcare respectively. It also includes a Dependant Care & Heath Care Reimbursement Account. Sick leave as well as a program known as Qlife (Work/Life Balance Solution) designed specifically to enhance overall quality of life of Qualcomm employees. (“Qualcomm,” 2010) Medical Plan The Qualcomm medical plan is a comprehensive plan that includes dental and vision coverage as well as coverage for dependants up to the age of 16 and coverage for the spouse, or domestic same sex partner. There is a lifetime maximum limit of $2,000,000. (“Qualcomm,” 2010) Sick Leave Each employee is allowed 10 sick days, Regular working employees of up to 30 hours or more per week to put aside up to 5,000 dollars tax free specifically to cover the cost of Dependant healthcare expenses tax free. (“Qualcomm,” 2010) HR Implications for other Companies What Qualcomm’s HR practices within their own camp implicate for other companies potentially using their programs as a benchmark, is that they go above and beyond what is conventionally necessary to take care of their employees. Any company looking to compete with Qualcomm on a fiscal level must first look at their HR practices as a tactic of starting from the ground level up. There is no doubt Qualcomm has adopted the position “a happy employee is a productive employee,” as they have placed vested interest in the entire lifespan of their workforce from age 18 – 50. Stock options, 401(k) plans, Health care plans that cover dependants, Tuition coverage for furthering education, even additional funds to assist in the raising of an adopted child all imply to the employee as well as to the outside competitor that Qualcomm is a company that doesn’t just take responsibility for their employee’s needs but their potential wants and future aspirations as well. This is an implication that will carry over to reflect Qualcomm’s results in the investment market.
In sum, what do all three of these concepts have in common? Rosen demonstrates how the internet is making human beings more desensitized to violent and extreme imagery while losing track of their own human identity; Qualcomm demonstrates that government and the economy is growing evermore data driven and less reliant on actual physical currency or human interaction, and the studies on cyber-terrorism shows that a world ever more reliant on the internet is also more vulnerable to simple attacks, like massive identity theft. There is no real stop to this phenomenon turning into an epidemic as both Western and Eastern media culture are willing to fuel this marketable addiction. If as Rosen has proven, human beings more accustomed to images of violence, and they no longer can distinguish fake imagery from real, it’s not an extreme idea to assume a World Wide holocaust caused by a cyber terrorist attack could be televised and streamed through the internet and received with the same enthusiasm, or reaction by the global public as reality television or the tragedy in Katrina.
Work Cited
Conway, C. and Steward, F. (2009), Managing and Shaping Innovation, Oxford University Press.
Denning, D., (2000) “Cyberterrorism”, Testimony before the Special Oversight Panel of Terrorism Committee on Armed Services, US House of Representatives. (http://www.cs.georgetown.edu/~denning/infosec/cyberter ror.html)
Green, J., (2002). The Myth of Cyberterrorism. The Washington Monthly, November 2002
Rosen, Christine. (2005) “Image Culture” The New Atlantis. p27-46
Vatis A., Michael (2001) Cyber Attacks During The War On Terrorism: A Predictive Analysis. Institute For Security Technology Studies at Dartmouth College, September 22, 2001
Weimann, G., (2004). Cyberterrorism: How Real Is the Threat? United States Institute of Peace, December 2004
Qualcomm United States benefits. (2010). (pp.1-6). Qualcomm.

Stuck with your Essay?
Get in touch with one of our experts for instant help!
Tags:

Time is precious
don’t waste it!
writing help!


Plagiarism-free
guarantee

Privacy
guarantee

Secure
checkout

Money back
guarantee

