 All papers examples
All papers examples
Disciplines

- MLA
- APA
- Master's
- Undergraduate
- High School
- PhD
- Harvard
- Biology
- Art
- Drama
- Movies
- Theatre
- Painting
- Music
- Architecture
- Dance
- Design
- History
- American History
- Asian History
- Literature
- Antique Literature
- American Literature
- Asian Literature
- Classic English Literature
- World Literature
- Creative Writing
- English
- Linguistics
- Law
- Criminal Justice
- Legal Issues
- Ethics
- Philosophy
- Religion
- Theology
- Anthropology
- Archaeology
- Economics
- Tourism
- Political Science
- World Affairs
- Psychology
- Sociology
- African-American Studies
- East European Studies
- Latin-American Studies
- Native-American Studies
- West European Studies
- Family and Consumer Science
- Social Issues
- Women and Gender Studies
- Social Work
- Natural Sciences
- Anatomy
- Zoology
- Ecology
- Chemistry
- Pharmacology
- Earth science
- Geography
- Geology
- Astronomy
- Physics
- Agriculture
- Agricultural Studies
- Computer Science
- Internet
- IT Management
- Web Design
- Mathematics
- Business
- Accounting
- Finance
- Investments
- Logistics
- Trade
- Management
- Marketing
- Engineering and Technology
- Engineering
- Technology
- Aeronautics
- Aviation
- Medicine and Health
- Alternative Medicine
- Healthcare
- Nursing
- Nutrition
- Communications and Media
- Advertising
- Communication Strategies
- Journalism
- Public Relations
- Education
- Educational Theories
- Pedagogy
- Teacher's Career
- Statistics
- Chicago/Turabian
- Nature
- Company Analysis
- Sport
- Paintings
- E-commerce
- Holocaust
- Education Theories
- Fashion
- Shakespeare
- Canadian Studies
- Science
- Food Safety
- Relation of Global Warming and Extreme Weather Condition
Paper Types

- Movie Review
- Essay
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- GCSE Coursework
- Grant Proposal
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- Essay
- GCSE Coursework
- Grant Proposal
- Interview
- Lab Report
- Literature Review
- Marketing Plan
- Math Problem
- Movie Analysis
- Movie Review
- Multiple Choice Quiz
- Online Quiz
- Outline
- Personal Statement
- Poem
- Power Point Presentation
- Power Point Presentation With Speaker Notes
- Questionnaire
- Quiz
- Reaction Paper
- Research Paper
- Research Proposal
- Resume
- Speech
- Statistics problem
- SWOT analysis
- Term Paper
- Thesis Paper
- Accounting
- Advertising
- Aeronautics
- African-American Studies
- Agricultural Studies
- Agriculture
- Alternative Medicine
- American History
- American Literature
- Anatomy
- Anthropology
- Antique Literature
- APA
- Archaeology
- Architecture
- Art
- Asian History
- Asian Literature
- Astronomy
- Aviation
- Biology
- Business
- Canadian Studies
- Chemistry
- Chicago/Turabian
- Classic English Literature
- Communication Strategies
- Communications and Media
- Company Analysis
- Computer Science
- Creative Writing
- Criminal Justice
- Dance
- Design
- Drama
- E-commerce
- Earth science
- East European Studies
- Ecology
- Economics
- Education
- Education Theories
- Educational Theories
- Engineering
- Engineering and Technology
- English
- Ethics
- Family and Consumer Science
- Fashion
- Finance
- Food Safety
- Geography
- Geology
- Harvard
- Healthcare
- High School
- History
- Holocaust
- Internet
- Investments
- IT Management
- Journalism
- Latin-American Studies
- Law
- Legal Issues
- Linguistics
- Literature
- Logistics
- Management
- Marketing
- Master's
- Mathematics
- Medicine and Health
- MLA
- Movies
- Music
- Native-American Studies
- Natural Sciences
- Nature
- Nursing
- Nutrition
- Painting
- Paintings
- Pedagogy
- Pharmacology
- PhD
- Philosophy
- Physics
- Political Science
- Psychology
- Public Relations
- Relation of Global Warming and Extreme Weather Condition
- Religion
- Science
- Shakespeare
- Social Issues
- Social Work
- Sociology
- Sport
- Statistics
- Teacher's Career
- Technology
- Theatre
- Theology
- Tourism
- Trade
- Undergraduate
- Web Design
- West European Studies
- Women and Gender Studies
- World Affairs
- World Literature
- Zoology
Network Security in an Office Setting, Research Paper Example
Hire a Writer for Custom Research Paper
Use 10% Off Discount: "custom10" in 1 Click 👇
You are free to use it as an inspiration or a source for your own work.

Network security is vital to any successful organization as proper planning and execution is needed to accelerate infrastructure and configuration for efficiency and effective savings. Intel Corporation (2007) is a leading IT development corporation who portrays an innovative idea to develop a wireless LAN (Local Area Network) for small offices, which delivers an estimated 43 percent net savings over 4 years, which accelerated time from months to days.
The network solution which is the most efficient in addressing the wireless network security is Cisco 3845 Integrated Services Router which uses high-level topology of the Cisco architecture, which also includes Light weight Access point protocols, the Wireless Control System and the Wireless LAN Controller, as well as the Cisco Access Control Server and its Authentication, Authorization and Accounting features the solution by providing RADIUS services, as mentioned by the Intel Corporation (2007). The schematic integration of the 48-power port over Ethernet (PoE) Fast Ethernet switch module for supplying the required LAN ports capabilities and connecting WLAN access points, that delivers VOIP, Unity Express, a voice mail, wireless controller module, voice and fax extension modules for direct analog fax machines connections as stated by Intel Corporation (2007). Below mentioned are the requirements of the Cisco 3845 ISR system confirming its architecture.
- High-availability system that recovers from access points failures or system interferences.
- 5 GHz 802.11a and 2.4 GHz 802.11g connection
- Client support includes “desktops, laptops, personal digital assistants, and Wi-Fi* phones (2007)”
- The system also has seamless out-of-the-box installation and clearly identifiable control access points.
- Central management servers also have tracking capability. It can be used for blacklisting clients, and mitigating security offenses.
- Sufficient 100/1000 switch ports to support servers, printers, and other office devices; at least 10
- Support for numerous digital LANs for different vocal and data activities, power over Ethernet (PoE) 802.3af, Quality of Service (QoS) 802.1p, and port verification 802.1x
- Support for different IP routing initiatives, that include Routing Information Protocol (RIP) version 2, Enhanced Interior Gateway Routing Protocol (EIGRP), and Open Shortest Path First (OSPF)
- Server abilities with Dynamic Host Configuration Protocol (DHCP). This includes vendor-specific capabilities.
- IP multicast system assistance and Internet Group Management Protocol (IGMP) snooping.
- The system has support for WAN technologies that are affordable., that includes asynchronous exchange mode (ATM), frame distribution, and integrated providers of the digital network (ISDN). Preferred WAN technologies can be deployed but may depend primarily on the service provider. Certain carriers offering service available to the site depend onservice availability, cost, location , and service level contracts.
- Certain bandwidth for small offices is usually between 1 and 45 megabits per second (Mbps)
- QoS packet classification is a key aspect of the system as well.
- Encryption using IP Security (IPsec)
- The system provides multicast support
- It should have voice trucking
- I should also have the ability for working as a standalone gatekeeper. This should apply even with remote gatekeepers.
- Support for popularly used codec’s: G.711, G.726, G.729, and special wideband codecs.
- It should have support for Session Initiation Protocol (SIP) endpoints
- Emergency services such call routing, voice mail capabilities, automated attendant access, and conference calls support.
- Remote management can also be provided, with secure management access.
- Support for various arays of access controls
The internet protocol journal (2006) mentions the Centralized architecture which is a hierarchical architecture that involves a WLAN controller which is responsible for configuration,
control and management of several WTPs. The Access points receive their addresses dynamically from a Dynamic Host Configuration Protocol and they automatically detect the controller, which is integrated inside the router; the primary wireless service follows the protocol on the 5.2 GHz 802.11a band and is secured using full 802.11i encryption. RADIUS servers that are shared between LAN and WLAN perform user authentication, and are available on the 2.4 GHz 802.11b and 802.11g band and go thru firewalls for more security, as stated by Wireless LAN design (n.d.).
The following is the model for the Cisco 3845 Integrated Services router as the separation of WAN from LAN is highly encouraged in order to avoid excess wiring, simplify network implementation, and increase agility. As the WLAN requires the Wireless Network username and password every time people try to access it, the firewalls always protect the invaders from misusing the wireless system.
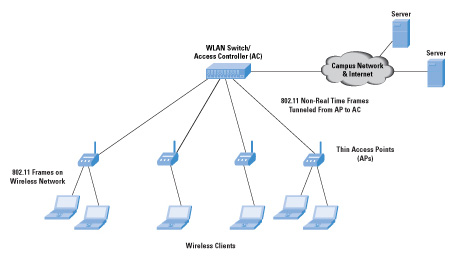
(The Internet Protocol Journal, 2006)
An ultimate way to enhance security feature on the Cisco 3845 Integrated Services system is to disable/ filter SNMP (HTTP) management, keeping AP (access point) firmware updated and the correct configuration of the BSSIS (MAC address of AP) as mentioned by Patterson & Poudel (2000).
References
Intel Corporation. (2007). Network in a box: Wireless LAN architecture for Small Offices. Retrieved from: http://www.intel.com/it/pdf/network-in-a-box.pdf
Patterson, M., & Poudel, R. (2000). Wireless Network Design & Architecture: Sanog. Retrieved from: http://www.sanog.org/resources/sanog6/peterson-poudel-wireless-archi-tutorial.pdf.
Sridhar, T. (2006). Wireless LAN Switches –Functions and Development. The Internet Protocol Journal, 9(3).
Wireless LAN design. (n.d.). Wireless LAN design. Cisco Unified Wireless Network Architecture (Chap. 5). Retrieved from: http://www.cisco.com/en/US/docs/solutions/Enterprise/Education/SchoolsSRA_DG/SchoolsSRA_chap5.pdf

Stuck with your Research Paper?
Get in touch with one of our experts for instant help!

Time is precious
don’t waste it!
writing help!


Plagiarism-free
guarantee

Privacy
guarantee

Secure
checkout

Money back
guarantee

