 All papers examples
All papers examples
Disciplines

- MLA
- APA
- Master's
- Undergraduate
- High School
- PhD
- Harvard
- Biology
- Art
- Drama
- Movies
- Theatre
- Painting
- Music
- Architecture
- Dance
- Design
- History
- American History
- Asian History
- Literature
- Antique Literature
- American Literature
- Asian Literature
- Classic English Literature
- World Literature
- Creative Writing
- English
- Linguistics
- Law
- Criminal Justice
- Legal Issues
- Ethics
- Philosophy
- Religion
- Theology
- Anthropology
- Archaeology
- Economics
- Tourism
- Political Science
- World Affairs
- Psychology
- Sociology
- African-American Studies
- East European Studies
- Latin-American Studies
- Native-American Studies
- West European Studies
- Family and Consumer Science
- Social Issues
- Women and Gender Studies
- Social Work
- Natural Sciences
- Anatomy
- Zoology
- Ecology
- Chemistry
- Pharmacology
- Earth science
- Geography
- Geology
- Astronomy
- Physics
- Agriculture
- Agricultural Studies
- Computer Science
- Internet
- IT Management
- Web Design
- Mathematics
- Business
- Accounting
- Finance
- Investments
- Logistics
- Trade
- Management
- Marketing
- Engineering and Technology
- Engineering
- Technology
- Aeronautics
- Aviation
- Medicine and Health
- Alternative Medicine
- Healthcare
- Nursing
- Nutrition
- Communications and Media
- Advertising
- Communication Strategies
- Journalism
- Public Relations
- Education
- Educational Theories
- Pedagogy
- Teacher's Career
- Statistics
- Chicago/Turabian
- Nature
- Company Analysis
- Sport
- Paintings
- E-commerce
- Holocaust
- Education Theories
- Fashion
- Shakespeare
- Canadian Studies
- Science
- Food Safety
- Relation of Global Warming and Extreme Weather Condition
Paper Types

- Movie Review
- Essay
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- GCSE Coursework
- Grant Proposal
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- Essay
- GCSE Coursework
- Grant Proposal
- Interview
- Lab Report
- Literature Review
- Marketing Plan
- Math Problem
- Movie Analysis
- Movie Review
- Multiple Choice Quiz
- Online Quiz
- Outline
- Personal Statement
- Poem
- Power Point Presentation
- Power Point Presentation With Speaker Notes
- Questionnaire
- Quiz
- Reaction Paper
- Research Paper
- Research Proposal
- Resume
- Speech
- Statistics problem
- SWOT analysis
- Term Paper
- Thesis Paper
- Accounting
- Advertising
- Aeronautics
- African-American Studies
- Agricultural Studies
- Agriculture
- Alternative Medicine
- American History
- American Literature
- Anatomy
- Anthropology
- Antique Literature
- APA
- Archaeology
- Architecture
- Art
- Asian History
- Asian Literature
- Astronomy
- Aviation
- Biology
- Business
- Canadian Studies
- Chemistry
- Chicago/Turabian
- Classic English Literature
- Communication Strategies
- Communications and Media
- Company Analysis
- Computer Science
- Creative Writing
- Criminal Justice
- Dance
- Design
- Drama
- E-commerce
- Earth science
- East European Studies
- Ecology
- Economics
- Education
- Education Theories
- Educational Theories
- Engineering
- Engineering and Technology
- English
- Ethics
- Family and Consumer Science
- Fashion
- Finance
- Food Safety
- Geography
- Geology
- Harvard
- Healthcare
- High School
- History
- Holocaust
- Internet
- Investments
- IT Management
- Journalism
- Latin-American Studies
- Law
- Legal Issues
- Linguistics
- Literature
- Logistics
- Management
- Marketing
- Master's
- Mathematics
- Medicine and Health
- MLA
- Movies
- Music
- Native-American Studies
- Natural Sciences
- Nature
- Nursing
- Nutrition
- Painting
- Paintings
- Pedagogy
- Pharmacology
- PhD
- Philosophy
- Physics
- Political Science
- Psychology
- Public Relations
- Relation of Global Warming and Extreme Weather Condition
- Religion
- Science
- Shakespeare
- Social Issues
- Social Work
- Sociology
- Sport
- Statistics
- Teacher's Career
- Technology
- Theatre
- Theology
- Tourism
- Trade
- Undergraduate
- Web Design
- West European Studies
- Women and Gender Studies
- World Affairs
- World Literature
- Zoology
Utah Data Center, Research Paper Example
Hire a Writer for Custom Research Paper
Use 10% Off Discount: "custom10" in 1 Click 👇
You are free to use it as an inspiration or a source for your own work.

Introduction
Utah data center is a heavily fortified $2 billion facility in Bluffdale, Utah’s Wasatch Range to the East and the Oquirh mountains to the west. It sits in a 1 million square feet land built solely for the National Security Agency (NAS). This was where religious pioneers first arrived years ago. It is massive and complex telecommunications center, which will be five times the size of the US capital. It is a top –secret project under construction. The inception of the project was done decades ago, but it has now come to be realized (James Bomford).
The main purpose of this center is to intercept, decipher, analyze and store gigantic worldwide communications from the numerous satellites and transmit through the underground and undersea cables of international and domestic networks. The capturing, storing, and analyzing will be done is secrecy even to the close neighbors of the Bluffdale town. This centre will be ready for use in September 2013. The center will be filled with servers, Computers intelligence experts and armed guards. It is constructed in a way that expanding to the town’s boundaries. All forms of communications for example, private e-mails, cell phone calls and data, Google search, parking receipts, travel itineraries, and all forms of digital communications will be flowing through the servers and routers and stored in near-bottomless databases (James Bomford).
The project was conceived during the first term of President Bush Government but in 2003 it was stopped by congress due to America’s outcry on invasion of privacy. Information from an intelligent officer involved in the program, revealed that it is more than a data center, it will also be used for code-breaking (democracynow). The center will also hold financial information, stock transaction, legal documents, business deals foreign military and diplomatic secrets, in an encrypted form. This will be critical for code making and breaking. According to the officer “The NSA made enormous breakthrough several years ago in its ability to crypt-analyze, or break, unfathomably complex encryption systems employed by not only governments around the world but also many average computer users in the US”. This means that everyone is a target (democracynow).
Thesis statement
The NSA have been faced by escalating series of terrorist attacks and surprising assault attacks for example World trade center bombing, booming of US embassies in East Africa, Attack on the USS Cole in Yemen, and also the disaster of 9/11. This has been giving the NSA headache and people began questioning the basis of existence (The Program). The center main purpose will be to eliminate the surprise attacks and be able to know before an attack happens. This will ensure that a mitigation plan is in place, ensuring the safety of its people and capturing of the terrorist before the attack. There has been some indication of improvement in the agency, although the numerous information and gathering opportunities could not capture all cases. For example, the attempted attacks, by the underwear bomber, on a flight to Detroit in 2009 and Car bomber in Times Square in 2010 (James Bomford).
The decision to improve on technology is for the sole purpose of being able to work at an exemplary speed, by checking and unscrambling patterns codes. The center is the largest, most clandestine, and the best ever developed intrusive intelligence agency. The NSA, having concentrated on its citizen’s emails and phone calls, will need supercomputers to analyze in seconds billions of data and their sources. The need for a large storage to store trillions of data collected in electronic form lead to the raise of Utah Data Center (The Program). In the plan for the Utah Data Centre, it is to be divided into, visitors control center equipped with facilities to clear staff before entering the premises; Administration space for technical support and personnel; Data halls with four 25,000 Sq for house facilities and server; Backup generators and fuel tanks to power the center for at least 3 days; Water storage and pumping to supply water to the center; Chiller plant to enable cooling of servers and prevent overheating; Power Substation to meet the power demand for the centre; and Security with videos surveillance and intrusion detection for protection (James Bomford).
Ethical frameworks to use in the evaluation
The ethical framework to be used is for the government to ensure the integrity of its staff. People who will be working on the Utah Data center should be people of integrity, people that would risk their life and not give out information the government holds. This has been very difficult for the Government to achieve as there have been many whistleblowers like William Bunney and Thomas A. Drake. The two have endangered their freedom to warn Americans on NSA’s domestic spying. The problem the government is facing is the fact that it cannot work without labor and because the Agency needs people’s information to maintain security of the state, they will need to invest a lot on employees (The Program).
There are several ethical frameworks that the Government can choose to use. In utilitarian framework it calls for the Government to choose the action plan that seems to be fit for the largest number of people. This framework is difficult to use because is a need the government to be unbiased and treat all people the same without discrimination (Shapiro & Stefkovich, 2010).
The other framework if rights-based, this calls for the government to consider respecting the morals rights of all its citizens. This is unique to individuals’ views and believes. If you are to practice this approach, you cannot access ones information even if the life’s of all the citizens is in danger (Shapiro & Stefkovich, 2010).
The common good and duty framework can be used by the NSA; this will help them make ethical decisions based on what is excellent for its citizens. This approach will recognize the value of maintaining security in the country and therefore, such measure as accessing personal information for the benefit of all is important to uphold (Shapiro & Stefkovich, 2010). The other framework is fairness and justice ethics. This action will treat all human being equally, if unequally then fairly based on some standard that is defensible (Shapiro & Stefkovich, 2010).
Technology definition with system diagram
The diagrams show how the Utah Data centre will be in September 2013, the various servers, Data halls and back-up generators which will be interconnected with satellite to collect the required data and information.
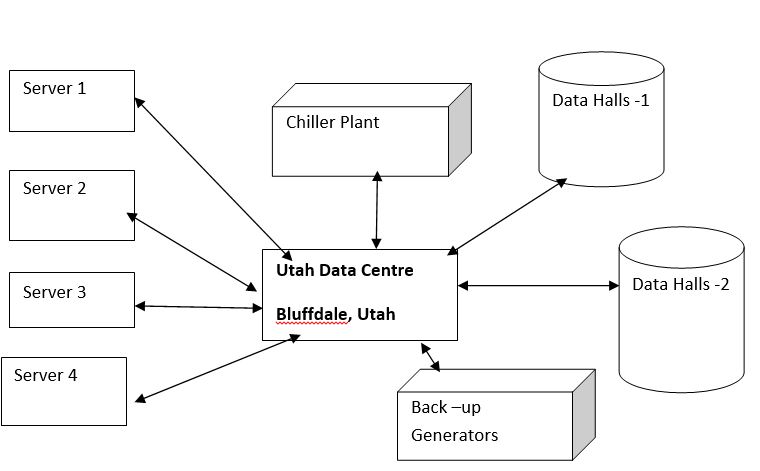
Exploration of ethical dimensions of the problems
Ethical issues arising from the establishing of the Utah Data Centre was the privacy that most US citizens felt it was being infringed. The use of the invisible web like the deep web, which contains data beyond the public’s access. Although the intention of the NSA is open and is beneficial to the entire country’s security, the Citizens have not been convinced otherwise, and they still feel like, being able to get one’s password-protected data and listening to phone calls is unethical and that their right to privacy is adhered.
According to NAS Whistle blower, Mr. William Binney, the foreign Intelligence Surveillance Act amended in 2008 is to be renewed in December; a select committee on intelligence consisting of Ron Wyden of Oregon and Mark Udall of Colorado are trying to bring in an
Amendment on privacy protection to the parliament. They have warned about secret interpretations of laws the allowed the government to collect the citizen private communications. This has generated a lot of debate and currently 13 senators have signed a letter expressing their concern about allowing the government to gain access of private information. These ethical issues have also generated problems with several groups and have challenged the government using the constitution and the Supreme Court is set to hear their arguments on the case on 29th October 2012.
The case where Mr. William Binney house was raided by the FBI is unethical. This was done after he retired from the NAS in 2001. Mr. Binney said he was sorry that the Agency have turned and used the intelligence system in place on its citizens. He said that the Government has profile information of everyone and can easily pull out information of a person when need arise. He was tired of the government harassing him and though that we should be clear if this is to be done or not.
V-application of ethical frameworks with diagrams
In conclusion, my view is that The Utah data centre is good for the Government to ensure that security of their Citizens. The reason behind my support is that it is very intricate to know who is intending on being insecurity to the Country. The only way to ensure cases like the 9/11 do not occur again or are minimized is by having prior information by being able to access information of such people and ensuring that they have no room to affect the security of the nation.
References
Shapiro, J. P. & Stefkovich, J. A. (2010). Ethical leadership and decision making in education: Applying theoretical perspectives to complex dilemmas. New York: Routledge.
This book gives an overview of how educators in education discipline implement various theories in their leadership and decision-making. It provides clear examples on how the theories relate to complex situations and dilemmas, which can be used by diverse organizations in gaining competitive advantage.
Bomford, J. The NSA Is Building the Country’s Biggest Spy Center (Watch What You Say). Retrieved from http://www.wired.com/threatlevel/2012/03/ff_nsadatacenter/all/
This Web page is good because it has sufficient information pertaining the way in which individuals need to relate with other in the society. It aims at reducing the number of terror attacks and gives individuals information on how to conduct their business their business. Additionally, the page has gathered data on how the Government is working to reduce the attacks by terrorists.
National Security Agency Whistleblower William Binney on Growing State Surveillance. Retrieved from http://www.democracynow.org/2012/4/20/exclusive_national_security_agency_whistleblower_william
This Web page is relevant and contributes to the compilation of the paper because it gives information on how NSA performed its duties in relation to William Binney views and opinions. The interview aims at portraying the level of Democracy in the country and insights elaborate how NSA functions in the fight against terrorists.
NSA Whistleblower Details How The NSA Has Spied On US Citizens Since 9/11. Retrieved from http://www.businessinsider.com/nsa-whistleblower- william-binney-explains-nsa-surveillance-2012-8
NSA has spying apparatus and the article critics the operations of the secretive agency. In addition, this program gave the agency a platform of how they are able to track electronic activities. This measure gave the agency a way towards successful achievement of minimizing terrorism in the country. The Program. Retrieved from http://www.nytimes.com/2012/08/23/opinion/the-national-security-agencys-domestic-spying-program.html>
The author brings to light issues pertaining the program and how state surveillance affected Binney’s life. The film-maker gets an opportunity of interviewing him and he gives him insights on the program and other fundamental issues.

Stuck with your Research Paper?
Get in touch with one of our experts for instant help!
Tags:

Time is precious
don’t waste it!
writing help!


Plagiarism-free
guarantee

Privacy
guarantee

Secure
checkout

Money back
guarantee

