Protecting Patient Private Information, Research Paper Example
Introduction
The recent shift of patient data storage from paper to electronic has been associated with many advantages. According to a 2007 article published in Informatics in Primary Care, electronic health records are the best way to ensure high quality clinical data (Weiner et al. 2007). Weiner and his colleagues state that before this shift, the best source of electronic information to support clinical investigation was claims data; the use of this data in patient research have been criticized because they only capture demographics, diagnoses and procedures recorded for billing purposes. Due to the different needs for record keeping between doctors and insurance companies, these claims may not fully reflect the patient’s condition. The use of electronic health records helps doctors have access to all of the essential details regarding the patient’s clinical status including vital signs, diagnostic test results, social and family history, prescriptions and physical examination findings.
In addition to the ease of access to health records, many physicians prefer to use electronic health records because implementation of this system will save them more money over time and records will be found and accessed more quickly. When records were primarily paper, record storage was a major issue. Physicians are required by law to maintain patient records for a minimum of seven years from the anniversary date of the last treatment; some localities require that these records are held for even a longer period of time than this. Therefore, electronic health records allow offices to maintain a complete set of information on each patient without the need to rent and search storage units for older records. In addition, it is nearly impossible to lose a record using this system; now when a patient enters the office, the nurse or physician’s assistant can pull up the record with a click of a button.
Despite the clear advantage of using electronic health record systems, there are some setbacks. According to a recent study published in Risk Management Healthcare policy, these drawbacks include “high upfront acquisition costs, ongoing maintenance costs, and disruptions to workflows that contribute to temporary losses in productivity that are the result of learning a new system” (Menachemi, 2011). On top of this issue, there are potential perceived privacy concerns. Although these issues have been addressed legislatively in documents like the Health Information Technology for Economic and Clinical Health (HITECH) Act of 2009, the use of electronic health systems have led to many breaches in patient security. According to HealthIT.gov, several measures have been put in place to protect against unintended access to patient health records. The overarching law that requires this privacy protection is known as the Health Insurance Portability and Accountability Act (HIPAA) Security Rule (healthIT.gov, n.d.). Some of the safety measures that are built into electronic health record systems to protect your medical records may include access control tools like passwords and PIN numbers, to limit access to patient information to authorized individuals, like the patient’s doctors or nurses and encryption of stored information. Using encryption, health information cannot accessed by someone who can “decrypt” it, using a special key made available only to authorized individuals.
Occasionally, the Health Insurance Portability and Accountability Act (HIPAA) Security Rule and the Health Information Technology for Economic and Clinical Health (HITECH) are breached. A large group of people are required to view health information in order to ensure proper integration of the electronic health record system into hospitals and doctors’ offices. As a result, we can only standardize the protection of information using these laws; there is now current method used in the implementation of electronic health record systems that will completely prevent unauthorized data access. For example, information can be stolen or unknowingly transmitted between personnel with authorized access. This type of data breach isn’t only unfortunate for the patients or doctors of patients who have their personal information stolen; stolen or de-identified health records can also lead to operational, strategic, cultural, and political fall-out for the organization who is deemed at fault. Many small non-for-profit health consulting firms, such as the Massachusetts eHealth Collaborative, do not have enough funds to protect their patient records to any substantial extent. When a business accidentally breaches patient health data security, they are forced to respond to legislative procedures; this is unfortunate for both the business personnel and the health care community as a whole. Since the need for electronic health record implementation is steadily increasing, third party companies are needed to assist with the process. Doctors do not have enough time to monitor the installation process themselves nor are they capable of creating the system from scratch; in addition, nurses, secretaries, and physician assistants frequently do not have the time required to enter patient data into the electronic record system themselves.
A recent scandal has indicated the need to either adjust the Health Insurance Portability and Accountability Act (HIPAA) Security Rule or increase the penalty for stealing sensitive patient information. A recent publication in UT San Diego online claims that the health care industry’s conversion to electronic health records has led to a flood of patient data being compromised or stolen. In one situation, third party health care electronic system implementer Micky Tripathi learned that someone had broken into his car and stolen his briefcase. Unfortunately, this briefcase contained his laptop computer which contained unencrypted health care records for 13,687 patients. Although this can be viewed as being in noncompliance with HIPAA, it is likely that this information was stored on his laptop computer to primarily convert to the format his clients needed, which would then eventually be coded to protect the patient information. This cost Tripathi’s nonprofit, the Massachusetts eHealth Collaborative in Waltham, Mass., nearly $300,000 in legal, private investigation, credit monitoring and media consultancy fees. While this situation is unfortunate, it is difficult to argue that he is completely at fault for this incident. Whoever broke into Tripathi’s car should assume full responsibility for the damages incurred not only to the patients whose information was stolen, but to the doctors whose practice’s this breach affected in addition to Tripathi’s company. This example demonstrates how unprotected patient information can be used for identity theft; each health record on the stolen laptop contained some combination of a patient’s name, Social Security number, birth date, contact information and insurance information (Perlroth, 2012). As healthcare providers and professionals, we need to do a better job ensuring that information is protected; however if this fails, we also need to know how to appropriately direct the blame.
It is essential that we take steps to ensure the safety of patient data to ensure the protection of people on all levels, whether they are the doctors, third party businesspeople, or the patients themselves. It is difficult to argue that implementing electronic health records is a dangerous process because they clearly provide an advantage to patient health. In fact, under the 2009 stimulus bill, the federal government provides incentive payments to doctors and hospitals to adopt electronic health records. Since there has been support of electronic health records at all levels, political and civilian, why are patient data breaches still allowed to occur? The number of reported breaches was up “32 percent in 2011 from the year before, according to the Ponemon Institute, a Michigan-based information-security research group”. In addition, “those breaches cost the industry an estimated $6.5 billion in 2010. In 49 percent of the cases, lost or stolen phones or personal computers were responsible”. “Fifty-three percent of the organizations surveyed by the group said that inadequate funding was the biggest barrier to preventing data breaches” (Perlroth, 2012). Therefore, the goal of this research is to determine how patient data is currently protected at the various levels of access, the impact that these breaches have on patients, doctors, and other members of the industry, and what steps can and have been taken to protect against patient data security breaches.
Methods
To determine how patient data is currently protected at the various levels of access, research was conducted to determine the currently laws that regulate these procedures federally and locally. In addition, this question was asked of other countries who use electronic health records regularly in order to provide insight into the kinds of legislation that controls this access among different groups of people. This data was retrieved mainly from online legal documents. In addition, several case studies were analyzed with consideration of the effect that breached security patient data has on doctors, patients, and other members of the industry. This data was retrieved mainly from internet newspaper articles describing the cases. The main factors that were analyzed in this situation was the association of the person with the healthcare field, how the security breach occurred, whether HIPAA regulations were being followed or not, whether state and federal regulations were being followed, and what could have been done to prevent the situation. Lastly, to determine what steps can and have been taken to protect against patient data security breaches, review articles that have been published in journals will be collected. In addition, the laws of different nations will be considered; if they differ at all from our own, I will determine whether these laws are applicable to the protection of patient security in our nation.
Results
As of January 2010, the United States Government Accountability Office issued a new document entitled “Patient Safety Act” (GAO, 2010). Although its implementation is still in progress so there is no data available on its effectiveness, we can still use the information contained within this document in order to determine whether it will be an improvement compared to current patient data safety regulatory standards. This document is an addendum to the current electronic health record policies, and calls for an increase in the amount of patient information to be recorded on these systems. The Department of Health and Human Services, Agency for Healthcare Research and Quality (AHRQ) are responsible for implementing the Patient Safety Act by “creating a list of Patient Safety Organizations (PSO) so that these entities are authorized under the Patient Safety Act to collect patient safety data from health care providers to develop improvements in patient safety, and implementing the network of patient safety databases (NPSD) to collect and aggregate patient safety data” (GAO, 2010).
This new law seems to be advantageous to the patient population. Now the data recorded on electronic health record systems will include information on events such as medical error and related events in order to facilitate improvements in patient safety. Before we can decide whether this will be an overall advantage to healthcare, we must determine whether there is potential for a security breach of information. Once medical error information is entered into an electronic health record system without encrypted data, both the patient and his or her doctor is at risk. For example, a patient who suffered from a medical error could be at higher risk in developing some kind of illness; insurance companies who are able to have access to this information may use this to increase their insurance premiums or deny them healthcare altogether. If an outside party has access to the doctor’s name who performed the medical error, his or her practice can suffer from ill publicity, which may force the practice to shut down. While a medical error should absolutely be avoided, accidents do happen and this may be the fault of medical technology or equipment rather than the doctor’s expertise. Therefore, this information can be used to shape current practice if it is done so in a way that both the patient and the doctor are protected.
According to this legal document, when a provider elects to use the services of a listed Patient Safety Organization, the Patient Safety Act provides privilege and confidentiality protections for certain types of data regarding patient safety events that providers collect for the purposes of reporting to a PSO. In general, the Patient Safety Act excludes the use of patient safety data in civil suits, such as those involving malpractice claims, and in disciplinary proceedings against a provider. While certain states have laws providing varying levels of
privilege and confidentiality protections for patient safety data, the Patient Safety Act provides a minimum level of protection. Legal Protections for Patient Safety Data Regulations implementing the Patient Safety Act address the
circumstances under which patient safety data may be disclosed, such as when used in criminal proceedings, authorized by identified providers, and among PSOs or affiliated providers. The government has the authority to conduct reviews to ensure that PSOs, providers, and other entities are complying with the confidentiality protections provided by the law. OCR also has the authority to investigate complaints alleging that patient safety data has been improperly disclosed and to impose a civil money penalty of up to $11,000 per violation” (GAO, 2011).
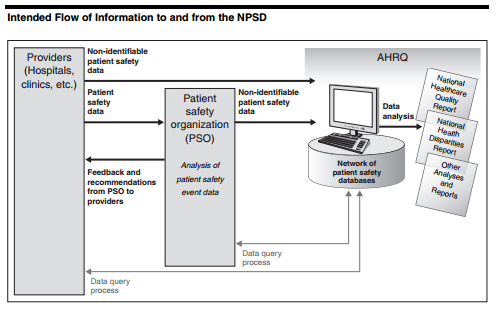
Figure 1 Intended Flow of Information to and from the NPSD
According to the above statement, the revised version of the Patient Safety Act does well to protect all whose information may be accessed. The act protects doctors by explicitly stating that information obtained in this database cannot be used in civil suits and that breach of this contract will impose a penalty of $11,000 violation. Despite this, we must be wary; before the information is placed on the protected system, it could be potentially exposed to theft. In addition, this legal contract only mentions protection in the case of civil suit; if this information is leaked into the public without a formal suit, negative attention brought to the doctor would result in other complications. Figure 1 shows the intended flow of information to and from the database. Before it reaches providers and hospitals, the system will ensure that it contains non-identifiable patient safety information; in addition, the information that providers and hospitals enter into the system to send to the main database will also contain non-identifiable patient safety information. Since the exact information that these records will contain is not listed, it is difficult to classify whether or not this patient information can be truly considered non-identifiable. However, if names are excluded and replaced with a unique identifier, and social security numbers are removed, we can reasonably conclude that effective steps have been taken to reduce identity theft. However, in addition to this information removal, all information that doesn’t directly pertain to patient health status should either be removed or recoded.
Although many states have similar electronic health record patient data safety policies, I decided to examine New York State due to the diversity of populations and localities in the area. According to the New York State Patient’s Bill of Rights, before patients can be treated in a hospital or clinic they must first be provided a list of their rights. The basics of these rights include the ability to “know the names, positions and functions of any hospital staff involved in your care and refuse their treatment, examination or observation, receive complete information about your diagnosis, treatment and prognosis, receive all the information that you need to give informed consent for any proposed procedure or treatment, receive all the information you need to give informed consent for an order not to resuscitate, refuse treatment and be told what effect this may have on your health, refuse to take part in research, privacy while in the hospital and confidentiality of all information and records regarding your care, review your medical record without charge, and authorize those family members and other adults who will be given priority to visit consistent with your ability to receive visitors”. New York State is also required to follow the federal regulations set out by HIPAA; while the hospital is required to allow the patient to see their own health information and they are allowed to elect a representative to also view this information, healthcare facilities are not permitted to show identifiable patient information to anyone else. The “privacy” section of the patient bill of rights refers to the fact that patient information will be decoded before it is used for statistical purposes and encrypted before storage. It is interesting to note that by New York State law, researchers are able to use non-identifiable patient clinical information without any permission from the patient (Public Health Law, n.d.). Other states have similar laws regarding local attention to patient privacy. Since this is the case, all states are required to primarily follow the patient privacy laws set out by the federal government; therefore, the information in this report is generalizable for most of the states.
According to the research I conducted on electronic health records in other parts of the world, people in these countries are potentially at a greater risk of having their health information stolen. Australia recently implemented the Personally Controlled Electronic Health Record (PCEHR) (eHealth) system, which is a nationwide database that will record a patient’s allergies, adverse reactions, medications, immunizations, diagnoses and treatments. Individual patients will also be able to have access to a personal medical diary that only they are able to view and edit. In one sense, this system appears to be safer than the one that the United States currently uses; this is mainly due to the fact that patients are unable to opt out of having their records electronically stored, while patients in Australia will be able to do so. This system will utilize a patient de-identification system similar to the one used in research in the United States. An interesting aspect of this system is that patient data will be available on an opted-in individual in all of the doctor’s offices that he or she goes to across the country; while this will make it easier for one person to go to whatever doctor they choose without worrying about transferring their documents, if this system is hacked, it will cause a major disaster (Department of Health and Aging, 2013). As a result of this analysis, I have concluded that the only major advantage of the Australian system compared to the United States system is the ability to deny the transfer of records to the electronic system; while this may cause some confusion in offices, the patient should full control of the accessibility of his or her documents.
The case discussing Micky Tripathi in the article “Health care industry’s conversion to digital has led to flood of patient data being compromised or stolen” clearly demonstrates the issues that third party businesspeople who work with electronic health records face. Doctors and patients also face similar issues when patient privacy is violated but there are many different repercussions for the different groups of people. The article “Nurse Texts Private Info, But Doctor Sued” discusses how privacy can be breached at the office level if workers are not careful. In this case, a man came into a clinic to have his sexually transmitted disease treated; the nurse at the clinic texted his girlfriend about this situation because the two were related through marriage. The nurse was fired as a result of her actions but the man still sued the nurse because she breached her duty to keep patient privacy (Veriphyr, 2013). The plaintiff’s attorney, T. Andrew Brown said “If the court does find there is an actionable right directly against a medical facility for the disclosure of medical information by a nonphysician, that would have huge implications throughout New York State and throughout the country”. In other words, it is highly important to ensure that doctor’s offices keep patient information private and there is no exception to the rule. HIPAA couldn’t have possibly protected the patient or the data in this situation; however when the woman who reported private health information to her friend, she was violating the nurse’s pledge. It is the foremost responsibility of healthcare professionals to ensure that their patient’s data remains protected. The bad decision that the nurse made also reflects upon her healthcare practice; since the case became publicized, it is likely that many patients stopped visiting this office. This is unfortunate because the doctor and other members of the staff were not at fault. It is possible that the nurse forgot that she shouldn’t be sharing this information or believed it wouldn’t cause any harm. Therefore, in order to prevent these types of situations in the future, the doctor’s office should implement a regular training program that deals with the proper use of the electronic health record system. Although these reminders won’t completely eradicate the leak of sensitive information at the office level, it will certainly help reduce its frequency. This Veriphyr article includes its own recommendation stating that “ProAssurance, a medical liability carrier, recommends all employees sign a confidentiality agreement as a condition of employment and again at the time of their performance evaluations. Supervisors should actively monitor for staff violations and discipline violators in a consistent manner.” While the assessment of violations is useful, it doesn’t help prevent against major patient privacy breaches if this breach is the first time that someone made this kind of mistake.
A 2013 Huffington Post article entitled “Why Your Medical Records Are No Longer Safe” explains that electronic health record systems are regularly accessed by unauthorized viewers. In many cases this can range from patient information being sold to sales companies to someone’s identity being completely stolen. According to the article, “a new study by the Ponemon Institute found that a whopping 94 percent of polled healthcare organizations have suffered ‘data breaches’ that exposed patient records. That’s a 65 percent increase since 2010-2011. Even worse, 45 percent of organizations reported they had more than five significant data breaches in the past two years. Less than half of these hospitals and clinics are confident they can prevent future data breaches or even know they took place” (Gregg, 2013). Since protecting patient privacy data is essential, we have to consider whether or not these numbers make it worthwhile to continue using these systems. While they do make correct diagnoses and prescription tracking substantially easier, do the risks outweigh the benefits? Another saddening fact that this article reports is that the U.S. Department of Health’s Office of Civil Rights, found that in just three years, nearly 21 million patients became the victims of medical record data breaches.
The article lists many reasons why people are able to get their hands on this sensitive information. A majority of the time, a criminal acquired patient privacy information simply by stealing an employee’s laptop. This is problematic because medical records should not be locally stored on an electronic device at all and when they are, they are supposed to be encrypted according to HIPAA to prevent an unauthorized access. In order to prevent this kind of data from being stolen, healthcare practices and third party businesses need to take steps to ensure that either this information isn’t stored on a portable electronic device that could be easily lost or stolen. Therefore, it may be useful for the United States government to implement a policy that states that machinery and equipment containing sensitive patient data should not be allowed to leave healthcare offices. It would also be beneficial if the equipment storing this information in offices were on desktop computers that are larger in size and therefore more difficult to take; surveillance and security should also be available on these premises. Since doctors, hospitals, and third party businessmen do not own this information, they are expected to take every step possible to ensure that this information remains where it should.
A second reason as to why criminals are able to obtain sensitive patient data is that old equipment once used by hospitals, doctors’ offices and other healthcare facilities are often thrown away without fully removing the sensitive medical records they contain. Therefore, healthcare facilities and third party businessmen need to ensure that their equipment is wiped of all sensitive patient information before they are discarded; this usually includes destroying the hard drive. To solve this problem, the United States government should create a law that directs the proper procedure of discarding information that once stored sensitive patient information. Government run centers should be established that instruct institutions how to get rid of their hard drives safely and talk to hospitals that regularly use a lot of this kind of machinery. While it will be up to the individual hospital to establish a subset of rules that they will use to ensure proper disposure of electronic materials, the government can meet with them and help guide them as to what local regulations would be most appropriate. It is essential for doctors and other healthcare professionals to remember that not only PC, laptops, and memory sticks are able to store this information; they must consider also removing the data from testing devices such as ultrasound equipment.
A third reason explaining why criminals are able to access sensitive patient data are due to mistakes made of the part of third parties. Many health care organizations outsource medical record storage and management to third-party vendors. This is a major issue because these vendors may not always be qualified to secure this type of information. One recent problem involves Kaiser Permanente; they allegedly allowed a ‘mom and pop’ document storage company to keep 300,000 personal medical records in a shared warehouse and on their home PCs. While the involvement of third party businesses is nearly impossible to limit due to the amount of work that implementing electronic health records requires, doctors and hospitals need to monitor the companies that they hire and be fully aware of the location and access of their records at all times. Third party companies like Kaiser Permanente need to be held to the same HIPAA standards that healthcare professionals are. If we find that many third party companies are breaching best security practices such as in this example, the United States government and the states involved need to implement a stronger punishment for breaking the law.
A fourth reason that criminals are able to access patient records is due to open WiFi use in many clinical settings. These WiFi networks are useful because they enable their medical staff to work efficiently and accurately as they go from patient to patient. Despite this, the WiFi networks are not always as secure as they should be which makes it possible for intruders within a certain radius of the facility to break into sensitive files. Therefore, healthcare facilities should either ensure the use of a protective password while using this system or switch to a network that allows Ethernet access only. This way only the employees who were intended to be on the network will be able to do so. In order to ensure further protection, each employee should be assigned an individual login name and password that can only be used on one computer in the facility at a time. The computers at the healthcare facility should be programmed to time out and log an employee out after two minutes of inactivity; this way, the likelihood of an unauthorized user coming by and using the computer will significantly decrease.
A fifth reason that criminals are able to access patient records is due to e-mailing scams. Criminals can send healthcare employees e-mails that trick them into giving them access to patient information; usually these scammers will pretend to be from the IT department, an authorized third-party vendor, a supervisor or a fellow employee. It is thus the responsibility of the IT department to reach out to all employees and make them aware of these scams. In addition, the department should provide a list of people who may potentially contact them about patient information and provide them with their phone numbers. Although it is better to only exchange patient information face to face with another employee (if absolutely necessary), individual healthcare policies likely have different rules about this kind of information exchange. Therefore, everyone who has access to this sensitive information should know what these rules are and be trained to identify scam e-mails.
A sixth, commonly seen reason why criminals are able to access private health information is through an employee who has access to this information and is willing to either sell it off to the criminal or give it away to embarrass the patient. Occasionally, this security breach is because the employee wants to get even with their employer or co-workers. In addition, general mistakes, like allowing an unauthorized outsider to view a medical record or leaving a file open on their computer, can also be harmful. Although not much can be done to prevent this kind of breach, the employees should be provided training that inform them about why this is harmful and the negative repercussions of committing this kind of crime. Most people may not realize the legal implications of selling or distributing private health information and they should be made aware of this.
A seventh reason why criminals are able to access private health information is due to records stored in the cloud. Although this is an up and coming data storage trend, storing information on the cloud can be useful in order to ensure that the patient data can be accessed regardless of what computer a healthcare professional is on. However, this system requires the simple use of a username and password to access. There are hackers who know how to guess this information or use internet and WiFi data to retrieve it. According to the Ponemon study, 62 percent of healthcare organizations are moving their patient health records to the cloud but only 30 percent are confident they can adequately protect that information from thieves. If a healthcare organization is unsure that they will be able to protect their patient data in the cloud, they should simply not be using it. Using the cloud has its advantages but it’s not worth threatening patient privacy safety to store this information in cyberspace. To best protect patient data, it should only be stored on the hard drives of computers that will not be removed from the healthcare facility. If data needs to be transferred from one computer to another, it should be transferred onto a flash drive that uses encryption and a password to retrieve the files; once the information is transferred onto the new computer, it should be swiftly deleted.
Conclusion
Patient data is currently protected by HIPAA. Despite this law’s requirements stating that patient data must be encrypted during transfer and de-identified when shared, there are many instances where this security precaution is ignored. Many third party businesspeople fail to follow the same laws that are directed at healthcare professionals which can cause a breach in patient health privacy. Usually, this occurs when the third party stores important patient information that the healthcare facility is unaware of, such as leaving a laptop computer or another mobile information storage device in a place where it shouldn’t be left or losing the device altogether. A second way this occurs is when patient information is being illegally stored on private PC’s that are used for other purposes and are not encrypted or de-identified. Patient data can be leaked differently at different levels of the healthcare system. Doctors and nurses may purposefully or accidentally leak this information by discussing it in public or with friends or may sell it to third parties. Other healthcare workers who have access to this information may be accidentally leaking it when they use their Wi-Fi, upload information to the cloud for storage, respond to an e-mailing scam, and failure to wipe old equipment that contain patient data.
When determining the best ways to ensure patient security, one must determine the levels of impact that the potential leak of this information will have on different people. One of the major issues with patient data leaks is the ability of the criminal to sell this information or use it for identity theft. If patient information isn’t encrypted or de-identified, it likely contains the patient’s name, address, social security number, phone number, and health insurance information. The complete record that is usually contained in an electronic health record can make it very easy for a criminal to achieve this. The doctor of a patient who suffers from the security leak can also face many issues. Firstly, he or she may be sued because the doctor is assigned ultimate responsibility for this information. Even if it is one of his or her employees who are responsible for leaking the information, once the news reaches the public eye, the doctor’s office may lose patients and/or receive negative attention. Lastly, third party businesspeople can suffer considerably as well; if the data storage business is a small non-for-profit like many are, they will be unable to handle the legal fees necessary to protect themselves and need to shut down. There are similar repercussions for larger third party businesses.
Not many steps have been taken to protect against patient data security breaches. As the electronic health record technology and associated storage technology evolves, there is a greater and greater chance that patient data will be accessed without permission. It is therefore essential for all employees to be trained regularly as a reminder to not share patient health data. In addition, they should be reminded to wipe old medical equipment and computers of all data before they throw it away, they should be reminded to encrypt their data on memory sticks when they transfer it from computer to computer, they should not respond to spam e-mails requesting patient information, and they should be weary of their third party business interactions. Overall, it would be useful if the government implemented policies that required HIPAA to be more tightly regulated. Until then, healthcare professionals need to ensure that they follow all of the above advice regarding protecting patient information.
References
Department of Health and Ageing. (2013). Expected benefits of the national PCEHR system.
Government Accountability Office. (2010). Patient Safety Act. Retrieved from http://www.gao.gov/new.items/d10281.pdf
Gregg, M. (2013). Why Your Medical Records Are No Longer Safe. Huffington Post. Retrieved from http://www.huffingtonpost.com/michael-gregg/privacy-medical-records_b_2473458.html
HealthIT.gov. (n.d.). What security safeguards are designed to prevent electronic health records from being “hacked?” Retrieved from http://www.healthit.gov/patients-families/faqs/what-security-safeguards-are-designed-prevent-electronic-health-records-being
Perlroth, N. (2012). Leaky records: Health care industry’s conversion to digital has led to flood of patient data being compromised or stolen. UT San Diego. Retrieved from http://www.utsandiego.com/news/2012/Jan/25/tp-leaky-records/
Public Health Law (PHL)2803 (1)(g). (n.d.). Patient’s Rights, 10NYCRR, 405.7,405.7(a)(1),405.7(c)
Menachemi N, Collum TH. (2011). Benefits and drawbacks of electronic health record systems. Risk Manag Healthc Policy, 4: 47–55.
Veriphyr. (2013). Nurse Texts Private Info, But Doctor Sued. Retrieved from http://blog.veriphyr.com/2013/05/nurse-texts-private-info-but-doctor-is.html
Weiner MG, Lyman JA, Murphy S, Weiner M. (2007). Electronic health records: high-quality electronic data for higher-quality clinical research. Inform Prim Care, 15(2):121-7.

Time is precious
don’t waste it!

Plagiarism-free
guarantee

Privacy
guarantee

Secure
checkout

Money back
guarantee






