 All papers examples
All papers examples
Disciplines

- MLA
- APA
- Master's
- Undergraduate
- High School
- PhD
- Harvard
- Biology
- Art
- Drama
- Movies
- Theatre
- Painting
- Music
- Architecture
- Dance
- Design
- History
- American History
- Asian History
- Literature
- Antique Literature
- American Literature
- Asian Literature
- Classic English Literature
- World Literature
- Creative Writing
- English
- Linguistics
- Law
- Criminal Justice
- Legal Issues
- Ethics
- Philosophy
- Religion
- Theology
- Anthropology
- Archaeology
- Economics
- Tourism
- Political Science
- World Affairs
- Psychology
- Sociology
- African-American Studies
- East European Studies
- Latin-American Studies
- Native-American Studies
- West European Studies
- Family and Consumer Science
- Social Issues
- Women and Gender Studies
- Social Work
- Natural Sciences
- Anatomy
- Zoology
- Ecology
- Chemistry
- Pharmacology
- Earth science
- Geography
- Geology
- Astronomy
- Physics
- Agriculture
- Agricultural Studies
- Computer Science
- Internet
- IT Management
- Web Design
- Mathematics
- Business
- Accounting
- Finance
- Investments
- Logistics
- Trade
- Management
- Marketing
- Engineering and Technology
- Engineering
- Technology
- Aeronautics
- Aviation
- Medicine and Health
- Alternative Medicine
- Healthcare
- Nursing
- Nutrition
- Communications and Media
- Advertising
- Communication Strategies
- Journalism
- Public Relations
- Education
- Educational Theories
- Pedagogy
- Teacher's Career
- Statistics
- Chicago/Turabian
- Nature
- Company Analysis
- Sport
- Paintings
- E-commerce
- Holocaust
- Education Theories
- Fashion
- Shakespeare
- Canadian Studies
- Science
- Food Safety
- Relation of Global Warming and Extreme Weather Condition
Paper Types

- Movie Review
- Essay
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- GCSE Coursework
- Grant Proposal
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- Essay
- GCSE Coursework
- Grant Proposal
- Interview
- Lab Report
- Literature Review
- Marketing Plan
- Math Problem
- Movie Analysis
- Movie Review
- Multiple Choice Quiz
- Online Quiz
- Outline
- Personal Statement
- Poem
- Power Point Presentation
- Power Point Presentation With Speaker Notes
- Questionnaire
- Quiz
- Reaction Paper
- Research Paper
- Research Proposal
- Resume
- Speech
- Statistics problem
- SWOT analysis
- Term Paper
- Thesis Paper
- Accounting
- Advertising
- Aeronautics
- African-American Studies
- Agricultural Studies
- Agriculture
- Alternative Medicine
- American History
- American Literature
- Anatomy
- Anthropology
- Antique Literature
- APA
- Archaeology
- Architecture
- Art
- Asian History
- Asian Literature
- Astronomy
- Aviation
- Biology
- Business
- Canadian Studies
- Chemistry
- Chicago/Turabian
- Classic English Literature
- Communication Strategies
- Communications and Media
- Company Analysis
- Computer Science
- Creative Writing
- Criminal Justice
- Dance
- Design
- Drama
- E-commerce
- Earth science
- East European Studies
- Ecology
- Economics
- Education
- Education Theories
- Educational Theories
- Engineering
- Engineering and Technology
- English
- Ethics
- Family and Consumer Science
- Fashion
- Finance
- Food Safety
- Geography
- Geology
- Harvard
- Healthcare
- High School
- History
- Holocaust
- Internet
- Investments
- IT Management
- Journalism
- Latin-American Studies
- Law
- Legal Issues
- Linguistics
- Literature
- Logistics
- Management
- Marketing
- Master's
- Mathematics
- Medicine and Health
- MLA
- Movies
- Music
- Native-American Studies
- Natural Sciences
- Nature
- Nursing
- Nutrition
- Painting
- Paintings
- Pedagogy
- Pharmacology
- PhD
- Philosophy
- Physics
- Political Science
- Psychology
- Public Relations
- Relation of Global Warming and Extreme Weather Condition
- Religion
- Science
- Shakespeare
- Social Issues
- Social Work
- Sociology
- Sport
- Statistics
- Teacher's Career
- Technology
- Theatre
- Theology
- Tourism
- Trade
- Undergraduate
- Web Design
- West European Studies
- Women and Gender Studies
- World Affairs
- World Literature
- Zoology
System Design and Specification, Capstone Project Example
Hire a Writer for Custom Capstone Project
Use 10% Off Discount: "custom10" in 1 Click 👇
You are free to use it as an inspiration or a source for your own work.

Introduction
Our industries, factories, organizations, SME’s are revolutionized significantly with the aid of information technology. The manual procedures which were conducted by physical interaction are now integrated in to computerized software programs and networks. The automation processes are now only a few mouse clicks away. These systems enabled the organizations to get accurate and efficient information almost instantly. Information technology is penetrated in almost every sector, every industry, corporate organizations, small businesses, online businesses, cell phones, home computers, fax machines, emails, Internet, and our day to day activities. Hence, Information technology is a part of our lives, culture and society.
On the other hand, the robust revolution of information technology advancements has enabled itself almost essential for every organization. The adaptation of information systems enables the business to automate the manual processes, productivity, reliability and efficiency. The objective is to automate organizational processes and decisions with the help of information systems. The objectives are to optimize the throughput and productivity at lowest cost. Evaluating information systems is listed in one of the most crucial aspects of this industry. Computer scientist showed the propensity to concentrate their efforts in terms of developing methods for evaluating the performance of information systems. The values which they consider as parameters to evaluate information systems are; the total throughput of the system, CPU utilization and processing a given job at lowest cost (Oxford Journals).
Today, information systems equipped with latest technology are mandatory to be incorporated in every corporate organization. However, gaining benefits from the new systems need an extensive consideration on various factors related to the success or failure of these systems. Similarly, a network design was constructed for Stush Inc. The specific product is a proposed network design addressing issues highlighted in requirement analysis. As the requirement analysis highlighted an absence of mechanism for capturing internal market of garment buyers and suppliers. Similarly, no administrative and technical controls are available. Moreover, no standardized practices are followed for business operations and no communication infrastructure available for connecting branches located at different locations. For addressing all these issues, a proposed network design was constructed. The design incorporates physical assets such as workstations, servers and network devices. For capturing international buyers, an infrastructure capable of hosting a secure website is implemented. For deploying administrative controls, network policy is drafted for designating ownerships and responsibilities for enforcement of policy. Moreover, technical controls are addressed by configuring VPN, CHAP, MD5 and PPTP along with Microsoft Internet and Acceleration server that will also work as a proxy server for Stush Inc. furthermore, for addressing scalability for the future, virtualization solutions are also implemented such as the Microsoft Hyper V (Stidley, 2008).
As far as training is concerned, information technology is evolving at a rapid pace. Organizations are keen to align with current trends in the industry. As we are currently on the initial stage of our training phase, users must be trained for using workstations and accessing data sources on the network. Moreover, they must be well versed for acceptable use policies that may include do’s and don’ts for the Stush network services and resources. Training is not a single phase activity; it is a periodic process that initiates on different phases of the network. For instance, network development training incorporates users to contribute in the development process, network migration training incorporates business continuity planning, and network maintenance incorporates support training for the support staff. As per the current scenario, on- going training is recommended, as the system behavior will change during network implementation. Users must be trained for accessing data sources within the internal as well as external networks i.e. remote offices. Moreover, users must be trained for establishing VPN connectivity if lost for some reason. Furthermore, updating anti-virus, defragmenting and scanning hard drive for efficiency and known viruses is also incorporated in an ongoing training of the staff.
Description of Products
The product of the design demonstrates a connectivity of two offices via a Virtual private network connection. The VPN connection is subscribed from an Internet Service Provider. Each remote office comprises of a firewall that accepts or denies data packets as per defined rules. After the firewall, a router is installed. The backbone router that is located at the hub branch is more secure, as it received request for connections from all other remote offices i.e. spokes. Secure encryption protocols, algorithms and hashing techniques are configured. Furthermore, the router is than connected to a switch connecting to internal network or local area network within the hub branch. However, the spoke branch incorporates a configuration of only MD5 at the router and the rest is similar to hub branch. The hub branch also incorporates Domain environment i.e. Microsoft Active Directory server, Microsoft Internet and Acceleration Server and RADIUS server. The Microsoft Active Directory server will ensure integrity and security of directory services and maintain them centrally (Brovick, Hauger, & Wade, 2000). The Microsoft Internet and Acceleration Server ensures added layer of security by dropping suspicious packets bypassing the firewall and granting, restricting Internet access to specific employees, as per business requirements. Moreover, ISA server is also configured for filtering traffic (Dooley, 2002), maintain a domain name service and dynamic host configuration protocol. Similar to a hub branch, all the spoke branches acquire a domain controller that will be synchronized with the primary domain controller located at the hub branch. Infrastructures for both hub branch and spoke branch are illustrated below in Fig 1.1 and 1.2 respectively.
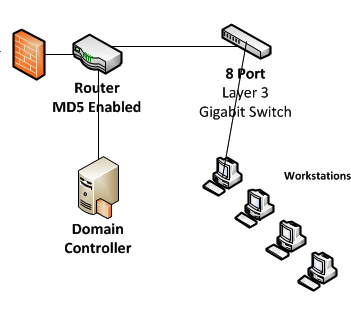
Figure 1.1
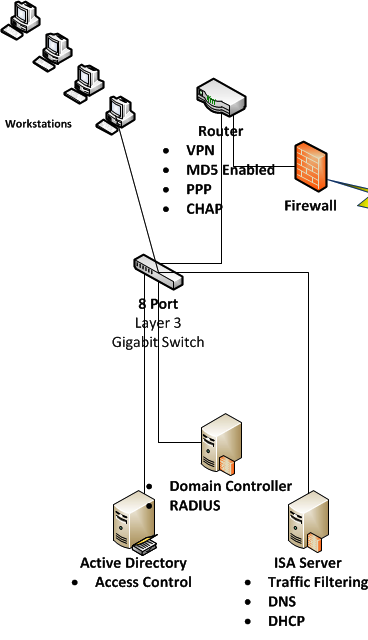
Figure 1.2
VPN connectivity is established by utilizing Public Switched Telephone Networks (PSTN). The connectivity is demonstrated in Fig 1.3 below
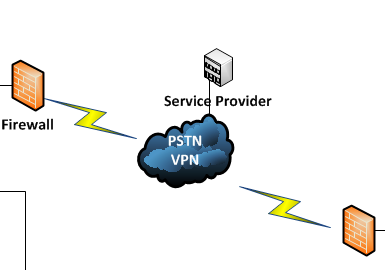
Figure 1.3
As per fig 1.2, one of the branches is hub branch and other one is the spoke branch (Remote office). As hub branch is the backbone for connecting all the branches, spoke branches must require an Internet connection and a VPN dialer (Roland & Newcomb,) with credentials. In order to establishing connectivity with the hub branch, spoke branch will dial in from a ‘VPN dialer’ with correct credentials for authentication and connecting successfully with the Stush Network. Cisco network devices and security appliances are preferred. However, if cost is the issue than the alternative will be to configure software based firewalls. Likewise, Microsoft ISA server is a firewall that also RADIUS, DHCP and VPN is a suitable options for an SME such as Stush. Moreover, for hosting web server, total cost of ownership will be increased significantly, as the web server requires periodic maintenance, redundant Internet links and alternate power supplies. Hosting to a third party will be a feasible option, as administrative access will be provided to modify or add dynamic web pages with updated contents.
References
Brovick, E., Hauger, D., & Wade, W. (2000). Windows 2000 active directory. Indianapolis, Ind.: New Riders Pub.
Dooley, K. (2002). Building large-scale LANs . Beijing: O’Reilly.
Roland, J., & Newcomb, M. J.CCSP cisco secure VPN exam certification guide (CCSP self-study) Cisco Press.
Stidley, J. (2008). MCTS: Windows server 2008 applications infrastructure configuration study guide (exam 70-643). Hoboken: John Wiley & Sons, Inc.

Stuck with your Capstone Project?
Get in touch with one of our experts for instant help!

Time is precious
don’t waste it!
writing help!


Plagiarism-free
guarantee

Privacy
guarantee

Secure
checkout

Money back
guarantee

