 All papers examples
All papers examples
Disciplines

- MLA
- APA
- Master's
- Undergraduate
- High School
- PhD
- Harvard
- Biology
- Art
- Drama
- Movies
- Theatre
- Painting
- Music
- Architecture
- Dance
- Design
- History
- American History
- Asian History
- Literature
- Antique Literature
- American Literature
- Asian Literature
- Classic English Literature
- World Literature
- Creative Writing
- English
- Linguistics
- Law
- Criminal Justice
- Legal Issues
- Ethics
- Philosophy
- Religion
- Theology
- Anthropology
- Archaeology
- Economics
- Tourism
- Political Science
- World Affairs
- Psychology
- Sociology
- African-American Studies
- East European Studies
- Latin-American Studies
- Native-American Studies
- West European Studies
- Family and Consumer Science
- Social Issues
- Women and Gender Studies
- Social Work
- Natural Sciences
- Anatomy
- Zoology
- Ecology
- Chemistry
- Pharmacology
- Earth science
- Geography
- Geology
- Astronomy
- Physics
- Agriculture
- Agricultural Studies
- Computer Science
- Internet
- IT Management
- Web Design
- Mathematics
- Business
- Accounting
- Finance
- Investments
- Logistics
- Trade
- Management
- Marketing
- Engineering and Technology
- Engineering
- Technology
- Aeronautics
- Aviation
- Medicine and Health
- Alternative Medicine
- Healthcare
- Nursing
- Nutrition
- Communications and Media
- Advertising
- Communication Strategies
- Journalism
- Public Relations
- Education
- Educational Theories
- Pedagogy
- Teacher's Career
- Statistics
- Chicago/Turabian
- Nature
- Company Analysis
- Sport
- Paintings
- E-commerce
- Holocaust
- Education Theories
- Fashion
- Shakespeare
- Canadian Studies
- Science
- Food Safety
- Relation of Global Warming and Extreme Weather Condition
Paper Types

- Movie Review
- Essay
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- GCSE Coursework
- Grant Proposal
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article
- Article Critique
- Article Review
- Article Writing
- Assessment
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Case Study
- Coursework
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- Essay
- GCSE Coursework
- Grant Proposal
- Interview
- Lab Report
- Literature Review
- Marketing Plan
- Math Problem
- Movie Analysis
- Movie Review
- Multiple Choice Quiz
- Online Quiz
- Outline
- Personal Statement
- Poem
- Power Point Presentation
- Power Point Presentation With Speaker Notes
- Questionnaire
- Quiz
- Reaction Paper
- Research Paper
- Research Proposal
- Resume
- Speech
- Statistics problem
- SWOT analysis
- Term Paper
- Thesis Paper
- Accounting
- Advertising
- Aeronautics
- African-American Studies
- Agricultural Studies
- Agriculture
- Alternative Medicine
- American History
- American Literature
- Anatomy
- Anthropology
- Antique Literature
- APA
- Archaeology
- Architecture
- Art
- Asian History
- Asian Literature
- Astronomy
- Aviation
- Biology
- Business
- Canadian Studies
- Chemistry
- Chicago/Turabian
- Classic English Literature
- Communication Strategies
- Communications and Media
- Company Analysis
- Computer Science
- Creative Writing
- Criminal Justice
- Dance
- Design
- Drama
- E-commerce
- Earth science
- East European Studies
- Ecology
- Economics
- Education
- Education Theories
- Educational Theories
- Engineering
- Engineering and Technology
- English
- Ethics
- Family and Consumer Science
- Fashion
- Finance
- Food Safety
- Geography
- Geology
- Harvard
- Healthcare
- High School
- History
- Holocaust
- Internet
- Investments
- IT Management
- Journalism
- Latin-American Studies
- Law
- Legal Issues
- Linguistics
- Literature
- Logistics
- Management
- Marketing
- Master's
- Mathematics
- Medicine and Health
- MLA
- Movies
- Music
- Native-American Studies
- Natural Sciences
- Nature
- Nursing
- Nutrition
- Painting
- Paintings
- Pedagogy
- Pharmacology
- PhD
- Philosophy
- Physics
- Political Science
- Psychology
- Public Relations
- Relation of Global Warming and Extreme Weather Condition
- Religion
- Science
- Shakespeare
- Social Issues
- Social Work
- Sociology
- Sport
- Statistics
- Teacher's Career
- Technology
- Theatre
- Theology
- Tourism
- Trade
- Undergraduate
- Web Design
- West European Studies
- Women and Gender Studies
- World Affairs
- World Literature
- Zoology
Infrastructure and Security Systems Design, Capstone Project Example
Hire a Writer for Custom Capstone Project
Use 10% Off Discount: "custom10" in 1 Click 👇
You are free to use it as an inspiration or a source for your own work.

Project Background
An organization hoping to expand further is expected to take on several conditions of development and adjustments especially when it comes to the information infrastructure that it operates with. Such development is essential as it plays a great role on how the progressive condition of an organization is likely to take place and become successful in achieving the goals set by the group towards embracing the new work culture related to expansion procedures (Donahue, 5). For this particular project, a focus on expanding the infrastructure and security systems design for the information route of an organization is to be given specific attention to. Going from one floor to three-floor operation, the organization is bound to realize conditions of adjustments that could jeopardize the way they handle operations if network stations are not established properly. Given the scenario, a creation of a local network is essential to make sure that the information, vital for the operation of the company, would be passed on effectively through work stations without being jammed nor hacked along the way (Dahl, 134). With expansion goals being set for the company, the business also expects to serve a higher number of clients accordingly; which means bigger bulk and loads of work that needs to be managed among different employees working on the matter (Dahl, 144). Notably, with this in concern, the information infrastructure seriously needs to become stable enough to handle such tasks.
Purpose and Objectives
It is the purpose of this project to equip the company with the proper tools and technological assistance to make sure that it embraces development at a much considerable pace allowing it to become more capable of handling particular instances of pressures from the clients and from the external environment that it is to thrive in (Donahue, 5). With the expectations of larger workloads to be handled, it could not be denied that the need to establish a strong and reliable network is necessary in the process of embracing development. Hence, to note, presented herein are four of the primary objectives that this project is dependent upon:
- To suffice the need of the organization to become more capable of handling pressures especially related to serving client demands coming in at a high rate due to the expansion
- To establish a local area network (LAN) to support the condition by which the organization is supposed to operate
- To make sure that the LAN infrastructure is sufficiently able to perform bulk tasks between workers allowing the employees to perform well with the work assignments they are asked to complete
- To make sure that the LAN infrastructure has sufficient system that supports protection and security operations thus keeping the system away from the possible impact of information theft or any other malicious act from both internal and external users of the system.
Basing from the conditions of the project’s procedures set alongside these objectives, a distinct concern for security and quality operation is given specific attention to. Relatively, these factors or characteristics that define the capacity of an information system infrastructure to handle work and protect the data stored in it for confidentiality shall not only keep the information intact for the organization but would also impose a greater influence on how the workflow of tasks is handled among the employees of the organization even during peak times when the company is expected to work at its best to serve the demands and requirements of the clients that it hopes to serve.
Procedures to Apply
Presented herein are the project schedules that need to be met by the project management team that needs to handle the task of preparing the company’s IT infrastructure for expansion:
Establishing the plan
The planning phase of the project encompasses the need to list down the primary goals of the IT infrastructure that is to be established. Knowing what it needs to accomplish and what it hopes to fulfill once it is already being used makes the creation of the infrastructure more definite and conveniently distinct especially when it comes to distinctively mandating how the operations of the organization shall be directed utilizing the IT systems-network to be created.
Designing the infrastructure
Establishing the architectural design of the infrastructure is one of the most crucial parts of the process. Creating this aspect of the plan includes the need to know how each work station is supposed to work and how it could be connected to the LAN system without interrupting procedures of operation at any time. Smooth transfer of information is necessary for the workstations to work at their best and the employees to perform better (LAN-BC, web). Hence, it could be considered that establishing the architectural design of the LAN system would be a key phase of operation within the overall context of the project management’s documentation of procedures.
Picking the primary points of consideration to set the primary characteristics of the infrastructure
What does the infrastructure need to accomplish? How many users is it supposed to serve at one time? These questions ought to impose on the capacity of the system and how it could be situated within the entire facility to cater to the needs of the employees and the clients they are supposed to serve. Along with this is the consideration over the security system that the infrastructure holds. Encryption and firewalling operations need to be given careful attention to as these elements shall determine the capacity of the LAN infrastructure to protect itself from malicious users (LAN-BC, web).
Test the quality of the infrastructure through trial and error procedures
As the computers are set and the network is already established, it is essential to run a trial and error operation to test the integrity of the infrastructure making sure that it will not crush at the point of being in need to face difficulties allowing it and the employees to handle bulk work with ease.
The Infrastructure’s Architectural Design
The diagram presented in this section entails to create visionary indication on what the IT systems infrastructure is be established upon. The systems used to connect the work stations altogether instantiates a distinct impact on how each station is to be connected to the main server and how the main server would be able to accommodate information flow at a very efficient approach. The entire system is dependent on the desire of being noted alongside particular characteristics that makes it the fitting design for the needs of the company being served :
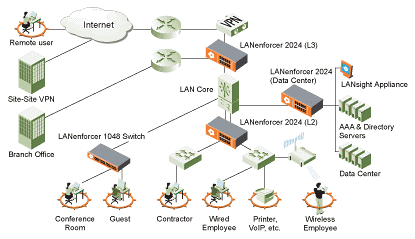
Among the primary characteristics that this system is noted for are as follows:
- Utilizes effective firewall technology that establishes a role-based system that is focused on managing work thus allowing a more efficient process of establishing a composite group policy model which makes workloads easier to manage and delegate among users.
- Instantiates the use of multiple detection procedures that would alert the system operators when scrupulous activities are being done within the network or towards an external operation that comes out from the LAN towards the internet.
- Provides a proactive method of considering authorized-access-only policy especially on confidential sectors that store information that need extreme protection.
- Provides centralized managing system that allows the server operators to see the overall function of the IT system thus allowing for better concept of supervision which protects not only the system but also the function of the organization in the industry and towards its clients.
Conclusion
Basing from the documentation of projection presented herein, it could be analyzed that the primary goals of establishing a local network system that would be able to handle information sharing and operations within the organization is based on two aspects, network protection [security and firewall protocol features] and the need to establish an easy-to-manage work systems supported by the infrastructure. With this in mind, the creation of a LAN system that supports the IT operations of the company would be more definite and more effective in handling the most crucial parts of operation that the company needs to deal with in relation to its goals of expansion.
References
Donahue, Gary A. (2007-06). Network Warrior. O’Reilly. p. 5.
Local Area Network (LAN) Basic Components. (2007). http://networkbits.net/lan-components/local-area-network-lan-basic-components/. (Retrieved on December 17, 2013).
Dahl, OJ. (2003). Structured Programming. Academic Press Ltd.

Stuck with your Capstone Project?
Get in touch with one of our experts for instant help!

Time is precious
don’t waste it!
writing help!


Plagiarism-free
guarantee

Privacy
guarantee

Secure
checkout

Money back
guarantee

