 All papers examples
All papers examples
Disciplines

- MLA
- APA
- Master's
- Undergraduate
- High School
- PhD
- Harvard
- Biology
- Art
- Drama
- Movies
- Theatre
- Painting
- Music
- Architecture
- Dance
- Design
- History
- American History
- Asian History
- Literature
- Antique Literature
- American Literature
- Asian Literature
- Classic English Literature
- World Literature
- Creative Writing
- English
- Linguistics
- Law
- Criminal Justice
- Legal Issues
- Ethics
- Philosophy
- Religion
- Theology
- Anthropology
- Archaeology
- Economics
- Tourism
- Political Science
- World Affairs
- Psychology
- Sociology
- African-American Studies
- East European Studies
- Latin-American Studies
- Native-American Studies
- West European Studies
- Family and Consumer Science
- Social Issues
- Women and Gender Studies
- Social Work
- Natural Sciences
- Anatomy
- Zoology
- Ecology
- Chemistry
- Pharmacology
- Earth science
- Geography
- Geology
- Astronomy
- Physics
- Agriculture
- Agricultural Studies
- Computer Science
- Internet
- IT Management
- Web Design
- Mathematics
- Business
- Accounting
- Finance
- Investments
- Logistics
- Trade
- Management
- Marketing
- Engineering and Technology
- Engineering
- Technology
- Aeronautics
- Aviation
- Medicine and Health
- Alternative Medicine
- Healthcare
- Nursing
- Nutrition
- Communications and Media
- Advertising
- Communication Strategies
- Journalism
- Public Relations
- Education
- Educational Theories
- Pedagogy
- Teacher's Career
- Statistics
- Chicago/Turabian
- Nature
- Company Analysis
- Sport
- Paintings
- E-commerce
- Holocaust
- Education Theories
- Fashion
- Shakespeare
- Canadian Studies
- Science
- Food Safety
- Relation of Global Warming and Extreme Weather Condition
Paper Types

- Movie Review
- Essay
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- GCSE Coursework
- Grant Proposal
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- Essay
- GCSE Coursework
- Grant Proposal
- Interview
- Lab Report
- Literature Review
- Marketing Plan
- Math Problem
- Movie Analysis
- Movie Review
- Multiple Choice Quiz
- Online Quiz
- Outline
- Personal Statement
- Poem
- Power Point Presentation
- Power Point Presentation With Speaker Notes
- Questionnaire
- Quiz
- Reaction Paper
- Research Paper
- Research Proposal
- Resume
- Speech
- Statistics problem
- SWOT analysis
- Term Paper
- Thesis Paper
- Accounting
- Advertising
- Aeronautics
- African-American Studies
- Agricultural Studies
- Agriculture
- Alternative Medicine
- American History
- American Literature
- Anatomy
- Anthropology
- Antique Literature
- APA
- Archaeology
- Architecture
- Art
- Asian History
- Asian Literature
- Astronomy
- Aviation
- Biology
- Business
- Canadian Studies
- Chemistry
- Chicago/Turabian
- Classic English Literature
- Communication Strategies
- Communications and Media
- Company Analysis
- Computer Science
- Creative Writing
- Criminal Justice
- Dance
- Design
- Drama
- E-commerce
- Earth science
- East European Studies
- Ecology
- Economics
- Education
- Education Theories
- Educational Theories
- Engineering
- Engineering and Technology
- English
- Ethics
- Family and Consumer Science
- Fashion
- Finance
- Food Safety
- Geography
- Geology
- Harvard
- Healthcare
- High School
- History
- Holocaust
- Internet
- Investments
- IT Management
- Journalism
- Latin-American Studies
- Law
- Legal Issues
- Linguistics
- Literature
- Logistics
- Management
- Marketing
- Master's
- Mathematics
- Medicine and Health
- MLA
- Movies
- Music
- Native-American Studies
- Natural Sciences
- Nature
- Nursing
- Nutrition
- Painting
- Paintings
- Pedagogy
- Pharmacology
- PhD
- Philosophy
- Physics
- Political Science
- Psychology
- Public Relations
- Relation of Global Warming and Extreme Weather Condition
- Religion
- Science
- Shakespeare
- Social Issues
- Social Work
- Sociology
- Sport
- Statistics
- Teacher's Career
- Technology
- Theatre
- Theology
- Tourism
- Trade
- Undergraduate
- Web Design
- West European Studies
- Women and Gender Studies
- World Affairs
- World Literature
- Zoology
Implementation Plan, Assessment Example
Hire a Writer for Custom Assessment
Use 10% Off Discount: "custom10" in 1 Click 👇
You are free to use it as an inspiration or a source for your own work.

Introduction
Stush is an organization that produces fashionable and trendy T-shirts and wants to deploy an E-business model, synchronizing two offices and making optimal resource management by only deploying sales and customer service staff at one location, minimize security threats, synchronize communication within remote offices and safeguard information. We will design a secure, reliable and efficient computer network for the company that will address all these issues and fulfill current and future requirements associated with network infrastructure.
Organization
Stush Inc. is a retail manufacturing company that specializes in the design of trendy t-shirts for both men and woman. Business partners and collaborative partners are designers of the t-shirt, t-shirts manufacturer, web designers, owners and sales person.
Detailed Description
The proposed solution of a network design will cover all the department of the company, as it will interconnected both the offices via a Virtual Private network connection. Moreover, applications that will operate on the network will be hosted on any one centralized location.
Work Done at Location
For office in Boca, local area network cabling is carried out, as there are only 4 employees, an 8 port Ethernet switch, a router will be sufficient. A DSL connection will be terminated on client premises equipment incorporating a router. For office in Fort Lauderdale, there are total 6 employees. Same network configuration will be applied except for a 12 port Ethernet switch. For office in Jamaica, again the configuration will be same except for a 12 port Ethernet switch. In order to connect a VPN connection, every remote office will use a dialer to establish VPN connectivity with each branch by providing user credentials.
Problems Found
As the company is relatively small, a cost effective computer network is required to interact digitally with T-shirt designers, T-shirt manufacturer, web designers, owners and sales staff. Moreover, due to absence of a mechanism to capture international buyers and suppliers, Stush inc is not able to gain cost effective rates for T-shirts and have to rely on local trading partners. There are no administrative controls as well as technical controls. An example of an administrative control is a policy that will be discussed in the later part of this project. Likewise, an example of a technical control is a firewall. Moreover, manual work procedure is not standardized and is based on employee experience that may impose a risk of taking inadequate decision. There is no connectivity between the remote offices that may result in a communication gap, resultantly, business goals are impacted. The manual work is not organized and well-structured and most importantly not secure. Communication between offices located at Boca, Fort Lauderdale and Jamaica is not secure, as they are communicating on the normal non encrypted Internet connections.
Proposed Solution to Problems Found
Figure 1.1 demonstrates servers, security appliances, network components, and site to site VPN connectivity along with configuration of features in the routers.MD5 hashing, Point to Point tunneling protocol, Virtual Private Network and CHAP configuration will be applied, as it is the part of the network design. If any employee wants to establish a WAN connection with the Stush network, there is a requirement of a VPN dialer and user credentials for logging into the VPN of Stush network. Moreover, for granting or denying Internet access within the entire network, Microsoft Internet Security and Acceleration server will administer Internet access management. Likewise, a network administrator can bind an IP addressed by the system or the MAC address to enforce compliance with policy violation issues. Moreover, a comprehensive security features are embedded within the network. MD5, PPP, CHAP, ACL and a domain environment is proposed to monitor, evaluate and maintain network services and applications. Furthermore, to optimally utilize the server for significant cost savings, virtualization will be carried out with the deployment of Microsoft hyper V solution that will create a logical instance of applications running on the same server and can be accessible to remote offices of the company.
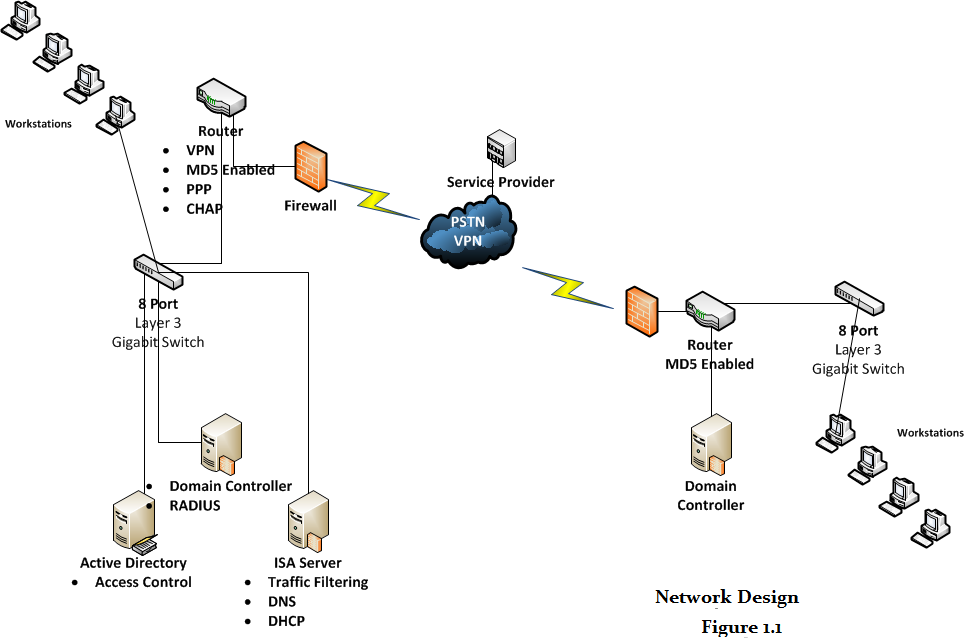
The proposed network design will address current trends in technology by incorporating a VPN connection to merge two offices of the company to a single point of contact. Likewise, sales and customer service staff can only be located at any one office. Moreover, for addressing security, firewall along with configuration of secure protocols is also recommended. Some of the security protocols include CHAP, PPP and MD5 encryption that will make the travelling and stored data secure from threats. Active directory will allow network administrators to centrally monitor and manage user account that will only be accessible by providing credentials. Furthermore, DHCP, RADIUS and traffic filtering are considered to be a value added network services that may become applicable as the company expands in size.
The information security policy is drafted from one of the templates from SANS that claims on their website to be the most trusted and the largest source for information security research in the world that focuses on certification, research and training. In spite, the focus needs to be on aligning business objectives to the policy, as it is considered to be one of the vital controls that govern from top to bottom (Osborne & Summitt,).
This policy demonstrates requirements for protecting or securing information for Stush network to safeguard that the Stush network information that is classified and categorized as confidential cannot be conceded or breached and the services related to production and third party service providers security is safeguarded from the operations of the Stush network
This policy is applicable to all other local networks internally connected, designers of the t-shirt, t-shirts manufacturer, web designers, owners and sales person. The scope of this policy will also cover all the legacy and future equipment that will be configured and tuned as per the reference documentations.
Ownership Responsibilities
The first factor that must be addressed is the ownership criteria. Stush network is responsible for recruiting or assigning a network security manager for a customized network, a point of contact for communication and an alternate point of contact in case of unavailability of the primary point of contact. Employees who are assigned as the owners of the Stush network must organize and update the point of contact on regular basis in order to align with the information security and corporate enterprise management members or groups. Managers of Stush network must be available all the time i.e. round the clock, either via phone or on office hours. In case of absence, alternate manager must be functional to avoid hindrance to Stush network operations. In case of any lack of mismanagement, legal action is applicable against the employee.
Moreover, Stush network managers are also liable for the vital factor that is the security of the information residing on Stush network and the impact of its operations on the production functions and operations that are functional on the network and any other associated network services. However, in a situation where no specific requirements are addressed in the policy, managers must do their best for safe guarding Stush network from security weaknesses and vulnerabilities.
The network support staff or administration must monitor and maintain a firewall between the network that connects the production functions, processes and operations from Stush network or network appliance / equipment / device.
The network support staff or administration must be entitled to have full rights for interrupting network connections of Stush network that may impose impact or security risk on processes, functions and operation on the production network
User passwords must meet the requirements of the access management or password policy of Stush network password policy. Moreover, any inactive account must be deleted within 2 days from the access list of Stush network and any device that involves critical and sensitive information of the Stush network, passwords of group based accounts from the group membership modules must be modified within 24 hours.
The Stush network will not facilitate other services apart from network and data transmission, storage, modification, monitoring and protection. All the other departments will be facilitated by their respective support functions.
In case of non-compliance, security management must consider business justifications and allow waivers accordingly.
Universal Configuration Necessities
The network traffic between the Stush network and other networks will be transmitted via a firewall monitored and maintained by the support staff.
In order to configure or modify any configuration settings on the firewall must be reviewed and approved by the network security personnel.
Enforcement
If any violation of this policy is found, the matter maybe subjected to disciplinary action including termination of employment.
Miscellaneous Items Needed
Star topology will provide centralized administration and configuration of all the nodes on the network. Moreover, star topology initiates low broadcasts on the network, consequently, consuming low bandwidth and at the same time making the network capacity on optimal levels. It is highly recommended for consideration. The minimum hardware specifications of the workstations that will be installed in the current scenario are:
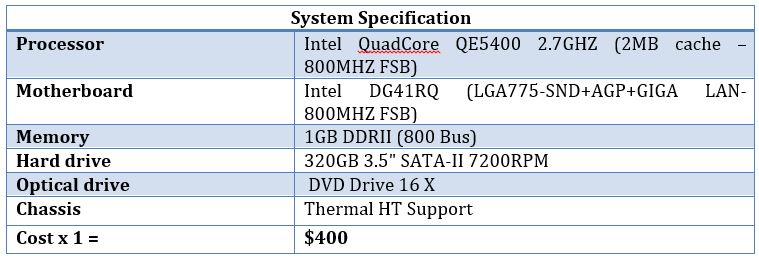
We have total 13 employees altogether deputed in Lauderdale, Jamaica and Boca. The total cost for 13 workstations will be $400 x 13 = $5200
Network devices are the objects for any network. The network functionality relies on the network devices .The dependability of the network devices emphasizes on the requirements of Stush network. Fast Ethernet switches will be implemented instead of hubs within the local area network of the company. Switches are more powerful and intuitive as compared to hubs. The switches will be connected to the router. Routers are implemented on a Wide Area Network (WAN) as well as on the Local Area Network (LAN).
For eliminating the unnecessary broadcast within a LAN domain, the Access Contol List can be configured to minimize the unwanted broadcast from each network node. Access rights and permissions can also be configured for restricting the user at certain levels. The ACL can be configured for restricting and allowing the access of any network resource to the specific user or group of users. Likewise, it provides “a mechanism that implements access control for a system resource by listing the identities of the system entities that are permitted or denied access to the resource” (Access control list.2007). The network server can be a domain controller, firewall or Windows NT server. The requirement of the network server will emphasize on the requirements of the network. A large Network containing network nodes more than 50 may require a domain controller for the administration and configuration of user accounts and permissions.
Conclusion
For addressing all the issues, we have proposed a redundant, secure and reliable network solution for Stush Inc capable of supporting E-business. Likewise; it is followed by a comprehensively defined network policy highlighting each criteria of the computer network. Moreover, costing of hardware including workstations, servers, cabling, network devices and security devices is also discussed.
Project Background
Stush Fashionable T-shirt is a manufacturer of fashionable and trendy T-shirts. For enhancing business functions, there is a requirement of a technological solution supported by information technology and Internet.
Project Goals
- Communication gaps between the two offices
- Communication with the business partners
- Information Security
- Capable to establish international relationships with buyers
- Global presence
- New business opportunities
- Not dependent on local trading partners or suppliers
- Network Design supports Electronic Commerce
- Redundant, reliable and secure computer network
Current State of the Project
As the organization is too small, there are costing issues that need to be considered. For instance, active directory proposed in the network design may not be relevant, as per the current scenario. However, in the long run, it may be a feasible option.
Project Timeline
| Milestones | Proposed Solution Completed |
| Task Deliverables | Network Design Completed, Network Policy Draft Completed |
| Resources Assigned | Firewall, Switches, Servers, Workstations, Routers |
| Deliverables | Network Design |
Budget
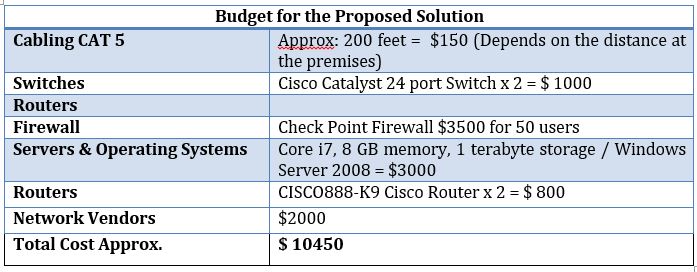
Conclusion
For the implementation part, we have discussed the project background, goals, current progress, timeline and budget for the proposed solution. The identified goals for the project have also been highlighted in this section.
References
Access control list. (2007). Network Dictionary, , 17-17.
Osborne, M., & Summitt, P. M.How to cheat at managing information security Syngress Publishing.

Stuck with your Assessment?
Get in touch with one of our experts for instant help!

Time is precious
don’t waste it!
writing help!


Plagiarism-free
guarantee

Privacy
guarantee

Secure
checkout

Money back
guarantee

