 All papers examples
All papers examples
Disciplines

- MLA
- APA
- Master's
- Undergraduate
- High School
- PhD
- Harvard
- Biology
- Art
- Drama
- Movies
- Theatre
- Painting
- Music
- Architecture
- Dance
- Design
- History
- American History
- Asian History
- Literature
- Antique Literature
- American Literature
- Asian Literature
- Classic English Literature
- World Literature
- Creative Writing
- English
- Linguistics
- Law
- Criminal Justice
- Legal Issues
- Ethics
- Philosophy
- Religion
- Theology
- Anthropology
- Archaeology
- Economics
- Tourism
- Political Science
- World Affairs
- Psychology
- Sociology
- African-American Studies
- East European Studies
- Latin-American Studies
- Native-American Studies
- West European Studies
- Family and Consumer Science
- Social Issues
- Women and Gender Studies
- Social Work
- Natural Sciences
- Anatomy
- Zoology
- Ecology
- Chemistry
- Pharmacology
- Earth science
- Geography
- Geology
- Astronomy
- Physics
- Agriculture
- Agricultural Studies
- Computer Science
- Internet
- IT Management
- Web Design
- Mathematics
- Business
- Accounting
- Finance
- Investments
- Logistics
- Trade
- Management
- Marketing
- Engineering and Technology
- Engineering
- Technology
- Aeronautics
- Aviation
- Medicine and Health
- Alternative Medicine
- Healthcare
- Nursing
- Nutrition
- Communications and Media
- Advertising
- Communication Strategies
- Journalism
- Public Relations
- Education
- Educational Theories
- Pedagogy
- Teacher's Career
- Statistics
- Chicago/Turabian
- Nature
- Company Analysis
- Sport
- Paintings
- E-commerce
- Holocaust
- Education Theories
- Fashion
- Shakespeare
- Canadian Studies
- Science
- Food Safety
- Relation of Global Warming and Extreme Weather Condition
Paper Types

- Movie Review
- Essay
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- GCSE Coursework
- Grant Proposal
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- Essay
- GCSE Coursework
- Grant Proposal
- Interview
- Lab Report
- Literature Review
- Marketing Plan
- Math Problem
- Movie Analysis
- Movie Review
- Multiple Choice Quiz
- Online Quiz
- Outline
- Personal Statement
- Poem
- Power Point Presentation
- Power Point Presentation With Speaker Notes
- Questionnaire
- Quiz
- Reaction Paper
- Research Paper
- Research Proposal
- Resume
- Speech
- Statistics problem
- SWOT analysis
- Term Paper
- Thesis Paper
- Accounting
- Advertising
- Aeronautics
- African-American Studies
- Agricultural Studies
- Agriculture
- Alternative Medicine
- American History
- American Literature
- Anatomy
- Anthropology
- Antique Literature
- APA
- Archaeology
- Architecture
- Art
- Asian History
- Asian Literature
- Astronomy
- Aviation
- Biology
- Business
- Canadian Studies
- Chemistry
- Chicago/Turabian
- Classic English Literature
- Communication Strategies
- Communications and Media
- Company Analysis
- Computer Science
- Creative Writing
- Criminal Justice
- Dance
- Design
- Drama
- E-commerce
- Earth science
- East European Studies
- Ecology
- Economics
- Education
- Education Theories
- Educational Theories
- Engineering
- Engineering and Technology
- English
- Ethics
- Family and Consumer Science
- Fashion
- Finance
- Food Safety
- Geography
- Geology
- Harvard
- Healthcare
- High School
- History
- Holocaust
- Internet
- Investments
- IT Management
- Journalism
- Latin-American Studies
- Law
- Legal Issues
- Linguistics
- Literature
- Logistics
- Management
- Marketing
- Master's
- Mathematics
- Medicine and Health
- MLA
- Movies
- Music
- Native-American Studies
- Natural Sciences
- Nature
- Nursing
- Nutrition
- Painting
- Paintings
- Pedagogy
- Pharmacology
- PhD
- Philosophy
- Physics
- Political Science
- Psychology
- Public Relations
- Relation of Global Warming and Extreme Weather Condition
- Religion
- Science
- Shakespeare
- Social Issues
- Social Work
- Sociology
- Sport
- Statistics
- Teacher's Career
- Technology
- Theatre
- Theology
- Tourism
- Trade
- Undergraduate
- Web Design
- West European Studies
- Women and Gender Studies
- World Affairs
- World Literature
- Zoology
The Basics of Kerberos, Research Paper Example
Hire a Writer for Custom Research Paper
Use 10% Off Discount: "custom10" in 1 Click 👇
You are free to use it as an inspiration or a source for your own work.

Understanding the Basics of Kerberos and its Compatibility with the WiMax Network Setup (Question and Response Paper)
What is Kerberos authentication protocol?
The institutionalization of computer technology has created several options of connection between users. It could be analyzed that somehow, the transformation of modern technology if communication has provided an open source of support and benefit for its million users around the globe. Nevertheless, it should not be forgotten that the same aspect of connection has subjected the system of modern communication into several dangers and disadvantages especially related to creating centralized systems that are made open to several users.
The establishment of communication networks between related users has become a common source of connection. Nevertheless, such connections ought to be secured. This is the reason why it is very important that such connections are secured only for the utilization of the authorized individuals. This means that only those who are authorized are supposed to have a direct access on the information and connection that a particular network provides.
The Kerberos authentication protocol, created by Steve Miller and Clifford Neuman, specifically gave an answer to this particular need (Neuman, et al, 1994). Dependent on the built-up of symmetric cryptography, the system protects a particular network from third party intruders into the system. Through the use of encrypted codes that are specifically utilized as access points for those who are allowed to access information from the network [or at some point exchange files using the system of the network] the entire operation of the network is completely protected.
The fourth version of Kerberos which is considered to be the latest had its specific sources of operational competence especially when it comes to its application on Project Athena. Nevertheless, vendors such as Oracle, Google, Microsoft and even Apple have funded for further research so as to improve the system of operation that Kerberos provides especially in relation to establishing protection for existing networks between users across the internet (Walla, 2000, Worldwide Web). At present, the system is being protected by the US consortium specifically pointing out that it is an auxiliary military program that should not be reproduced nor exported. However, the system that was created by the Swedish programmers was considered to be a copy or at least a sourced out system from that of Kerberos which is now used widely by several networks [although the one submitted for military use has its exclusive functions].
Explain how it works (give examples)?
Currently, the release of the fifth version of Kerberos protocol has been considered to be the most updated aspect of the system. Basically, the operation exists in line with the utilization of exchange of tickets between users and the servers.
As seen from the diagram (Zhu , 2006, Worldwide Web) presented herein, the Kerberos operation of protection and security in networks is based upon the existence of a Key Distribution Centre or KDC. Before a user is able to access a particular network, the server asks for authentication code which serves as an access ticket.
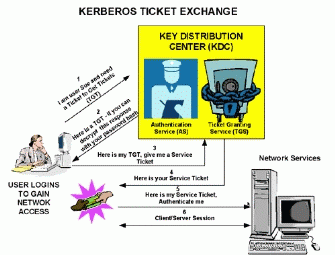
The TGT [Ticket Granting Ticket] system then processes an access code for both the server and the client for them to be able to access both workstations within a specific time allowance. Through this system, the access code provided is to be utilized only during a specific span of time. The verification of identity between the server and the client is impacted by the Kerberos system through the use of codes that serve as access tickets to the system. There are instances when network operators would require the non-re-entry of ticket access from one client. The idea behind this is to protect the network from possible intruders to the system through constantly revised codes hence making it easier to identify the clients who are given the authority to access the network’s operation and exchange information within its system.
In this aspect of accessing a particular network, there are instances when a user name and password entry would not suffice for an access ticket. The server operators are then to ask particular information to assure that the incoming user is an authenticated client of the network (Kohl, et al, 1994). Only after entering the correct response to particular questions that only the user would know would access be granted to the client. Nevertheless, such access should be noted to have a limited point of utilization hence insisting that the client be able to re-enter information and reconfirm authentication after several hours of logging into the system.
What is the current status of the security for WiMAX (based on IEEE 802.16 Standard)?
As a model of the 4G communication system, WiMAX or the Worldwide Interoperability for Microwave Access is considered to be the latest form of wireless connectivity known to the human society at present. Surpassing a 30-meter wireless range for internet access, this system of connection is widely used worldwide.
Relatively though, because of its wide-ranged manner of reaching its users, there are instances when unauthorized clients are able to access signal and some are even able to hack through the system and further create possibilities of accessing and utilizing the services provided through the said wireless connection. As a result, those who have actually paid for the service begin to suffer the consequences of overloaded users of the system. This is the reason why the need to establish a system of security in relation to the establishment of WiMAX central signal stations have been considered.
In relation to the currently established security system of WiMAX, it has been noted to be based on two quality encryption operations. One is that of the DES3 and another is that of the AES. Noted to be within the leading edge of protection programs for the operation, the security processor that functions as the protector of the system under the DES3 and the AES operation are specifically related under the data over cable service interface specification or the DOCSIS security protocol.
This means that the encryption of information and message passed on through the wireless communication system is handled within the data cables connecting the source of signal towards its users. This then allows the users to access information with much protection from possible third-party intruders from non-authorized public users.
Certification of users’ access code is another system that WiMAX uses at present for establishing system protection. However, given the encryption system used for WiMAX, it could be realized how relatively weak it has been tested when it comes to the needed management of frames as information is released within each dedicated data cable. It has been reported that the 802.11 version of the encryption system is weak when it comes to allowing third party attackers in collecting information about subscribers around the area and likely hacking through the system using the said collected data from authorized users (Weinschenk, 2010). Through manipulating the information they have collected, they are often able to intrude within the system and get legitimate service utilizing legitimate access points and access codes.
Can Kerberos authentication protocol be used in WiMAX network? explain why?
Considering that WiMax operates in larger forms of network, specific adjustments on the system of authentication protocol that Kerberos provides could make it a viable source of security for the system (Fazel. et al, 2008). Relatively, Kerberos could address the weakness of WiMAX’s current system of protection through imposing the utilization of the ticket granting ticket operation. This way, the information code that is given to users becomes constantly dynamic which means it shall be changed every time a user tends to access the network service that WiMAX provides (Ergen. 2009) .
This could at some point be tedious especially when it comes to actual application. Nevertheless, its establishment within the system of operation that WiMAX embraces would likely protect it from intruders who are relying on repetitive information used for access by legitimate users of the service. With such protection, third party hackers or intruders would not be able to immediately “guess” the access codes that the users use as they are expected to change every time that the authorized clients log into the system. The uniformity of log in details along with the code used to access the service that WiMax gadgets provide often make the system vulnerable to those who are able to gather such information from original users. The dynamic system of changing codes would simply allow the users to secure the services they receive more and become more capable of protecting their position in receiving the services that WiMAX operation should be able to provide them with.
References
Fazel, K. and Kaiser, S. (2008). Multi-Carrier and Spread Spectrum Systems: From OFDM and MC-CDMA to LTE and WiMAX, 2nd Edition, John Wiley & Sons.
Ergen, M. (2009). Mobile Broadband – Including WiMAX and LTE. Springer, NY.
Weinschenk, . (April 16, 2010). “Speeding Up WiMax“. IT Business Edge.
Neuman, C. and Ts’o, T. (September 1994). “Kerberos: An Authentication Service for Computer Networks”. IEEE Communications 32 (9): 33–8.
Kohl , J.T., Neuman, C, and Ts’o, T (1994). “The Evolution of the Kerberos Authentication System”. In Johansen, D.; Brazier, F. M. T. (Postscript). Distributed open systems. Washington: IEEE Computer Society Press. pp. 78–94.
Walla, M. (2000). Kerberos Explained. Windows 2000 Advantage magazine. http://technet.microsoft.com/library/Bb742516#EEAA. (Retrieved on July 22, 2012).
Zhu, L and Tung, B. (2006). Public Key Cryptography for Initial Authentication in Kerberos (PKINIT). http://tools.ietf.org/html/rfc4556. (Retrieved on July 22, 2012).

Stuck with your Research Paper?
Get in touch with one of our experts for instant help!
Tags:

Time is precious
don’t waste it!
writing help!


Plagiarism-free
guarantee

Privacy
guarantee

Secure
checkout

Money back
guarantee

