 All papers examples
All papers examples
Disciplines

- MLA
- APA
- Master's
- Undergraduate
- High School
- PhD
- Harvard
- Biology
- Art
- Drama
- Movies
- Theatre
- Painting
- Music
- Architecture
- Dance
- Design
- History
- American History
- Asian History
- Literature
- Antique Literature
- American Literature
- Asian Literature
- Classic English Literature
- World Literature
- Creative Writing
- English
- Linguistics
- Law
- Criminal Justice
- Legal Issues
- Ethics
- Philosophy
- Religion
- Theology
- Anthropology
- Archaeology
- Economics
- Tourism
- Political Science
- World Affairs
- Psychology
- Sociology
- African-American Studies
- East European Studies
- Latin-American Studies
- Native-American Studies
- West European Studies
- Family and Consumer Science
- Social Issues
- Women and Gender Studies
- Social Work
- Natural Sciences
- Anatomy
- Zoology
- Ecology
- Chemistry
- Pharmacology
- Earth science
- Geography
- Geology
- Astronomy
- Physics
- Agriculture
- Agricultural Studies
- Computer Science
- Internet
- IT Management
- Web Design
- Mathematics
- Business
- Accounting
- Finance
- Investments
- Logistics
- Trade
- Management
- Marketing
- Engineering and Technology
- Engineering
- Technology
- Aeronautics
- Aviation
- Medicine and Health
- Alternative Medicine
- Healthcare
- Nursing
- Nutrition
- Communications and Media
- Advertising
- Communication Strategies
- Journalism
- Public Relations
- Education
- Educational Theories
- Pedagogy
- Teacher's Career
- Statistics
- Chicago/Turabian
- Nature
- Company Analysis
- Sport
- Paintings
- E-commerce
- Holocaust
- Education Theories
- Fashion
- Shakespeare
- Canadian Studies
- Science
- Food Safety
- Relation of Global Warming and Extreme Weather Condition
Paper Types

- Movie Review
- Essay
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- GCSE Coursework
- Grant Proposal
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- Essay
- GCSE Coursework
- Grant Proposal
- Interview
- Lab Report
- Literature Review
- Marketing Plan
- Math Problem
- Movie Analysis
- Movie Review
- Multiple Choice Quiz
- Online Quiz
- Outline
- Personal Statement
- Poem
- Power Point Presentation
- Power Point Presentation With Speaker Notes
- Questionnaire
- Quiz
- Reaction Paper
- Research Paper
- Research Proposal
- Resume
- Speech
- Statistics problem
- SWOT analysis
- Term Paper
- Thesis Paper
- Accounting
- Advertising
- Aeronautics
- African-American Studies
- Agricultural Studies
- Agriculture
- Alternative Medicine
- American History
- American Literature
- Anatomy
- Anthropology
- Antique Literature
- APA
- Archaeology
- Architecture
- Art
- Asian History
- Asian Literature
- Astronomy
- Aviation
- Biology
- Business
- Canadian Studies
- Chemistry
- Chicago/Turabian
- Classic English Literature
- Communication Strategies
- Communications and Media
- Company Analysis
- Computer Science
- Creative Writing
- Criminal Justice
- Dance
- Design
- Drama
- E-commerce
- Earth science
- East European Studies
- Ecology
- Economics
- Education
- Education Theories
- Educational Theories
- Engineering
- Engineering and Technology
- English
- Ethics
- Family and Consumer Science
- Fashion
- Finance
- Food Safety
- Geography
- Geology
- Harvard
- Healthcare
- High School
- History
- Holocaust
- Internet
- Investments
- IT Management
- Journalism
- Latin-American Studies
- Law
- Legal Issues
- Linguistics
- Literature
- Logistics
- Management
- Marketing
- Master's
- Mathematics
- Medicine and Health
- MLA
- Movies
- Music
- Native-American Studies
- Natural Sciences
- Nature
- Nursing
- Nutrition
- Painting
- Paintings
- Pedagogy
- Pharmacology
- PhD
- Philosophy
- Physics
- Political Science
- Psychology
- Public Relations
- Relation of Global Warming and Extreme Weather Condition
- Religion
- Science
- Shakespeare
- Social Issues
- Social Work
- Sociology
- Sport
- Statistics
- Teacher's Career
- Technology
- Theatre
- Theology
- Tourism
- Trade
- Undergraduate
- Web Design
- West European Studies
- Women and Gender Studies
- World Affairs
- World Literature
- Zoology
Troubleshooting Methodologies, Research Paper Example
Hire a Writer for Custom Research Paper
Use 10% Off Discount: "custom10" in 1 Click 👇
You are free to use it as an inspiration or a source for your own work.

Technical Guide
This technical guide will provide a professional exposure for facilitating the Superior financial analysts. We will demonstrate the capabilities of the tools for resolving major incidents that occurs on the network.
Internetwork Performance Monitor
The IPM is an integrated module in the Cisco tool that will facilitate the analyst to monitor the activity of networks configured on multiprotocol. SSID will be utilized for identifying unique services on the network. Likewise, the tool also ensures that the response time and accessibility of IP based network on a router to router basis. Moreover, it also calculates the response from one router to another along with the mainframe that exists in the System Network Architecture (SNA) based networks. Analysts can use the IPM to troubleshoot and perform the following activities:
- Troubleshooting of issues by identifying the latency involving devices configured on the network
- Utilizing the Simple Network Management Protocol (SNMP) alerts whenever a defined and configured threshold is excessive. Moreover, alerts can also be generated on establishing, re-establishing and timeouts on a connection. Furthermore, Intrusion Detection Systems will also utilize SNMP for alert generation.
- Identifying probable issues prior to their occurrence via accumulating statistics that are utilized for modeling and predicting network topologies for the upcoming expectations.
- Analysts can also monitor the responses and the time taken between two ends of the network.
If we elaborate the IPM module further, it can be further divided into three components i.e. IPM server, IPM application, Response Time Reporter (RTR) that is the feature of Cisco IOS.
Using the ping Commands
In order to check host reach ability of host and to configure network connectivity, use the ping command is utilized. This ping commands can be raised from both user exec mode and privileged exec mode. Moreover, once you logged in to the router or you are admitted into the server, you are spontaneously in user exec command mode.
At the privileged level the exec commands that are available at the user level are a subset. Similarly, the user exec commands allows you to perform different functions such as
- Connection to remote devices.
- Change in terminal settings for temporary period.
- Execution of simple tests.
- Collecting system information.
On AppleTalk, The ping command is required to endorse basic network connectivity. This also includes ISO Connectionless Network Service (CLNS), IP, Novell, Apollo, VINES, DECnet, or XNS networks. Furthermore, the ping command directs Internet Control Message Protocol (ICMP) Echo messages towards IPs. The Internet protocol that detects errors and delivers information that is significant to IP packet addressing is called as ICMP. Moreover, if any ICMP Echo messages are received by the station it promptly directs an ICMP Echo Reply message back to the main source. In order to determine the IP header options, the extended ping command mode is used. In fact, this permits the router to implement a new broad range of test options. To arrive at the ping extended command mode, you have to enter yes at the extended commands prompt of the ping command.
Using the trace Command
The routes are suggested by the trace user exec command that helps a router’s packets to follow during their travelling towards end points. In addition, this trace restricted exec command enables the IP header options to be identified. Thus, allowing the router to accomplish another wide-ranging test options.
The trace command mechanism works by utilizing the error messages that are generated by routers. These messages are developed when a datagram surpasses its time-to-live (TTL) value. Initially, the probe datagram are directed with a TTL value of 1. For This reason, the first router is removed by the probe datagram and sends back “time exceeded” error messages. Furthermore, the trace command then directs numerous probes and demonstrations are made for each round-trip time. In fact, after each third probe, the TTL is increased by 1. In addition, each and every outgoing packet can attain one or two error messages. The error messages might be “time exceeded” or “port unreachable”. Once the maximum TTL is achieved, the trace command dismisses the destination. Moreover, if the disturbance is occurred by user than the trance sequences escape. In order to use the trace command along with ping than the network performance is accurate under normal circumstances if compared among troubleshooting.
Using Cisco Network Management Tools
In order to implement internetwork, the Cisco suggest CiscoWorks 2000 family of management products that offer design, monitoring, and troubleshooting tools. In fact, below are some internetwork management tools that are convenient for troubleshooting internetwork complications:
- CiscoView provides dynamic monitoring and troubleshooting functions, including a graphical display of Cisco devices, statistics, and comprehensive configuration information.
- Internetwork Performance Monitor (IPM) empowers network engineers to proactively troubleshoot network response times utilizing real-time and historical reports.
- The TrafficDirector RMON application, a remote monitoring tool, enables you to gather data, monitor activity on your network, and find potential problems.
- The VlanDirector switch management application is a management tool that provides an accurate picture of your VLANs.
Cisco View
The vibrant status, statistics and widespread configuration are the core features of Cisco View. These features are utilized for Cisco internetworking procedures such as switches, routers, hubs, concentrators and access servers. In order to demonstrate Cisco devices and color-coding ports, the Cisco view encourages network management. This will enable users to understand necessary information. Below are the lists of functions:
- Graphical displays of Cisco products from a central location, giving network managers a complete view of Cisco products without physically checking each device at remote sites.
- A continuously updated physical view of routers, hubs, switches, or access servers in a network, regardless of physical location.
- Updated real-time monitoring and tracking of key information and data relating to device performance, traffic, and usage, with metrics such as utilization percentage, frames transmitted and received errors, and a variety of other device-specific indicators.
- The capability to modify configurations such as trap, IP route, virtual LAN (VLAN), and bridge configurations.
Performance Problem Review
A testing tool “network sniffer” is used for monitoring remote access communications. If there are flaws and loop holes in the communications process, testers will utilize them as sources for remote access authentication information and other data sent and received by remote access users. Live testing of remote access connections, is performed during off peak hours of the organization to limit potential disruption to employees and the remote access systems. The testing will be conducted with the administrator ID having full permission and right to perform actions and administrative tasks.
Cost
For conducting the RAS testing, a test bed is required. At least two systems are required for the testing process. One system will be the host. The second will be a remote server. Both of the system must have a modem installed. One network access server and telephone switch is required. As far as time is concerned, the testing will continue until there are no errors left. It may take a day or two depending on how many RAS servers are available in the organization.
Installation RAS on a Wireless Router
In order to install a typical RADIUS server on a router, following protocols and services are associated:
- DHCP
- TCP / IP
- TKIP
- SSID
- WPA
- Internet Authentication Service
- DNS
The next step is to demonstrate RADIUS server installation on a wireless router by incorporating the above mentions protocols and services.
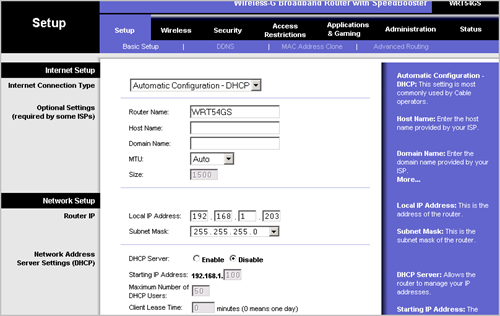
Figure 1.1
As shown in figure 1.1, the first step is to configure the wireless router configuration. These parameters will be considered:
- Internet Connection type: Automatic Configuration
- Router Name: Any
- Host Name: Any
- Domain Name: Any
- MTU: Any
- Local IP Address: Local IP address of the workstation
- DHCP Server: Disabled for RADIUS Configuration
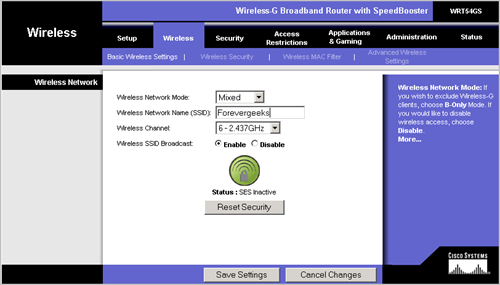
Figure 1.2
As shown in figure 1.2, following parameters will be considered for Basic Wireless network settings:
- Wireless Network Mode: Mixed
- Wireless Network Name (SSID): Type SSID
- Wireless Channel: do not make any changes
- Wireless SSID Broadcast : Enabled
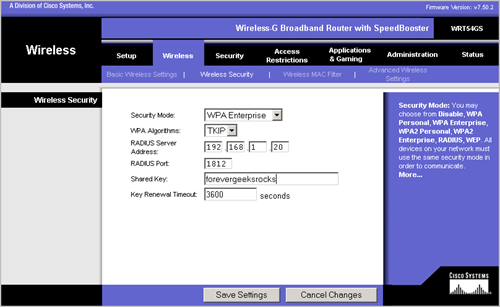
Figure 1.3
Figure 1.3 shows the configuration of the following parameters:
- Security Mode: Select WPA Enterprise
- WPA Algorithms: Select TKIP
- RADIUS Server Address: Configure IP address of the RADIUS server
- RADIUS Port: Set the port to 1812
- Shared-key: Configure the selected shared key
- Key Renewal Timeout: Leave it to default
Figure 1.4
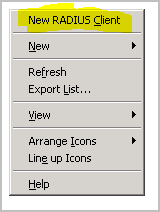
Figure 1.5
As shown in Figure 1.4 and 1.5, Right click on the RADIUS client and click on ‘New RADIUS Client’
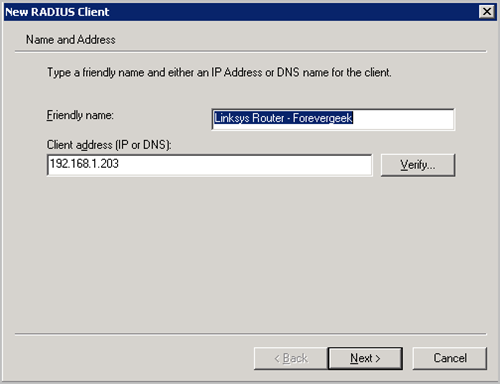
As shown in Fig 1.6, now select name of choice and enter IP address of the Linksys router.
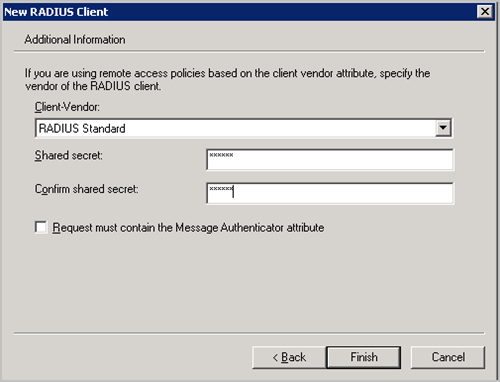
Figure 1.6
As shown in Fig 1.6, the last step will be to set ‘RADIUS standard’ as the ‘Client-Vendor’ and set the shared key that will be identical to the shared key that was configured in the Linksys router. Click finish to end the wizard.
References
Intrusion detection system. (2007). Network Dictionary, , 258-258.
Service set identifier. (2007). Network Dictionary, , 435-435.

Stuck with your Research Paper?
Get in touch with one of our experts for instant help!

Time is precious
don’t waste it!
writing help!


Plagiarism-free
guarantee

Privacy
guarantee

Secure
checkout

Money back
guarantee

