 All papers examples
All papers examples
Disciplines

- MLA
- APA
- Master's
- Undergraduate
- High School
- PhD
- Harvard
- Biology
- Art
- Drama
- Movies
- Theatre
- Painting
- Music
- Architecture
- Dance
- Design
- History
- American History
- Asian History
- Literature
- Antique Literature
- American Literature
- Asian Literature
- Classic English Literature
- World Literature
- Creative Writing
- English
- Linguistics
- Law
- Criminal Justice
- Legal Issues
- Ethics
- Philosophy
- Religion
- Theology
- Anthropology
- Archaeology
- Economics
- Tourism
- Political Science
- World Affairs
- Psychology
- Sociology
- African-American Studies
- East European Studies
- Latin-American Studies
- Native-American Studies
- West European Studies
- Family and Consumer Science
- Social Issues
- Women and Gender Studies
- Social Work
- Natural Sciences
- Anatomy
- Zoology
- Ecology
- Chemistry
- Pharmacology
- Earth science
- Geography
- Geology
- Astronomy
- Physics
- Agriculture
- Agricultural Studies
- Computer Science
- Internet
- IT Management
- Web Design
- Mathematics
- Business
- Accounting
- Finance
- Investments
- Logistics
- Trade
- Management
- Marketing
- Engineering and Technology
- Engineering
- Technology
- Aeronautics
- Aviation
- Medicine and Health
- Alternative Medicine
- Healthcare
- Nursing
- Nutrition
- Communications and Media
- Advertising
- Communication Strategies
- Journalism
- Public Relations
- Education
- Educational Theories
- Pedagogy
- Teacher's Career
- Statistics
- Chicago/Turabian
- Nature
- Company Analysis
- Sport
- Paintings
- E-commerce
- Holocaust
- Education Theories
- Fashion
- Shakespeare
- Canadian Studies
- Science
- Food Safety
- Relation of Global Warming and Extreme Weather Condition
Paper Types

- Movie Review
- Essay
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- GCSE Coursework
- Grant Proposal
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- Essay
- GCSE Coursework
- Grant Proposal
- Interview
- Lab Report
- Literature Review
- Marketing Plan
- Math Problem
- Movie Analysis
- Movie Review
- Multiple Choice Quiz
- Online Quiz
- Outline
- Personal Statement
- Poem
- Power Point Presentation
- Power Point Presentation With Speaker Notes
- Questionnaire
- Quiz
- Reaction Paper
- Research Paper
- Research Proposal
- Resume
- Speech
- Statistics problem
- SWOT analysis
- Term Paper
- Thesis Paper
- Accounting
- Advertising
- Aeronautics
- African-American Studies
- Agricultural Studies
- Agriculture
- Alternative Medicine
- American History
- American Literature
- Anatomy
- Anthropology
- Antique Literature
- APA
- Archaeology
- Architecture
- Art
- Asian History
- Asian Literature
- Astronomy
- Aviation
- Biology
- Business
- Canadian Studies
- Chemistry
- Chicago/Turabian
- Classic English Literature
- Communication Strategies
- Communications and Media
- Company Analysis
- Computer Science
- Creative Writing
- Criminal Justice
- Dance
- Design
- Drama
- E-commerce
- Earth science
- East European Studies
- Ecology
- Economics
- Education
- Education Theories
- Educational Theories
- Engineering
- Engineering and Technology
- English
- Ethics
- Family and Consumer Science
- Fashion
- Finance
- Food Safety
- Geography
- Geology
- Harvard
- Healthcare
- High School
- History
- Holocaust
- Internet
- Investments
- IT Management
- Journalism
- Latin-American Studies
- Law
- Legal Issues
- Linguistics
- Literature
- Logistics
- Management
- Marketing
- Master's
- Mathematics
- Medicine and Health
- MLA
- Movies
- Music
- Native-American Studies
- Natural Sciences
- Nature
- Nursing
- Nutrition
- Painting
- Paintings
- Pedagogy
- Pharmacology
- PhD
- Philosophy
- Physics
- Political Science
- Psychology
- Public Relations
- Relation of Global Warming and Extreme Weather Condition
- Religion
- Science
- Shakespeare
- Social Issues
- Social Work
- Sociology
- Sport
- Statistics
- Teacher's Career
- Technology
- Theatre
- Theology
- Tourism
- Trade
- Undergraduate
- Web Design
- West European Studies
- Women and Gender Studies
- World Affairs
- World Literature
- Zoology
Data Security Management, Research Paper Example
Hire a Writer for Custom Research Paper
Use 10% Off Discount: "custom10" in 1 Click 👇
You are free to use it as an inspiration or a source for your own work.

With the ever increasing reliance on wireless networks there are more opportunities for risks to data by external forces trying to take advantage of the security weaknesses of a wireless network. There are many threats to wireless networks and many of these risks can cause damage to the organization’s and customers’ data. The first type of attack would include gaining access by going right into the network. Without the proper security measures an intruder could gain access to the wireless network by sniffing out the wireless signal and logging into the system which grants access to key data and business information. These types of attacks can be active or passive. The active attack is where the intruder is actively seeking out ways to intrude into the network and there is also passive ways for malicious entities to hinder a network. The active risks include direct access to an authorized network access, network hijacking, denial of service and flooding the network with unnecessary requests which limits the ability for the network to be used (Hayden, 2010). The passive attacks utilizes software programs to seek out unsecured or weakly secured networks and accesses them through the program to gain access and cause a disruption. These attacks can be limited and reduced with the appropriate network security measures such as password protection, encryption and other software and hardware security measures.
With data there are two different areas that require security measures and each are slightly different from one another. Here are the key differences and similarities between organizational data and customer data security needs.
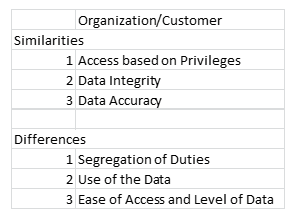
Each area has its own area of similarity and differences. The security measures for each the internal and external users vary slightly based on location and whether or not they are within the firewall security of the organization. This access leads to the types of security measures required to secure the data.
There are many ways to ensure the organizational data is secured from internal and external threats. These threats can come in the form of malicious attacks or unintentional data leakage that could cause harm to the business. The data security is based on protecting the data and other assets from the risks of destructive forces or misappropriated use of the organization’s data. In order to ensure data security there are multiple methods of protection. The first area of protection is the utilization of an encryption method which denies the ability for an unauthorized source from viewing and using the data. This type of encryption normally resides on the hard drive or other storage area that the organization’s data resides. While this type of software encryption’s goal is to prevent malicious behavior there are still threats in the environment that would pose a risk to the data. As well as data encryption there is also data masking which is the process of masking or hiding the data to ensure sensitive or critical data is not present to a group that would be too broad in nature. This masking or securing of data could be limited to a specific group of people that would require specific credentials to access the data.
There are also hardware-based security measures that would thwart the risk of corruption, access or other malicious activity. These hardware based security measures are implemented through the use of security tokens. These tokens must be physically activated and present when logging into a secured system. This allows another point of security that protects the informational assets of the organization.
While there are varying ways to protect the data through software and hardware implementations there are other methods that allow for data security that are more process orientated. This includes establishing a periodic backup plan to secure and store the data so that progress would not be lost if the data is compromised and recovery is necessary. This is a critical component of the overall data security model. This is in essence saving the work the organization is producing so that the information derived from the data is not lost and negative ramifications are felt due to intrusion, corruption or other negative act on the data. Securing the data can be done through encryption, login protection, limiting access, hardware security measures and backing up data to preserve the integrity of the data and information.
References
Hayden, L. (2010). It security metrics. New York: McGraw Hill.

Stuck with your Research Paper?
Get in touch with one of our experts for instant help!

Time is precious
don’t waste it!
writing help!


Plagiarism-free
guarantee

Privacy
guarantee

Secure
checkout

Money back
guarantee

