 All papers examples
All papers examples
Disciplines

- MLA
- APA
- Master's
- Undergraduate
- High School
- PhD
- Harvard
- Biology
- Art
- Drama
- Movies
- Theatre
- Painting
- Music
- Architecture
- Dance
- Design
- History
- American History
- Asian History
- Literature
- Antique Literature
- American Literature
- Asian Literature
- Classic English Literature
- World Literature
- Creative Writing
- English
- Linguistics
- Law
- Criminal Justice
- Legal Issues
- Ethics
- Philosophy
- Religion
- Theology
- Anthropology
- Archaeology
- Economics
- Tourism
- Political Science
- World Affairs
- Psychology
- Sociology
- African-American Studies
- East European Studies
- Latin-American Studies
- Native-American Studies
- West European Studies
- Family and Consumer Science
- Social Issues
- Women and Gender Studies
- Social Work
- Natural Sciences
- Anatomy
- Zoology
- Ecology
- Chemistry
- Pharmacology
- Earth science
- Geography
- Geology
- Astronomy
- Physics
- Agriculture
- Agricultural Studies
- Computer Science
- Internet
- IT Management
- Web Design
- Mathematics
- Business
- Accounting
- Finance
- Investments
- Logistics
- Trade
- Management
- Marketing
- Engineering and Technology
- Engineering
- Technology
- Aeronautics
- Aviation
- Medicine and Health
- Alternative Medicine
- Healthcare
- Nursing
- Nutrition
- Communications and Media
- Advertising
- Communication Strategies
- Journalism
- Public Relations
- Education
- Educational Theories
- Pedagogy
- Teacher's Career
- Statistics
- Chicago/Turabian
- Nature
- Company Analysis
- Sport
- Paintings
- E-commerce
- Holocaust
- Education Theories
- Fashion
- Shakespeare
- Canadian Studies
- Science
- Food Safety
- Relation of Global Warming and Extreme Weather Condition
Paper Types

- Movie Review
- Essay
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- GCSE Coursework
- Grant Proposal
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- Essay
- GCSE Coursework
- Grant Proposal
- Interview
- Lab Report
- Literature Review
- Marketing Plan
- Math Problem
- Movie Analysis
- Movie Review
- Multiple Choice Quiz
- Online Quiz
- Outline
- Personal Statement
- Poem
- Power Point Presentation
- Power Point Presentation With Speaker Notes
- Questionnaire
- Quiz
- Reaction Paper
- Research Paper
- Research Proposal
- Resume
- Speech
- Statistics problem
- SWOT analysis
- Term Paper
- Thesis Paper
- Accounting
- Advertising
- Aeronautics
- African-American Studies
- Agricultural Studies
- Agriculture
- Alternative Medicine
- American History
- American Literature
- Anatomy
- Anthropology
- Antique Literature
- APA
- Archaeology
- Architecture
- Art
- Asian History
- Asian Literature
- Astronomy
- Aviation
- Biology
- Business
- Canadian Studies
- Chemistry
- Chicago/Turabian
- Classic English Literature
- Communication Strategies
- Communications and Media
- Company Analysis
- Computer Science
- Creative Writing
- Criminal Justice
- Dance
- Design
- Drama
- E-commerce
- Earth science
- East European Studies
- Ecology
- Economics
- Education
- Education Theories
- Educational Theories
- Engineering
- Engineering and Technology
- English
- Ethics
- Family and Consumer Science
- Fashion
- Finance
- Food Safety
- Geography
- Geology
- Harvard
- Healthcare
- High School
- History
- Holocaust
- Internet
- Investments
- IT Management
- Journalism
- Latin-American Studies
- Law
- Legal Issues
- Linguistics
- Literature
- Logistics
- Management
- Marketing
- Master's
- Mathematics
- Medicine and Health
- MLA
- Movies
- Music
- Native-American Studies
- Natural Sciences
- Nature
- Nursing
- Nutrition
- Painting
- Paintings
- Pedagogy
- Pharmacology
- PhD
- Philosophy
- Physics
- Political Science
- Psychology
- Public Relations
- Relation of Global Warming and Extreme Weather Condition
- Religion
- Science
- Shakespeare
- Social Issues
- Social Work
- Sociology
- Sport
- Statistics
- Teacher's Career
- Technology
- Theatre
- Theology
- Tourism
- Trade
- Undergraduate
- Web Design
- West European Studies
- Women and Gender Studies
- World Affairs
- World Literature
- Zoology
Virtual Network Design, Research Paper Example
Hire a Writer for Custom Research Paper
Use 10% Off Discount: "custom10" in 1 Click 👇
You are free to use it as an inspiration or a source for your own work.

Introduction
A single piece of hardware is divided into multiple instance by a technology is known as virtualization. The (OS) operating system and hardware is the same before virtualization. The division of hardware makes the resource transmission simple as, an operating system (OS) needs to utilize all resources that are available in a box. A single box with the help of resources can host several instances or nodes. For example RAM, Permanent storage space (I/O capacity), network address (Bandwidth), CPU etc. Likewise, this procedure facilitates an effective method for resource management of web application. For instance, a web application that is hosted on a relatively small node works on reduced cost of using entire box and still manages to provide resources from one node to another. In order to enhance the efficiency an unused resources in a box are moved. Optimal resource management is achieved by virtual server; we can also say that there is no requirement for deploying a web application and its components for migration of web services to some other hosts that are subjected to re-installation of new operating system. Consequently, virtualization fulfills the last process by utilizing a hypervisor. Likewise, the hypervisor hosts operating system that provides management of assets for many visitor operating systems and networks linked with system. Hence, when a network application is deployed along with virtualization technology, we can get a guest operating system powered by hypervisor. This is the major factor that provides scalability and assignment of more resources for the web application by clicking few buttons (Kusnetzky, 2011).
It is unnecessary to state that virtualization appeared in the year 1960 as here are numerous hypervisors present to select from them. The large amount accepted virtualization appliances are X men and the Virtual Box (Kusnetzky, 2011). They both are considered as an open-source projects as, well as profitable contributions through corporations such as VMware and Nimbus data systems. However the process of virtualization is actually without responsibility. In fact, some disadvantages are also associated with its implementation. For example, “a hardware box’s configuration is not clear to node users. A hardware box could be near its overall hardware limit, in which case more resources for a node could be limited, even requiring migration to another box”. In addition, it could appear as a weak virtualized resource like I/O capability. In this situation numerous nodes that are present in the identical box try to read/write on or after the similar set of hard drives thus an amplified latency is formed. Moreover, on sidebar it contains additional information on the subject virtualization and I/O capability. Moreover, countless of the last virtualization includes a number of drawbacks that are at the center of vertical and horizontal scaling policy (Blokdijk & Menken, 2010).
Network Attached Storage
In order to store a data present in web applications, initially we need to trust on DAS. As the web application grows the storage demand increases and can grow into the TEBI BYTE and PEBI BYTE range. This can be impossible for the hardware to store such amount of DAS due to several limitations associated to HBA. The data storage facility of a network application is frequently deputized towards an isolated container that helps in communication through a host container as they were rightly attached. In fact, it would simplify the large amount of data management process thus reducing hardware limitations related to HBA. This is called as NAS (Network Attached Storage). NAS is considered as a hardware box also known as application. It comprise whole of the elements and assets such as RAM, CPU, Bandwidth etc. the network file system protocols acts as communication channel among NAS and the host container.
The system protocols of network files contain less efficiency as compared to HBA or DAS protocols counter parts. Moreover, between the most prevalent system protocols of network files the Network File System (NFS) protocol is discovered for Unix/Linux file systems. Moreover, the Server Message Block (SMB) protocol for Windows files systems is also found. The protocols that are discussed above are present in hardware that are located across a network in another box and thus can allow a host to get access into files.
Storage Area Network
Storage Area Network (SAN) demonstrates an additional complex explanation intended for storing data as compare to Network Area Storage (NAS) that utilize network file system (NFS) protocols for configuring the communication between the two nodes i.e. NAS and the host. Likewise, SAN is dependent on protocols such as SCSi and other protocols that are used by DAS. Organizations save cost by deploying NAS instead of DAS and SAN. As the SAN architecture is dependent on DAS based protocols, it is called as appliance embedded with many HBA that are accomplished by providing storage that has more capacity than DSA based storage. Moreover, a SAN is recognized as a large storage solution with massive capacity (Goldworm & Skamarock, 2007).
A question comes in mind that what is the difference between NAS and SAN, as they are both separate devices. The physical architecture of NAS comprises of connected physical cables, as it is dependent on network file system (NFS) based protocols. Likewise, these features make it cost effective and more convenient to manage different storage boxes embedded with storage devices. In contrast, SAN has a physical architecture that demonstrates connection via HBA that is identical to DAS. These features make it more costly along with complex data storage management (Goldworm & Skamarock, 2007).
The NAS and SAN hybrid appliances along with architectures are now more appropriate. This permits mutually DAS type protocol support is meant for high-performance applications and for the network file system protocol support devoid of experiencing in the expenditure consequences of DAS. In addition, it also provides high storage capacities outside DAS. The dissimilarity among NAS and SAN solutions are difference in storage types.
Network Diagram
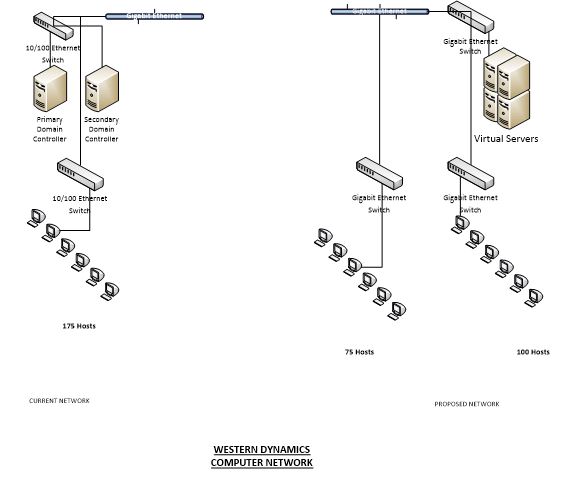
Explanation
The current network of Western Dynamics incorporates two domain controllers i.e. the primary domain controller and the secondary domain controller. Previously, it seems that these systems also host services for dynamic host configuration protocol (DHCP) and Domain Name Service (DNS). For incorporating all these services along with the domain controllers, the company wants to physically host them on a single server that is already been purchased by Western Dynamics. The configuration of the server consists of a Quad core CPU with 8 Gigabits of RAM and two network interface cards. The current diagram represents the current network as well as the proposed network. The current network is representing two domain controllers physically hosted on individual systems. Whereas, the proposed network is illustrating a single system for all the required network services. As far as network data transfer rates are concerned, we will use gigabit Ethernet that starts from 1000 Megabytes bits per second.
IP addressing Scheme
The IP address for the single virtualized machine with two network interfaces will be as follows:
Current Subnet IP addressing Scheme ranges from 192.168.1.3 to 192.168.254 with the subnet of 255.255.255.0 and with the Gateway IP of 192.168.0.1.
Proposed Subnet IP addressing Scheme will be divided in to three different subnets i.e. two groups of workstations and the server will be configured on the third subnet.
Group One for 75 Hosts
Network address: 192.168.0.0 / 25
Usable IP addresses: 192.168.0.1 – 192.168.0.126
Broadcast: 192.168.0.127
Usable IP Addresses: 125
Group Two for 100 Hosts
Network address: 192.168.1.0 / 25
Usable IP addresses: 192.168.1.1 – 192.168.1.126
Broadcast: 192.168.1.127
Usable IP Addresses: 125
Group three for Servers
Network address: 192.168.2.0 / 28
Usable IP addresses: 192.168.2.1 – 192.168.2.14
Broadcast: 192.168.2.15
Usable IP Addresses: 13
Adding more servers to the current virtualized environment
We have already addressed the requirement for expansion of the network in the future. For this reason, we have a group one network address of 192.168.1.0 / 25 that will spare 50 IP addresses. Similarly, for group two network address of 192.168.1.0 / 25, we have 25 spare IP addresses. For the group three networks we only need two IP addresses i.e. for primary and secondary domain controller, it concludes that we have 11 spare IP addresses. The virtualization architecture requires an instance of an operating system for loading purpose. Once the operating system is loaded on one instance, we need to configure it and assign hardware resources to the specific application. The virtualization application then requires a network interface settings i.e. IP address, subnet mask, gateway, DNS IP addresses as well. Once configured, the application is operational on the network. For adding a server in any one of the three groups, we need to assign the IP pool associated with that group. Likewise, we have three different subnets for all the three groups. Moreover, the rest of the procedure will be same, it consists of network settings, hardware settings, application settings and load balancing is also available. Moreover, for supporting the disaster recovery plan that may be drafted in the future, the virtualized environment will definitely add value by minimizing total cost of ownership, low administration overhead, minimized recovery time objectives, and maximizing recovery point objectives. An example for taking backups of the virtual network is very easy, as Western Dynamics requires backup of certain mission critical data, the network administrator will only replicate a single file compatible with the virtual application format. For instance, Microsoft ESXi Vmware has its own file extensions that can only be loaded on a Microsoft based platform. I would like to recommend Hewlett Packard to be the vendor for this product. As HP is a renowned name in the industry and deploys best practices for installation and configuration of Microsoft Vmware ESXi. Moreover, HP is a reliable name with a reputable after sales support and maintenance for any known issues that may occur. Ranging from corporate business solutions and small and medium businesses, their expert consultants provide advice and recommendation for known issues and risks that may occur during migration to Vmware. For the converged infrastructure, HP may recommend ways that may prevent additional cost. Furthermore, HP also provides support for specific situations, for instance, there are support communities that may help solve issues that are common on a wide scale, product and troubleshooting tab provides ample amount of information and guidance for specific products and system software with other supported tools and applications are also archived at the website.
Security
The primary objective for Western Dynamics virtual network is the identification of threats such as unauthorized access of employees; create session and activity logs for employees, surveillance of critical servers by infrared cameras, prevention of wireless networks by encrypting the connections. However, an intelligent firewall has a capability of supporting packet filtering capability that intrudes in each data packet and then decides for allowing or granting access. Likewise, there are teams such as computer incident response team that responds to any threat or incident occurs within the premises of Western Dynamics. For baseline security, Western Dynamics requires an authentication policy for enforcing best practices to assign access rights to employees. Moreover, there is also a requirement of a security policy framework that will administer all deployed policies for the Western Dynamics virtual network. The security policy framework will also facilitate and issue User ID and passwords for every request and the deployment of an access control policy will only be applicable by a technological aspect i.e. a full functional domain controller. As per the scenario, we have a virtual domain controller; it will recognize every network node on the network such as network switch, network printers, workstation NIC and any other available device. Furthermore, Microsoft Active Directory will facilitate the network team to configure security settings on files available on the network. Restriction of Internet can be enforced by Microsoft ISA server that will only serve as a baseline security control. Allowing Internet to everyone will impose several threats and opens a door for viruses that can be penetrated via a web browser. In addition, we have three different groups, it is recommended to create three separate groups and add the associated user accordingly. This will allow network team to allow/grant network services.
Conclusion
We have designed a virtualized computer network for Western Dynamics that will reduce costs, infrastructure cost, facility cost, hardware / software maintenance cost, low cost of ownership, low technical overhead and provide for a smaller carbon foot print. Moreover, 3 different subnets were also calculated for three different groups. Furthermore, addition of a server in the virtual environment is also discussed, as it is relatively very easy via a Microsoft ESXi VMware. In addition, we have also discussed the security aspects for the network, as everything is centralized, hacker may need a single loop hole to exploit any vulnerability that is present in any one of the OS mounted virtually on a single server.
References
Blokdijk, G., & Menken, I. (2010). Virtualization – the complete cornerstone guide to virtualization best practices: Concepts, terms, and techniques for successfully planning, implementing and managing enterprise IT virtualization technology – second edition Art of Service.
Goldworm, B., & Skamarock, A. (2007). Blade servers and virtualization: Transforming enterprise computing while cutting costs Wiley.
Kusnetzky, D. (2011). Virtualization: A manager’s guide O’Reilly Media, Incorporated.

Stuck with your Research Paper?
Get in touch with one of our experts for instant help!

Time is precious
don’t waste it!
writing help!


Plagiarism-free
guarantee

Privacy
guarantee

Secure
checkout

Money back
guarantee

