All papers examples
All papers examples
Disciplines

- MLA
- APA
- Master's
- Undergraduate
- High School
- PhD
- Harvard
- Biology
- Art
- Drama
- Movies
- Theatre
- Painting
- Music
- Architecture
- Dance
- Design
- History
- American History
- Asian History
- Literature
- Antique Literature
- American Literature
- Asian Literature
- Classic English Literature
- World Literature
- Creative Writing
- English
- Linguistics
- Law
- Criminal Justice
- Legal Issues
- Ethics
- Philosophy
- Religion
- Theology
- Anthropology
- Archaeology
- Economics
- Tourism
- Political Science
- World Affairs
- Psychology
- Sociology
- African-American Studies
- East European Studies
- Latin-American Studies
- Native-American Studies
- West European Studies
- Family and Consumer Science
- Social Issues
- Women and Gender Studies
- Social Work
- Natural Sciences
- Anatomy
- Zoology
- Ecology
- Chemistry
- Pharmacology
- Earth science
- Geography
- Geology
- Astronomy
- Physics
- Agriculture
- Agricultural Studies
- Computer Science
- Internet
- IT Management
- Web Design
- Mathematics
- Business
- Accounting
- Finance
- Investments
- Logistics
- Trade
- Management
- Marketing
- Engineering and Technology
- Engineering
- Technology
- Aeronautics
- Aviation
- Medicine and Health
- Alternative Medicine
- Healthcare
- Nursing
- Nutrition
- Communications and Media
- Advertising
- Communication Strategies
- Journalism
- Public Relations
- Education
- Educational Theories
- Pedagogy
- Teacher's Career
- Statistics
- Chicago/Turabian
- Nature
- Company Analysis
- Sport
- Paintings
- E-commerce
- Holocaust
- Education Theories
- Fashion
- Shakespeare
- Canadian Studies
- Science
- Food Safety
- Relation of Global Warming and Extreme Weather Condition
Paper Types

- Movie Review
- Essay
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- GCSE Coursework
- Grant Proposal
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- Essay
- GCSE Coursework
- Grant Proposal
- Interview
- Lab Report
- Literature Review
- Marketing Plan
- Math Problem
- Movie Analysis
- Movie Review
- Multiple Choice Quiz
- Online Quiz
- Outline
- Personal Statement
- Poem
- Power Point Presentation
- Power Point Presentation With Speaker Notes
- Questionnaire
- Quiz
- Reaction Paper
- Research Paper
- Research Proposal
- Resume
- Speech
- Statistics problem
- SWOT analysis
- Term Paper
- Thesis Paper
- Accounting
- Advertising
- Aeronautics
- African-American Studies
- Agricultural Studies
- Agriculture
- Alternative Medicine
- American History
- American Literature
- Anatomy
- Anthropology
- Antique Literature
- APA
- Archaeology
- Architecture
- Art
- Asian History
- Asian Literature
- Astronomy
- Aviation
- Biology
- Business
- Canadian Studies
- Chemistry
- Chicago/Turabian
- Classic English Literature
- Communication Strategies
- Communications and Media
- Company Analysis
- Computer Science
- Creative Writing
- Criminal Justice
- Dance
- Design
- Drama
- E-commerce
- Earth science
- East European Studies
- Ecology
- Economics
- Education
- Education Theories
- Educational Theories
- Engineering
- Engineering and Technology
- English
- Ethics
- Family and Consumer Science
- Fashion
- Finance
- Food Safety
- Geography
- Geology
- Harvard
- Healthcare
- High School
- History
- Holocaust
- Internet
- Investments
- IT Management
- Journalism
- Latin-American Studies
- Law
- Legal Issues
- Linguistics
- Literature
- Logistics
- Management
- Marketing
- Master's
- Mathematics
- Medicine and Health
- MLA
- Movies
- Music
- Native-American Studies
- Natural Sciences
- Nature
- Nursing
- Nutrition
- Painting
- Paintings
- Pedagogy
- Pharmacology
- PhD
- Philosophy
- Physics
- Political Science
- Psychology
- Public Relations
- Relation of Global Warming and Extreme Weather Condition
- Religion
- Science
- Shakespeare
- Social Issues
- Social Work
- Sociology
- Sport
- Statistics
- Teacher's Career
- Technology
- Theatre
- Theology
- Tourism
- Trade
- Undergraduate
- Web Design
- West European Studies
- Women and Gender Studies
- World Affairs
- World Literature
- Zoology
Networking Assignment and Wireshark Lab, Quiz Example
Hire a Writer for Custom Quiz
Use 10% Off Discount: "custom10" in 1 Click 👇
You are free to use it as an inspiration or a source for your own work.

Question1
Subnet
An internal connection is called a subnet. Networks become more effective with subnetworks. Thanks to subnetting, a communication network can go a smaller area to its destinations without using extraneous routers.
Prefix
Prefix serves as a unit of measure for huge numbers. In networking, prefixes like 10.0.0/8 and 10.0.0/24 are employed to characterize many hosts and networks.
BGP route
The gateway mechanism known as Border Gateway Protocol (BGP) allows the internet to transmit routing data among autonomous computers (AS). Systems connect a method of communication whenever they communicate with one another. Peering provides for the accomplishment of this.
Question2
The matched interface for the five host addresses.
(These addresses are shown in order from Link Interface through Destination Address Ranges.)
01110000 to 10111111 0
10100000 to 10111111 1
11000000 to 10111111 2
11010000 to 10111111 2
11110000 to 10111111 3
Question3
- MAC address space is 48bits long. They are divided into two halves: the Organizationally Distinctive Identification (OUI) formed by the initial 24 bits and the serial number formed by the final 24 bits (formally called an extension identifier).
- Ipv4 is 32bit long. There are 4,294,967,296 (232) different numbers available in the 32-bit Ipv4 and ipv6 space, although significant blocks are set aside for technical network communication.
- The ipv6 address is 128bit long. Consequently, there really are 2128=340,282,366,920,938,463,463,374,607,431,768,211,456 addresses in the main memory (or roughly 3.41038 addresses). This satellite’s blocks and some particular addresses are set aside for special purposes.
Question4
After the fifth interaction, the node will select a K value randomly between 0 to 31 (i.e., 0 to 1, 1, 2,…, 25 – 1). The node will now wait for K*512-bit intervals following selecting K=4. The bit rate of Ethernet at 10 Mbps is 0.1 microseconds. As a result, the total node’s average wait time is 4 * 512 * 0.1 microseconds or 204.8 microseconds.
Question5
Key management issues, practical implications, and general encryption method vulnerability are the main WEP of 802.11 networking flaws. Although WEP may make it more difficult for attackers, it offers no actual protection from a dedicated intruder.
The other concern is the lack of physical barriers, which makes wireless LANs more vulnerable. These are vulnerable to all known attacks on wired LANS, including espionage, jamming, intrusion, and many others.
The original remote monitoring standard (WEP) has security issues resolved by WPA due to TKIP encryption, which is superior to WEP’s fixed-key encrypted communications and a 256-bit encrypted message.
Question6
A collection of protocols known as IPsec are used to establish secure communications among machines. Data exchanged across open networks is kept safer, thanks to it. VPNs are frequently set up using IPsec, which operates by encryption Internet protocol and verifying the source of the transmissions. The inner IP data packet is shielded against tampering, eavesdropping, information gathering, and eavesdropping by multiple layers of encrypted communications.
However, the five steps which should be followed to achieve this include the following:
- Step 1: Fascinating traffic commences the IPSec process—Interesting communication is determined whenever the IKE procedure is launched by the Internet standard policy set in the IPSec peers.
- Step 2: Complete IKE phase one. Throughout this step, IKE negotiates IKE SAs and authorizes IPSec peers to establish a secure negotiation channel for negotiation with IPSec SAs during phase 2.
- IKE needs to negotiate IPSec SA specifications in step 3 and creates complementary IPSec SAs in the peers.
- The IPSec settings and keys kept in the SA databases are used to move information among IPSec peers in Step 4.
- Step 5: Suspension of the IPSec tunnel—IPSec SAs are deleted or time out.
Question7
Whenever a mobile node is connected to its home network, its IP address serves as its permanent address. Whenever a device visits a neighbouring network, it receives a care-of-address. The foreign entity is the one who assigns the COA. (This may be the mobile nodes or the destination node’s edge gateway.)
Question8
- Application using outdated and unpatched technology – Using a computer system or software application that software engineers no longer maintain implies that neither fixes nor upgrades will be released to areas that need improvement. To lower your risk, it’s crucial to always upgrade to the most recent editions and run network vulnerability analysis (or have a network management security provider conduct these regular businesses).
- Poor Password protection – By employing weaker or common passwords on an internal software package and web apps, you risk a security breach. Simple credentials are generally simple for malware attacks to decipher or for hackers to obtain, like the standard selection “password” and the company name. They ensured that the credentials one or their team used were also secure.
- Solitary Strong Authentication – Single-step verification is the practice of logging access programs, a program, or a file with just one password. Possessing only one level of defence makes it simple to get past, even after addressing the above issue with weak passwords. To increase your privacy, we advise switching to a multi-factor authentication strategy. An unauthorized person can’t obtain access using a secure password, supplemented by secondary means, like a texting password, secret questions, or a biometric scan.
Question9
Asymmetric encryption, often referred to as cryptography and public-key encrypted communications, utilizes statistically connected public- and private-key combinations that encode and decode confidential material between senders and receivers as opposed to symmetric key encryption, which operates the very same private key for both operations.
Question10
- False- An IP address is contained inside the actual frame employed by a network when it is transferred across that connection. This Ethernet frame may be seen to have an IP packet inside of it.
- True- A standard internet typically provides all hosts to receive a transmission sent by one host. It uses the CSMA/CD operating system. The term “collision domain” refers to a group of hosts fighting for the same connexion. MAC has been its protocols. Each produced adaptor seems to have a 48-bit HEX identifier that is specific to it. Ip Packet Format: Type-Demultiplexing Secret, Source and Pathname Ethernet Address, Repetitive Format of 0s and 1s, Body Cargo (minimum 46 bytes and maximum 1500 bytes) 802.11 still uses that were, has complicated broadcast domain, operates via CSMA/CA, and uses an enhanced MAC protocol without slot restriction. Prologue, PLCP header, and MAC PDU make up the 802.11 fame protocol (34-2346).
THE LAB ASSIGNMENT
Question1
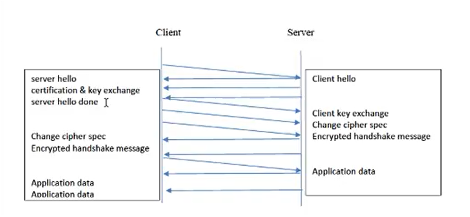
| Frame | Source | SSL Count | SSL Type |
| 106 | Client | 1 | Client Hello |
| 108 | Server | 1 | Server Hello |
| 111 | Server | 2 | Certificate
Server Hello Done |
| 112 | Client | 3 | Client Key Exchange Change Cipher Spec Encrypted Handshake Message |
| 113 | Server | 2 | Change Cipher Spec Encrypted Handshake Message |
| 114 | Client | 1 | Application Data |
| 122 | Server | 1 | Application Data |
| 127 | Server | 1 | Application Data |
Question2
Content Type = 1 byte
Version = 2 bytes
Size or length = 2 bytes
Question3
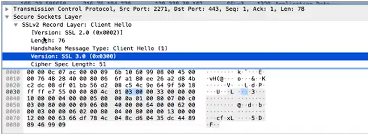
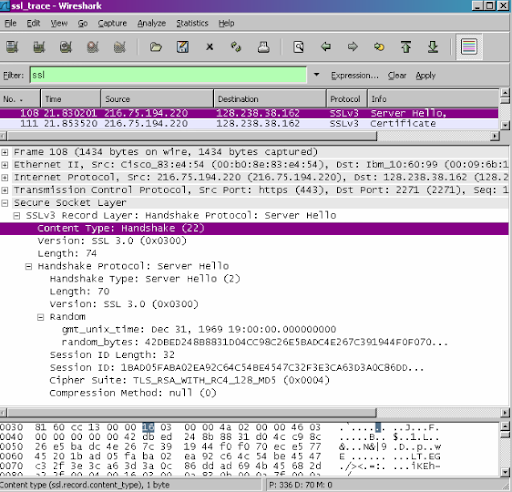
It is clear that the classification result again for the handshake message, which is 22, is 22. The client hello record’s interaction type inside the capture is 01, according to the image.
Question4
The problem sent by the client hello is as continues to follow: 66df 784c 048c d604 35dc 4489 8946 9909.
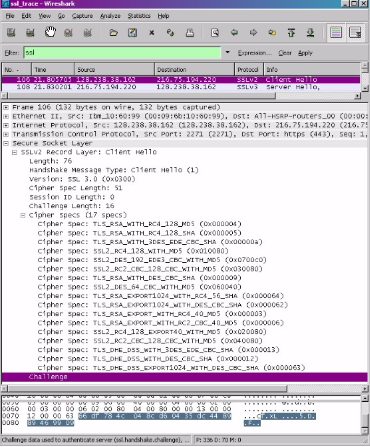
Question5
The primary suite incorporates the MD5 hash computation, RC4 for the symmetric-key calculation, and RSA for entrance control encryption.
Question6
The cypher package includes the RC4 symmetric-key cypher, RSA for open key cryptography, and the MD5 hash function.
Question7
Yes, a sequence number registered beneath Randomized exists present in this record. In the nonce, 32 bits total—28 for information and 4 for time. The goal is to continue the retransmission.
Question8
Yes, indeed, it does. It provides the SSL session, which is supplied for free, with a unique persistent identifier. By using the session ID provided by the server whenever it receives the ClientHello, the customer can resume the very same session later.
Question9
No, there isn’t a certification included in this file. These individual records include the certificate. A standard Ethernet frame did fit the accreditation. The information is contained in another document. It can be controlled in a single Ethernet outline.
Question10
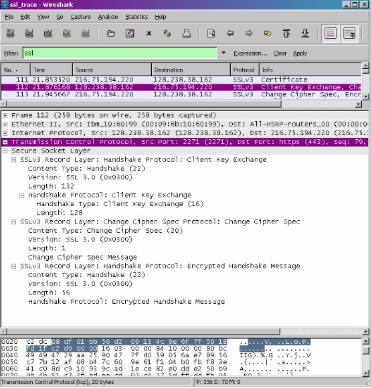
A consists secret is contained in the client key. It is used to construct expert mysteries used by both the server and the client to generate shared keys enabling MAC and encryption. The server’s accessible secret, which even the client extracted from the server’s authorization, is used to encrypt its mystery. One hundred twenty-eight bytes make up the mystery.
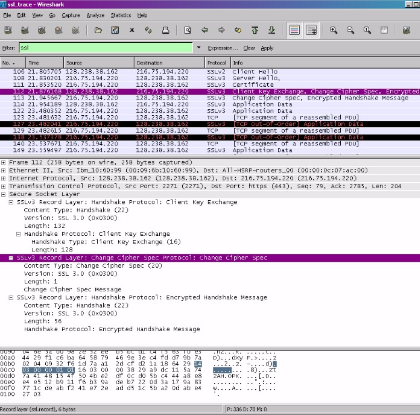
Question11
The Changing Cipher Spec record’s purpose is to show that the body—not the header—of the following SSL recordings supplied by the client will be encrypted. Every title of this record is 5 bytes long, and the message part comprises 1 byte long.
Question12
All previous handshake communications supplied by this client are produced into a MAC of relationship and forwarded to the server.
Question13
Yes, because the server will also transmit an encrypted handshake and a Change Cipher Spec information to the client. The encrypted handshake recording supplied by the server differs from that sent by the client because it includes the links to all the greeting information conveyed from the server rather than the customer. Typically, the data might turn out to be identical.
We can conclude that all the handshake information conveyed by the server is included in the encryption handshake. Other includes messages that clients have sent.
Question14
Applications information is encrypted to use the symmetric encryption algorithm (RC4) chosen during the handshake step, which uses keys made and utilized by the pre-expert key and nonces from both client and the server. Technologies that allow the client to the server are encrypted using the client encryption method, and data transmitted from the server to the client is encrypted using the server encryption algorithm.
The application’s data is encrypted using the symmetric encryption technique. A MAC is present in the records that carry application data. No, Wireshark didn’t distinguish between MAC and the encrypted application programs.
Question15
Since everything functions as intended, I have no more comments on this.

Stuck with your Quiz?
Get in touch with one of our experts for instant help!
Tags:

Time is precious
don’t waste it!
writing help!


Plagiarism-free
guarantee

Privacy
guarantee

Secure
checkout

Money back
guarantee