Network Security, Research Paper Example
Abstract
Burger King is a global chain of fast food restaurants that are located all around the world. It was founded in United States and, as per statistics; burger king is the second largest after McDonalds that is also a fast food chain founded in the UK. For proposing network security, we have selected four branches of Burger King and named them as follows, Building A (Regional Office), Building B (Site Office) building C (Site Office) and Building D (Warehouse). By utilizing quantitative and qualitative research methods, we will analyze different aspects of information security within the company. We have also constructed a holistic information security policy for Burger King. Likewise, the policy will address internal threats and vulnerabilities, password complexity and outside threats. As network vulnerabilities are constantly at a rise, network security vulnerabilities are evaluated in three categories i.e. logical security, internal security and external security. The logical security domain will cover technical controls such as deployment of IDS, Virtual LAN, monitoring violation logs, auditing on domain environment, ISA server and VPN security as well. Secondly, internal and physical security will discuss human threats, physical access to server rooms and servers, sensors and sprinklers etc. Moreover, protecting accidently shutting down system will also be discussed. After evaluating vulnerabilities associated with these three domains, controls will be proposed and justified accordingly. Furthermore, incorporation of Burger King Architecture will also be utilized for better insights.
Introduction to Organization
Currently, Burger King is utilizing a Virtual Private Connection that is connecting one or more sites. However, the VPN connection is also entitled to allow internet traffic on the same dedicated line from the Internet Service Provider. Moreover, the current network only utilizes a single firewall that is located at the regional branch. It concludes that the rest of the two remote sites are only protected via a simple Network address translation function that is incorporated in a DSL modem. Moreover, there is no advanced security devices, for instance, Host based/ Network based Intrusion detection systems for analyzing and monitoring any suspicious activity that may possibly become a threat to Burger King’s computer network. Moreover, there is no patch management for updating security patches in the workstations connected to the network. There are no indications of hardening servers for instance, email server, application server, centralized server and database server must be hardened and needs physical protection as well. In addition, the recent twitter hack concluded that the staff is not aware of information security and there is no such policy and enforcement for setting secure passwords.
Business Issue and Technical Approach
We will utilize Burger King Computer network in our research as a basis of our discussions. Moreover, we will focus on qualitative research on information security, tools, assessments and statistical data in some cases. It has been concluded by some experts that the year 2012 is considered to be the worst year in terms of computer network security breaches (Schirick, 2012). Likewise, the year that has not even passed the half year mark, some of the foremost companies were sufferers of network security breaches resulting in massive losses (Schirick, 2012). However, the news buzz only highlights Sony and Citibank to be victims of network security breaches, as these companies are popular among the public. The other sides of the picture highlights organizations of all sizes are affected by the consequences of network security breaches. Likewise, it can be concluded that network security risks are continuously evolving, modifying and growing at a rapid pace. Organizations normally install a firewall and even intrusion detection systems that triggers alerts of any suspicious activity, as these two components only covers the technical domain and not the human and physical domain. The current network scenario is utilizing a Virtual Private Connection that is connecting one or more sites. However, the VPN connection is also entitled to allow internet traffic on the same dedicated line from the Internet Service Provider. Moreover, the current network only utilizes a single firewall that is located at the regional branch of Burger King. It concludes that the rest of the two remote sites are only protected via a simple Network address translation function that is incorporated in a DSL modem. Moreover, there are no advanced security appliances such as Intrusion detection systems for analyzing and monitoring any suspicious activity that may possibly become a threat to Burger King. Moreover, there is no patch management for updating security patches in the workstations connected to the network. There are no indications of hardening servers for instance, email server, application server, centralized server and database server must be hardened and needs physical protection as well. Most importantly, there is no information security policy and password policy as well.
The network security vulnerabilities will be accessed in three categories i.e. logical security, internal security and external security. As far as logical security is concerned, we can see that the fig 1.1 demonstrates a firewall, Microsoft Internet Security and Acceleration (ISA) server and a domain controller with Microsoft Active Directory. The three categories for network vulnerabilities are categorized.
Logical Vulnerabilities
The current logical controls for protecting information assets within the network are Microsoft Active directory, ISA server and a Firewall. The Microsoft active directory is not primarily a security control, as it does not mitigate any risks associated with viruses, worms, Trojans, phishing, spam, denial of service attacks etc. however, it provides a secure administration of user profiles and File sharing features (Smith, 2010). File sharing threats are spreading on a rapid pace, as every now and then, new file sharing technologies are getting being developed and in demand. Controls will not only provide value from all network based services, but will also augment productivity for the organization in terms of revenue, customer loyalty and competitive advantage. Workgroup based environment is not centralized. For instance, users can only login, if they have account created on that specific computer. As far as security is concerned, there are no passwords, resulting in anyone to log on the network. Moreover, workgroup only recognize twenty to twenty five computers that are on the same subnet. For instance, we have application servers that are on the different subnet, users will not be able to access applications, as they are configured on a different subnet. On the other hand, Domain based environment provides centralized administration and access for users. All staff has to enter user credentials, in order to identify themselves on the network before doing any work. Moreover, computers with different subnet are supported and thousands of computers can be connected on the domain based environment. For instance, if a computer stops responding, employees or users can log on from some other computer and no work is halted. Therefore, Domain based network environments are more effective and are compatible to the current network scenario. Moreover, if security auditing features are enabled, user activity and system logs are saved and monitored. Likewise, the lightweight directory access protocol ensures encryption all the way from the domain controller to the workstations via Kerberos. However, network or system security specialist will not be able to monitor, analyze or examine threats from a domain environment. Active directory prevents unauthorized access because users have to provide login credentials for accessing personal file settings, data and customized permitted objects in the operating system. Secondly, the ISA server that can be considered as a firewall and a proxy server as well due to support of cache management functions. As per the current scenario, the suspicious packets are handled by the firewall, as it is separately installed. (Internet security and acceleration server.2007) The ISA server is only implemented to enable access management to different services associated with Internet, file sharing etc. ISA server will only prevent unauthorized access to different network services, for example, Internet access. We have covered two logical controls in the current network scenario up till now. The third security control that we have identified is a hardware based firewall. The firewall operates on chain of rules that are defined by the security specialist, consultant or a vendor. The configuration is carried out for restricting or dropping unwanted packets and suspicious packets. However, legitimate packets are allowed for entering tin the network. The firewall only operates on rules and if any suspicious packet hides itself within other packet may enter in the network.
Logical vulnerabilities include no additional security controls on firewall, critical servers, and network devices. If any suspicious packet bypasses the firewall, there are no mechanisms to track and monitor the probe of a hacker trying to breach into the core systems. Moreover, building B and building C have not a single security control. This concludes that only Network address translation (NAT) is the only logical security control, whose main purpose is to hide private IP addresses of the local area network and relay the traffic via a global IP address. Suppose, if a threat bypasses a firewall that is located at the main site, there is a high probability and risk that the data residing at the two buildings i.e. building B and building D will also be compromised. Moreover, if any employee or personnel plugs in the suspicious USB drive in one of the system, there is no mechanism or tools to monitor internal network threats, as it has been proved that internal threats are relatively more probable than external threats. Furthermore, there are no tools for demonstrating events and alerts associated with violation logs. In addition, there are no logical controls linked with the database, as SQL injection techniques have proven to exploit data from the database. Furthermore, for logical vulnerability there is an absence of Virtual local area networks. VLAN’s provide adequate security, “Virtual LAN (VLAN) refers to a logical network in which a group of devices on one or more LANs that are con?gured so that they can communicate as if they were attached to the same wire, when in fact they are located on a number of different LAN segments. Because VLANs are based on logical, instead of physical, connections, they are very ?exible for user/host management, bandwidth allocation and resource optimization” (Virtual LAN, 2007). VLAN’s separates traffic for each department an also prevent denial of service attacks and unwanted traffic broadcast that may result in network congestion and degradation of network services.
Internal and Physical Security
The internal security is associated with adequate protection from internal threats i.e. humans. It has been evaluated that organizations emphasize only on physical and logical security and often skips adequate protection of internal human controls from threats such as unauthorized access, theft, espionage etc. In the current scenario, there are no security controls addressing human security. Likewise, there are no mounted racks for locking up servers, network components and Ethernet wires. As Ethernet wires can be tapped, an appropriate way is to install patch panels for CAT 5 cables. Moreover, theft of any critical hardware or software component is easy, as there are no biometric systems available in the premises. Biometric identification systems are considered to be the best physical security control till date. Moreover, there are no surveillance cameras installed on critical locations, as they prevent physical theft of systems as well as identify disasters. For instance, if fire occurs due to any short circuit in one of the critical information assets, it can be controlled in an early stage. However, sensors, water sprinklers and fire extinguishers are considered to be ideal controls in this scenario.
Intrusion detection system
Security in terms of computer networks has marked its significance. Senior management address security issues to an optimal level and enforces strict security procedures in order to protect strategic and financial assets. Likewise, new and improved sensing technologies are now mandatory for Burger King Computer network for maintaining the security of network. Consequently, an intrusion detection system is required for continuously monitor threats and vulnerabilities within the Burger King Computer network. IDS/IPS derived from the traditional security appliances and is defined as “Intrusion detection system (IDS) is a type of security management system for computers and networks. An IDS gathers and analyzes information from various areas within a computer or a network to identify possible security breaches, which include both intrusions and misuse” (Intrusion Detection System, 2007). Figure 1.1, demonstrates the physical location of the IDS (indicated in Red) in Burger King Computer network.
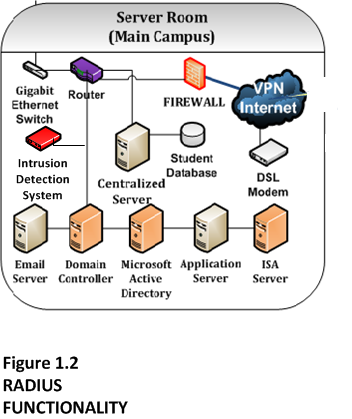
Figure 1.1
The IDS embedded with signatures provides analysis on detecting specialized patterns or anomalies that are similar to the signatures. The parameters for detecting attacks consist of different port numbers, different protocols, raw data and other factors. Moreover, the signature based IDS also detects any anomaly that is dissimilar to previous anomaly. Furthermore, for monitoring, the network is scanned by complex algorithms and all the signatures are stored in one location that is called as repository for signatures. Conclusively, the primary task of this IDS is to match the anomalies of attacks by signature stored in the as repository for signatures.
Anomaly based intrusion detection system is based on data driven methodology that complies with data mining techniques. The functionality of an anomaly based IDS involves in the creation of profiles associated with normal behavior and activities within the network. If any unknown activities initializes that is not similar to the normal profiles, is considered as anomalies or attacks. Moreover, the normal routines of normal profiles are also monitored, if they also exceeds from their given boundaries, they are also considered as anomalies also called as false positives. An efficient anomaly based IDS may extract results containing high detection success rate along with low false positive rate. Moreover, these systems are categorized in to various sub categories including data mining, statistical methodologies, artificial neural networks, immune systems and genetic algorithms. Among all of these, statistical methods are more commonly used for detecting intrusions by finding out any anomaly that has initiated within the network (Ayd?n, Zaim, & Ceylan, 2009). By combining these two types of IDS, network administrators eliminate or fill vulnerabilities within the network. Anomaly based intrusion detection system will be recommended for Burger King computer network, as the signature based IDS only works on the given signatures and will not sense any unusual activity if it is not defined in the signature. Anomaly based IDS will detect every threat that is referred as anomaly within the network.
Physical Security
A bio metric identification system is required prior to entrance in the Burger King Computer network server room. Moreover, surveillance cameras must be installed for monitoring the server room. Furthermore, for addressing fire or electricity incidents, temperature sensors and water sprinklers must be installed near critical systems and applications. The bio metric system will restrict unauthorized personnel for entering in the server room and consequently, the risk of physical theft associated with computing devices or equipment will be minimized. In addition, a proper review of access logs for bio metric systems is also necessary, as it will identify how many times a particular employee is entering or exiting from the server room or any other department. Guards will provide adequate security for the building of Burger King and will only allow relevant people enter in to the building. One more aspect that needs to be discussed is the power button of critical applications that are operational every second. For instance, personnel or support staff from the third party started working on the server and accidently his hand presses the power button will result in halting of educational operations. For this reason, protective covers must be deployed on power buttons of each server. If the server needs to be restarted, there is an approval process that will be accepted or rejected by the relevant system or application owner. After granting approval, server can be re booted.
Burger King Information Security Policy
Purpose of Establishing Information Security Policy
Burger King needs an information security policy to secure information resources from threats, as it will build confidence in stakeholder confidence and customers. Moreover, by securing information resources, competitive advantage can be achieved in the market, that will result in maximizing profitability along with trust in data. Security of the organization should not focus on Information technology only. Some of the sources of threats includes vandalism, sabotage, espionage, natural disasters, online frauds, phishing etc. however, cyber criminals can also compromise networks while data in transit. Some of the threats are non-ethical hacking, viruses, Trojan, malicious codes, and denial of service attacks.
Success Factors
- Critical success factors for the effective and successful application of security within Burger King are:
- Complete and comprehensive security policy, security objective that aligns with Burger King’s business objectives
- A methodology that is steady and aligns with Burger King culture
- Comprehensively Visible Senior management support for Burger King
- Highly visible support from Burger King executive management
- Comprehensive and in-depth knowledge of risk management and security requirement practices
- Communicating security requirements to Burger King Managers, business partners, customers, software developers and outsourcing companies.
- Assistance and guidance to all Burger King Managers, business partners, customers, software developers and outsourcing companies.
- Awareness and training on Information security
- Measuring the effectiveness of information security by periodic reviews of controls and mechanisms
- Setting strong passwords by enforcing complex password requirements on social media and other digital channels as well.
- Identifying weak areas and adjustment on Burger King modified business objectives where necessary
- For updating or modifying the policy, Annual review of the information security policy of Burger King for addressing changed business objectives along with risk environments
Information Security Policy
Scope
This policy is applicable to all information resources, systems that are internally connected, Burger King, employees and third parties who have access to Burger King. The scope of this policy will also cover all the legacy and future equipment that will be configured and tuned as per the reference documentation.
Policy
Ownership
The first factor that must be addressed is the ownership criteria. Burger King is responsible for recruiting or assigning an information security manager, a point of contact for communication and an alternate point of contact in case of unavailability of the primary point of contact. Employees who are assigned as the owners of the systems must organize and update the point of contact on regular basis in order to align with the information security and corporate enterprise management members or groups. Information security manager must be available all the time i.e. round the clock, either via phone or on office hours. In case of absence, alternate manager must be functional to avoid hindrance to production operations. In case of any lack of mismanagement, legal action is applicable against the employee.
Moreover, Information security managers are also liable for the vital factor that is the security of the information resources of Burger King and the impact of its operations on the production functions and operations that are functional on the network and any other associated network services. However, in a situation where no specific requirements are addressed in the policy, managers must do their best for safe guarding information security of Burger King, from security weaknesses and vulnerabilities.
Information security managers are also liable for aligning security policies in compliance with Burger King, security policies. The following policies are vital: Password policy of networking devices and hosts, wireless network security policy, Anti-Virus security policy and physical security policy.
The information security manager of Burger King is responsible for granting and approving access to employees requiring access for information or business purpose. Access can be either short term or long term depending on the ongoing job description or responsibilities. Moreover, information security manager will also ensure effective procedures for terminating/revoking unwanted access to the Burger King resources.
The network support staff or administration must monitor and maintain a firewall between the network that connects the production functions, processes and operations from the Burger King Network or network appliance / equipment / device.
The network support staff or administration must be entitled to have full rights for interrupting network connections of the Burger King that may impose impact or security risk on processes, functions and operation on the production network
The network support and administration staff must maintain and record all the IP addresses that are operational in the Burger King, any database associated with routing information from these IP addresses.
Network access of Burger King by departmental or external organizations to or from the network must provide a business case including justification of access with network diagrams and equipment to the information security management who will review the requirements for security issues and concerns and give approval prior to the deployment of the connection.
User passwords must meet the requirements of the access management or password policy of Burger King, password policy. Moreover, any inactive account must be deleted within 2 days from the access list and any device that involves critical and sensitive information of Burger King, passwords of group based accounts from the group membership modules must be modified within 24 hours.
The customized network of Burger King will not facilitate third party or outsourced organization apart from network and data transmission, storage, modification, monitoring and protection. All the other departments of Burger King will be facilitated by their respective support functions.
In case of non-compliance, information security management must consider business justifications and allow waivers accordingly.
Conclusion
We have adopted a business and technical approach for identifying vulnerabilities in logical, physical and internal security of Burger King Computer network. In order to add an extra layer of security and defense, we have considered IDS/IPS. Likewise, we have also discussed types of IDS and recommended the best one. Moreover, for addressing information security for all aspects, we have developed a comprehensive information security policy that will address all issues and can be utilized by other global restaurant chains as well. Furthermore, for addressing physical and internal security, Bio metric systems are recommended along with surveillance cameras monitoring server rooms. Furthermore, a deployment of firewall each is recommended for computer networks.
References
Ayd?n, M. A., Zaim, A. H., & Ceylan, K. G. (2009). A hybrid intrusion detection system design for computer network security. Computers & Electrical Engineering, 35(3), 517-526. doi: 10.1016/j.compeleceng.2008.12.005
Intrusion Detection System. 2007. Network Dictionary, , pp. 258-258.
Internet security and acceleration server. (2007). Network Dictionary, , 255-255.
Remote Authentication Dial In User Service Security. 2007. Network Dictionary, , pp. 409-409.
SCHIRICK, E.A., 2012. Computer Network Security — Evolving Risks. Camping Magazine, 85(2), pp. 16.
Smith, R. (2010). Advanced active directory security. Windows IT Pro, 16(10), 28-31.
Virtual LAN. 2007. Network Dictionary, , pp. 515-515.

Time is precious
don’t waste it!

Plagiarism-free
guarantee

Privacy
guarantee

Secure
checkout

Money back
guarantee






